
Realizations Shape Organisations
U-1 Basics Understanding and Improving Services
U-1.1 Contents
⚙ U-1.1.1 Global content

The world of BI and Analytics is challenging.
It is not the long-used methodology of producing reports.
A lot needs to get solved:
❶ ⚙ Operational Lean processing, design thinking
❷ 📚 doing the right things, organisation & public.
❸ 🎭 help in underpinning decisions boardroom usage.
❹ ⚖ Being in control, being compliant in missions.
It is about shaping change.
When wanting going logical backward:
🔰 Too fast ..
previous.
⚖ U-1.1.2 Guide reading this page
This page is about Optimizing. The scope for services processes routines while all kind of uncertainties are included for sensible decisions.
When a holistic approach for organisational missions and organisational improvements is wanted, starting with services covered by missions extracted from visions is the pathway.
Knowing what is going on on the shop-floor (Gemba).
👁 💡 Working into an approach for optimized services, there is a gap in knowledge and support by tools.
The proposal to solve support by tooling is "Jabes".
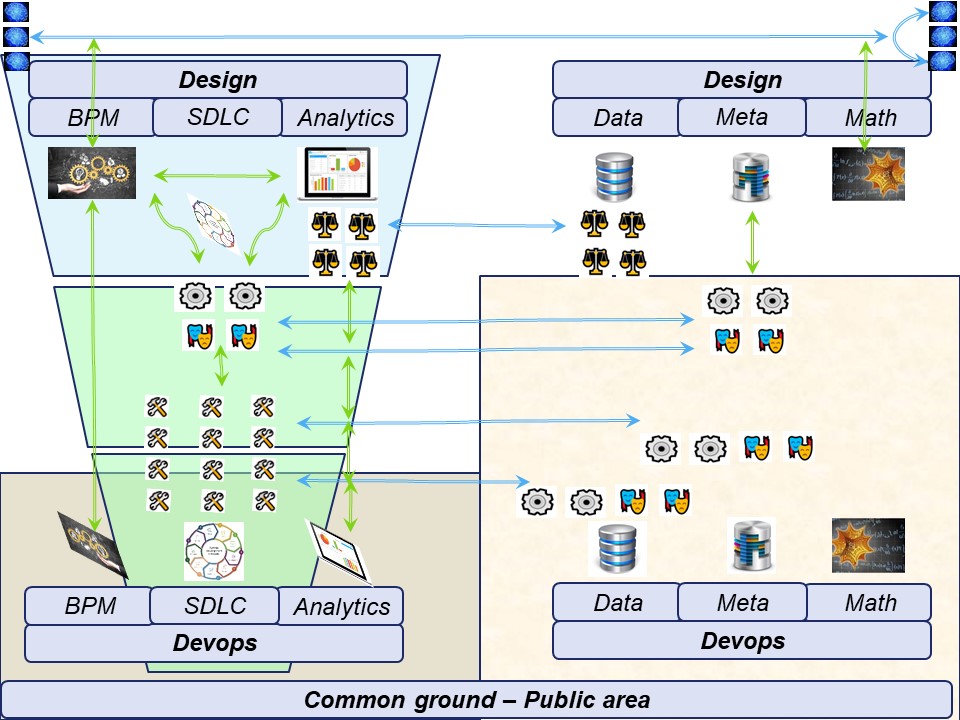
⚒ Three Pillars as an organizational structure
The organisation powered by technology in a ship like constellation.
The engines (data centre) out of sight below visibility.
Serving multiple customers (multi tenancy) for the best performance and the best profits on all layers.
There are six pillars diveded over a functional and technical layer.
A futuristic vision is a positive attitude but can easily become negative when too far from reality.
