Naming conventions
Patterns as operational constructs.

Naming conventions, why is it critical?
There are a lot of questions to answer:
📚 Information data is describing?
⚙ Relationships data elements?
🎭 Who is using data for what proces?
⚖ Inventory information being used ?
🔰 Somewhere in a loop of patterns ..
Most logical back reference:
previous.
Contents
| Reference | Topic | Squad |
| Intro | Patterns as operational constructs. | 01.01 |
| Foundation | Why doing naming conventions. | 02.01 |
| Technical LC | Technical & tools Life cycle. | 03.01 |
| assembly line | Business Process assembly line sequence. | 04.01 |
| artefacts | Logical Artefacts. | 05.01 |
| Pattern chain | Defining the chain - Transformations. | 06.00 |
| | Dependencies other patterns | 06.02 |
Progress
- 2020 week:01
- Moved naming convetions to a dedicated page.
It is a common prereq for simplified soltution approaches.
Duality service requests

sdlc: Naming conventions with de DTAP (life cycle) is fundamental good governance.
bianl: The information in the DTAP (life cycle) is a source to use analysing processes.
When additional measurements are needed they are to new requirements.

Why doing naming conventions.
There are several reasons:
- Understanding of the organisation as issue.
Naming conventions is the language solving that.
- Having a well defined naming convention in place, technical realisations can use that.
This will avoid the tremendous complexity when trying to solve the underlaying questions in another way.
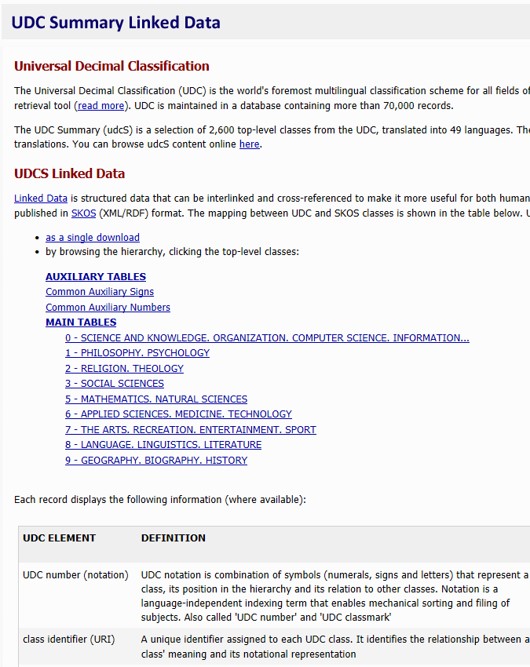
Proposal idea duplication, library classification scheme
udcdata is one of classification schemes.
The UDC is the world's foremost multilingual classification scheme for all fields of knowledge and a sophisticated indexing and retrieval tool. It is a highly flexible classification system for all kinds of information in any medium.
Because of its logical hierarchical arrangement and analytico-synthetic nature, it is suitable for physical organization of collections as well as document browsing and searching.

Technical & tools Life cycle.
The goals are preparing all those technical resources at the infrastructure level for the tooling´s (applications) with their administration and the business (applications) with another administration type.
This starts with the administrative agreements and follow up in low level technical tier.
The resulting environment of the technical aspects is for tier-1 administration. The follow up are the business aspects.
Storage & monitoring.
Technical naming´s (IAAS PAAS):
- file systems - drive letters - First level qualifier.
- Storage performance tiers with their configuration settings.
- CPU & internal memory constraints for deleviering perforamance.
- Central Monitoring & logging identification, configuration.
- CIA levels as of BIA ratings with resulting needed segregations.
There is no visible business naming conventions for this.
The used naming conventions get a direction by those that are delivering these infrastructure resources.
Machines & Tools for research & development.
There is no visible business naming conventions for this.
The needed naming conventions get a direction by logical machine naming´s.
Business process development.
1
📚 <idtapz-C>/ one letter -
- I - Initial & research
- D - Development
- T - Test validation technical
- A - Test acceptance usability
- P - Production Operational
- Z – out of service – archive
Two stages added to normal DTAP
Remarks:
- I - is having mostly only documentation artefacts.
Possible are some POC (Proof of Concept) codes.
- A - Not only for user acceptance testing but also human educational lines.
- In those cases the parallel identification should make clear the details differentiations.
Business process identification.
2
📚 B<process_id-NNN>/ The letter B followed by three digits.
The logical name is often changed in time although the process is the same. The logical name should be found as documentation artefact