The three internal lines:
- Information (Business, Missions Visions, Information, BPM),
- Technology (Operations SDLC),
- Communication (Advisory, Analytics decision support)

Practising knowledge on technology
The positive approach for organisational issues:
- Reuse existing commodity knowledge wisely
- Reuse existing portfolio knowledgegement
- Look for improvements with options in the commodity market
- Avoid the known loopholes
Although the positive approach is the one that is needed for achieving results & goals, the threats and challenges are also needed to know so the can get solved or bypassed.
The gap Business - ICT is well known. The gap business strategy -theory vs running operations is overlooked.
Trying to connect the C-Shape to r-shape for what how why to do, the vertical lines are found broken.
The difference is that C-shape is based on visions by processes, technoloyg.
The r-shape switched for services, processes activities and avoiding the how in technology, the who by names.
The gaps found to solve for an profound working environment in the the C-Steer C-Shape C-Serve are hampering the situation at this practical content.
These are in the U-*.6 references a starting point not a desired end situation.
Needed knowledge to read this
Basic knowledge:
- Logic of Information processing for an organisation.
- Basic understanding of computeres and their ICT technology.
- Understanding what the impact of changing services can be.
This page is the realisation area, there are refences to Jabes for enabling work.
⚙ U-1.1.3 Local content
| Reference | Squad | Abbrevation |
| U-1 Basics Undertanding and Improving Services | |
| U-1.1 Contents | contents | Contents |
| U-1.1.1 Global content | |
| U-1.1.2 Guide reading this page | |
| U-1.1.3 Local content | |
| U-1.1.4 Progress | |
| U-1.2 How to improve services? | innbase_02 | Inside |
| U-1.2.1 Floor Impediments - Gemba People | |
| U-1.2.2 Business services processes Administrative/cyber | |
| U-1.2.3 A functional tasks & actions floorplan, external | |
| U-1.3 Methodologies for improvements | innbase_03 | Outside |
| U-1.3.1 Floor Impediments Gemba - process | |
| U-1.3.2 Understanding services "cyber administrative" | |
| U-1.3.3 A functional tasks & actions floorplan, internal | |
| U-1.4 Operational Service Improvements | innbase_04 | ValOSI |
| U-1.4.1 The value for the Customer, Requestor, Data subject | |
| U-1.4.2 Administrative cyberworld Information as a product | |
| U-1.4.3 A safe environment for cyberworld information | |
| U-1.5 Shape: Manage Information Services | innbase_05 | DO USM |
| U-1.5.1 ITIL: service management technology driven | |
| U-1.5.2 Simplify USM: using words, lean agile | |
| U-1.5.3 Cleaned up USM principles | |
| U-1.6 Maturity 3: fundaments Services | innbase_06 | CMM3-4FS |
| U-1.6.1 The goal & maturity of the internal organisation | |
| U-1.6.2 The goal & maturity of the organisation servicing external | |
| U-1.6.3 Result: Value creation for Customer, Requestor, Data subject | |
| U-1.6.4 Safety: Capabilities for managing uncertainties & risks | |
| U-1.6.5 The goal & maturity of the organisation as service provider | |
| U-1.6.6 Short checklist organisational impediments | |
| U-2 Ideate Improving value streams, reducings risks | |
| U-2.1 Safety - Access Management processes | innline_01 | TIP Risk |
| U-2.2.1 Central management: names, gid id LDAP, AD | |
| U-2.2.2 Security processes - Identities access | |
| U-2.2.3 A Safe environment quest (I) | |
| U-2.2.3 A Safe environment quest (II) | |
| U-2.2 Processes internal partially solving services | innline_02 | Genba |
| U-2.2.1 Positive wanted functionality & negative ones with their impact | |
| U-2.2.2 Protection of materials for wanted and unwanted functionality | |
| U-2.2.3 Transforming of materials into new ones defined by functionality | |
| U-2.2.4 Protecting Transformations, expected and unexpected behaviour | |
| U-2.2.5 Gemba, walking the shop floor, multiple maps | |
| U-2.3 Processes servicing customers, requestors | innline_03 | Service |
| U-2.3.1 The Product | |
| U-2.3.2 The Product Manager | |
| U-2.3.3 The Waterstrider | |
| U-2.3.4 PoLP Principle of Least Privilege | |
| U-2.4 Safety & quality embedded in services | innline_04 | C-Safety |
| U-2.4.1 Safety procedures at an organisation | |
| U-2.4.2 Safety practices at an organisation | |
| U-2.4.3 Risk management principles | |
| U-2.5 Service lines functionality functioning | innline_05 | SMART USM |
| U-2.5.1 Services, processes, practices, instructions | |
| U-2.5.2 facility - support, functionality - functioning | |
| U-2.5.3 The Service quantum | |
| U-2.6 Maturity 4: Change Services in control | innline_06 | CMM4-4OO |
| U-2.6.1 Safety intangible at the internal organisation | |
| U-2.6.2 Clear safe assembly lines, deliveries, by the organisation | |
| U-2.6.3 Product: Value creation for Customer, Requestor, Data subject | |
| U-2.6.4 Safety: Capabilities for managing uncertainties & risks | |
| U-2.6.5 The goal & maturity of the organisation as service provider | |
| U-2.6.6 Short checklist organisational impediments | |
| U-3 Realisations improved value streams, reduced risks | |
| U-3.1 Simple risk information & services | inntdss_01 | 101-RIS |
| U-3.1.1 Dualities: Materialised transforming | |
| U-3.1.2 Inference Statistical - Machine Learning | |
| U-3.1.3 Inference purpose information processing | |
| U-3.2 Interactions in a complicated landscape | inntdss_02 | ComCap |
| U-3.2.1 Perspectives activies in the centre | |
| U-3.2.2 Perspectives activies over axis | |
| U-3.2.3 Walking over floorplan lines | |
| U-3.3 Ideate the purpose for the Enterprise | inntdss_03 | Ideate-EE |
| U-3.3.1 Enterprise Culture vision | |
| U-3.3.2 Culture expectation threats | |
| U-3.3.3 Threats by accountability nature | |
| U-3.4 Evolving technical operational organisations | inntdss_04 | Plan-EE |
| U-3.4.1 From Chaos to Control | |
| U-3.4.2 Service quality versions adding value | |
| U-3.4.3 Data governance, analytics - business intelligence | |
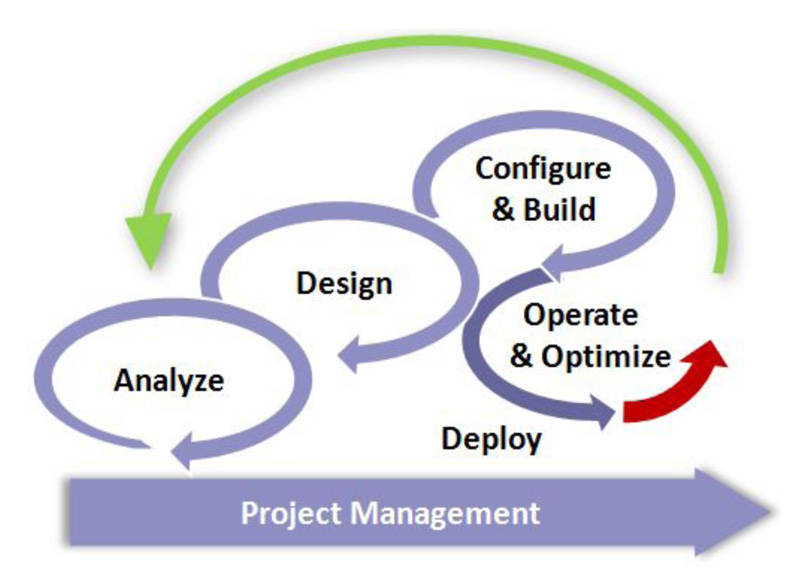
| U-3.5 Realizing optimised lean services | inntdss_05 | EXEC USM |
| U-3.5.1 OPS Serve functioning | |
| U-3.5.2 CTM Shape functionality | |
| U-3.5.3 SMA Steer purpose | |
| U-3.5.4 Maturity Steer Shape Serve | |
| U-3.6 Maturity 5: Controlled Enterprise Changes | inntdss_06 | CMM5-4OO |
| U-3.6.1 Safety: Capabilities for managing uncertainties & risks | |
| U-3.6.2 Interacting communicating becoming an entity | |
| U-3.6.3 The organisation servicing a product | |
| U-3.6.4 The goal & maturity of the internal organisation | |
| U-3.6.5 The goal & maturity of the organisation as service provider | |
| U-3.6.6 Following steps | |
⚒ U-1.1.4 Progress
done and currently working on:
- 2024 week 20
- A quick conversion of r-shape with mostly little old content.