Business Process assembly sequence.
The technical area is having at least two administrative tiers.
-
⚙ Those tiers are:
- -0- Hard core components
machines, storage, the operating system.
the root level is associated with number 0.
- -1- Middleware applications
databases, ESB FTP, BI tools.
there are more of them interacting at one machine.
Every business process is having several steps in their proceeding. It is like an assembly line with stations and workers.
The business area is adding more administratitieve tiers.
-
⚙ Those tiers are:
- -2- Business application administration for the business users.
- -3- Optimisation with analytics
what is going in at business processes in the assembly lines.
paralellel line non operational
3
📚 L<process_id-*>_
At develop and test there can multiple lines active at the the same moment. The real operational production doesn&actut have that. I that real operatonal this is left empty / blank.
Classification System ICT artefacts
4
📚 <process_proceeding-N> One number (character)
- 0 – Input External, not validated consistent
- 1 – Input Internals validated consistent
- 2 – Split sub flows (map)
- 3 – data preparations
- 4 – Logic processing
- 5 – Combine Results (reduce)
- 6 – Preparations of results
- 7 – Logical monitoring results - data
- 8 – Technical monitoring processing data
- 9 – Output deliveries (internal / external)
All steps are applicable to any system although might be empty in cases.
Remarks:
- Proceeding 9 is used with technical administrator overwrite. Goal is to manage the logical segmentation requirements.
- Proceeding 9 External delivery can be of any type. A direct DBMS interface, file transfer or micor service.
- Proceeding 8 is an operational connection for segregation of duties.
- Proceeding 0 an external input source for data is requiring strict input validation.

Logial Artefactcs.
The logical artifacst within a process proceeding can have many types of techncial realisstions.
Sometimes the can stored in the same storage type, sometimes the naming convention in different storage types is the only way of the strong association.
Classification System ICT artefacts
Artifacts (shared - subfolders)
5
📚 <artifact type-Cccc>/
- Fdoc - Functional descriptions
- Vmdl – Process reporting
- Csrc - Code Sources (src devops)
- Cexe - Code Executables (src devops)
- Ldta – data content and lineage (data)
- Lmta – metadata data lineage (data)
- Uadm – administrative overwrites
- Tmap - Test validation reports
- Sbac - Security Access rules
- Hedu - Human education usage
- Hrsp – Human responsibilities
- Mrls - Maintenance & changes
Not all types of artifacts need to be present in every business level of proceeding
unique business application proces lines
6
📚 <%*>
An unique name for this artefact within the context type.
Different artifacts that are strongly related can use the same name. Eg a word document and the PDF version having the same name. The documentation for some code er data elemement can share the same nam in a similar way.

Underpinning the technical dependicies.
The usage of the process-proceeding is not required with simple processes.
When going vor Machine lerarning Application Life Cyce type 3 (ALC-v3), then there a many parties with different type of duties getting involved.
The segregation of duties requirement is resulting in many different autorisation settings in the same value stream of the process.
Having the artefacts segregated at process flow steps:
- this detailed autorisation can be managed.
- The release management is more clear in responsablities and impact.

Defining the chain - Transformations.
Pattern: Naming convention & managing hierarchy
The levels ordered:
- <idtapz-C>/
- B<process_id-NNN>/
- <parallel_id-L*>_
- <process_proceeding-N>/
- <artifact type-Cccc>/
- %*
A long combined string to use:
<C>/B<NNN>_<N>/L<*>_<Cccc>/%*
Remarks:
- A level like “/” might be left away when forced in an other way.
- Bringing artifacts together simplifies versioning and releases. The approach will be container based release not artifacts based
- C is a placeholder for a character
- N is a placeholder for a number. The logical process identification might get different logical names in time
- %* is a free to choose name for the artifacts
Conflicting other Patterns.
This naming pattern is a logical construct. In the realisation there are also physical properties to evaluate and choose options.
When the CIA, Confidentiality Integrity Availability requirements for all artefacts are the same, storing everything in the same physical structure is an option.
With different sizing of code (sources) and data (information) and different performance requirements (io throughput) and different availability (backup restore DR) the physical placing is different as of the logical naming.
💡 A solution for this is using logical links so both requirements are acknowledged.
⚠ knowing the physical naming´s a tendency is to neglect the logical pattern.
Dependicies other patterns

This page is a pattern on naming conventions.
Within the scope of metadata there are more patterns like exchaning information (data) , building private metadata and securing a complete environment.
🔰 Somewhere in a loop of patterns ..
Most logical back reference:
previous.
 Naming conventions, why is it critical?
Naming conventions, why is it critical? sdlc: Naming conventions with de DTAP (life cycle) is fundamental good governance.
sdlc: Naming conventions with de DTAP (life cycle) is fundamental good governance. 