This page was left rather empty in 2020, not really knowing wat the content should be.
- 2024 week 30
- There was no idea how to proceed after analysing concepts for sponsor and jabes usage.
The tipping point was continuing with r-steer (business) including all safety for information.
Security usually is not seen part of the business.
- Continuing in theoretical evaluations (r-know), got an opening for a rebuild r-shape.
- Shop floor & communication (U-*.2) and USM (U-*.5) are the strongholds for what is arround.
- 2024 progress by weekk
- week 31 published first version for chapters U-1.1 - U-1.6
- week 33 published a version for chapters U-2.1 - U-2.6 completed
- week 34 published a version for chapters U-3.1 - U-3.6 completed
What is not included
- OODA: "Observe, Orient, Decide, Act" loop.
It is often applied to understand commercial operations and learning processes. The approach explains how agility can overcome raw power in dealing with human opponents.
There are still initiatives missing in the product-service operational life cycles.
- Details for chained information (history), journals logs.
To solve by technical perspectives, that is another web-page.
U-1.2 How to improve services?
Searching for an understandable workable approach for analysing what is going on.
The quest for improvements is not getting real solutions.
What could be the problem?
- Ambiguity in goals, Complexities for goals
- Uncertainties for accountabilities
- There is no map, no floorplan
A hierachy is not a floorplan.
⚖ U-1.2.1 Floor Impediments - Gemba People
🤔 Shop floor supervisor
The role of shaping work and shaping an organisation requires understanding what is going on.
The way of doing this is promoted by looking at the shop floor, Gemba.
Looking for who is doing and organising the work at the shop-floor.
To do this we will have to find:
- production lines by all steps how the work is done
- a contact person on the floor able to explain what is going on
- the line manager responsible, accountable for the product
For a physical plant the production line is easy to recognize and locate.
In the cyber administrative world there is no physical location.
The start at seeing the shop floor is fully dependant on finding the coordinator on the shop floor.
💣 It is stated that in the cyber administrative world the floor manger and line manager are eliminated in favour of smart agile solutions.
More likely is that are person doing that kind of work but not described or mentioned in hierarchical schemas.
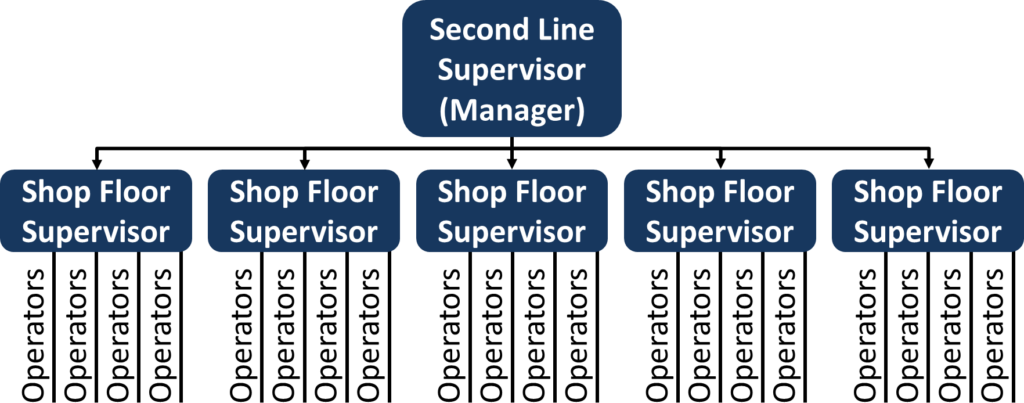
First line, second line supervisors
Reviewing for the cyber/administrative physical equivalent of who is accountable for the value stream flow.
The awareness of value streams is a requirement first to validate to find lines for managing functionality and functioning.
Training Within Industry—Second-Line Supervisor Job Instructions
Training Within Industry and its modules Job Instructions, Job Relations, and Job Methods are well known. ...
Job Instructions for Second-Line Supervisors (nowadays called managers).
This is a hierarchy level higher, and the goal is to support and guide the shop floor supervisors on how to use job instructions.
Physical: Waterstrider, Scrum master, Product owner
The person on the shop floor doing the coordination for the product.
Introduction to Point-of-Use Providers (or Mizusumashi)
The point-of-use provider takes care of the "last mile" (or more precisely last few meters) of the material transport.
This is often for assembly lines, as there is a lot of material arriving.
It should not be impossible to find that person and from there seeing what is going on.
⚙ U.1.2.2 Business services processes Administrative/cyber
🤔 Understanding & manging processes
Searching for who is doing and organising the work at the Shop-floor.
To ingnore are:
- creation of software, unless there is a hint to its usage in a value stream.
- New interesting technology, unless there is a hint to a product line mananger
- What big tech advisors are saying, use this for s
The goal is being good at: knowing and understanding the organisation.
Data driven - process driven
There is strong relationship between two approaches, data-driven, process-driven they can´t exist without the other.
fluxicon disco manual (vdaalst)
Data science is the profession of the future. However, it is not sufficient to focus on data storage and data analysis.
The data scientist also needs to relate data to processes.
At the same time, process analysis professionals need to learn how to incorporate data from the IT systems into their work.
Assumed processes - reality:
When you ask someone about how their process is being performed, or look how it is documented, the structure is typically relatively simple (“First we do X, then, we do Y, etc.”).
However, in reality processes are much more complex.
👉🏾 There is rework: Steps have to be done again, because they were not right the first time.
👉🏾 Exceptions need to made to deal with special situations, different people perform the same process in different ways, and so on.
👉🏾 So, there is a discrepancy between how people assume that processes are performed and how they are actually executed.
... But looking further, this discrepancy is not even the biggest problem.
After all, to a certain extent it can be expected that not everything is always going according to plan.
💣 The much bigger problem is that in most situations nobody has an overview about how the real process looks like in the first place.
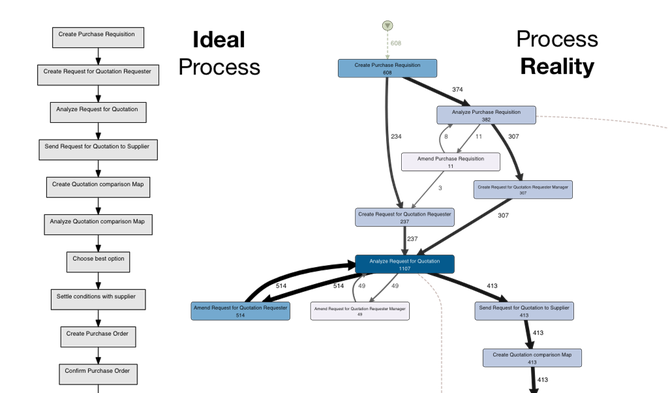
In a figure:
See left side
Why is it so difficult to have an overview about how the processes are actually performed?
- Subjectivity: Everyone has a subjective picture of the process.
- Partial view: Specifically for services, processes there is the additional challenge that there is not one single person that performs the complete process.
- Change: Services, processes change all the time, often while they are being analysed.
- Invisibility through digitization of processes.
In the old times, a pile of paper on the desk was an indication.
Nowadays a customer case can stuck in the system only hearing about it once the customer complains.
⚒ U.1.2.3 A functional tasks & actions floorplan, internal
functionality
Not all information is created equal. For a line there must be at least an ordinal scale.
Ordinals: variables that have a natural order, but no quantifiable difference between values.
Ordinal lines by tasks, activities (left to right):
- Business Visions, missions goals - Business Results success & Risk
- Business Visions, missions goals - Product Assemble. Operations Request/Delivery
- machines operating system, networking - Product Assemble. Operations Request/Delivery
- machines operating system, networking - Business Results success & Risk
Aside these lines other are able to get a description, there are gaps left.
In a figure:
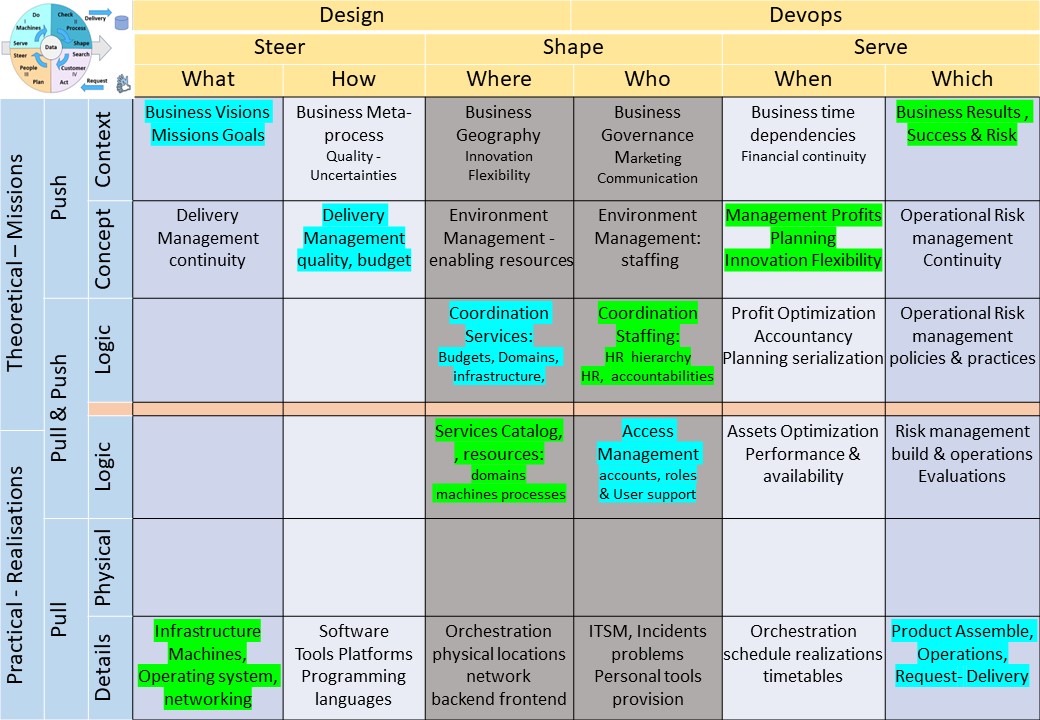
Notes:
👁 The goal for each horizontal line is at the right side (which).
👁 Interactions are only allowed vertical and horizontal not diagonal.
👁 managing design & change is conforming the SIAR cycle (PDCA/DMAIC).
functioning
Ordinal lines by tasks, activities (left to right):
- Business Visions, missions goals - machines operating system, networking -
- Business Visions, missions goals - Product Assemble. Operations Request/Delivery
- Business Results success & Risk - Product Assemble. Operations Request/Delivery
- Business Results success & Risk - machines operating system, networking
In a figure:
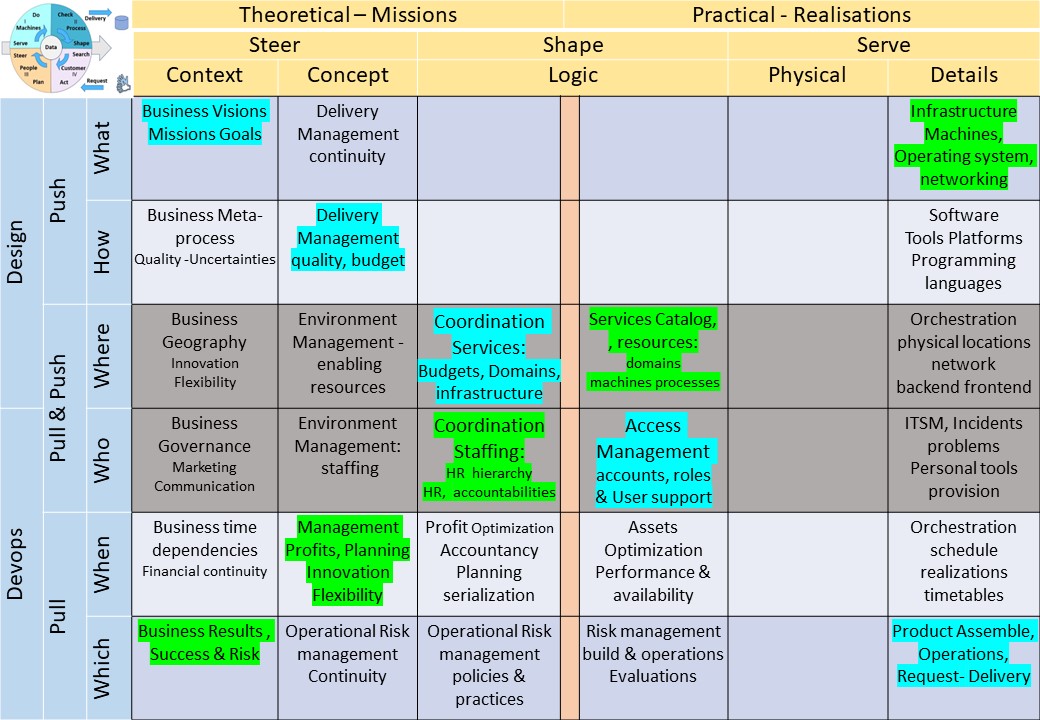
Notes:
🎭 The perspective change to functioning is changing the goals column.
🎭 In the centre there are generic indispensable tasks activities.
⚖ The left open gaps obligations
There are several categories needing a line but are not covered by generic indications.
To get covered by information knowledge by a portfolio:
- Security architecture (technical)
- Operational risk (functional)
- Privacy - impact
- Process - impact
In a figure:
See right side.

U-1.3 Methodologies for improvement.
Searching for an understandable workable approach for analysing what is going on.
The quest for improvements is not getting real solutions.
What could be the problem?
- Ambiguity in goals, Complexities for goals
- Uncertainties for accountabilities
- There is no map, no floorplan
A hierachy is not a floorplan.
⚖ U-1.3.1 Floor Impediments Gemba - process
🤔 Shop floor locations
Going to physcial locations is the first reaction when the questions is: "do a walk at the shop floor".
When doing that you will see persons busy with something but unclear is wat they are really doing.
The shop floor plan only is helping i you can find the person with the usefull wanted information on services activities routines.
In a figure:
🤔 Shop floor, PDCA DMAIC cycles
Instead of being stuck on the floor go for value streams using services routines marked by activities and tasks.
There must be an understandable structure in high level abstraction.
- Nine planes, showing the SIAR model in several levels
- Goal: enabling, running controlled services, processes at (IV)
- Enabling & planning: understanding managing services at (III)
- Designing building validating a service tool/product at (I)
- Delivery of a service product, change in the services for functioning at (II)
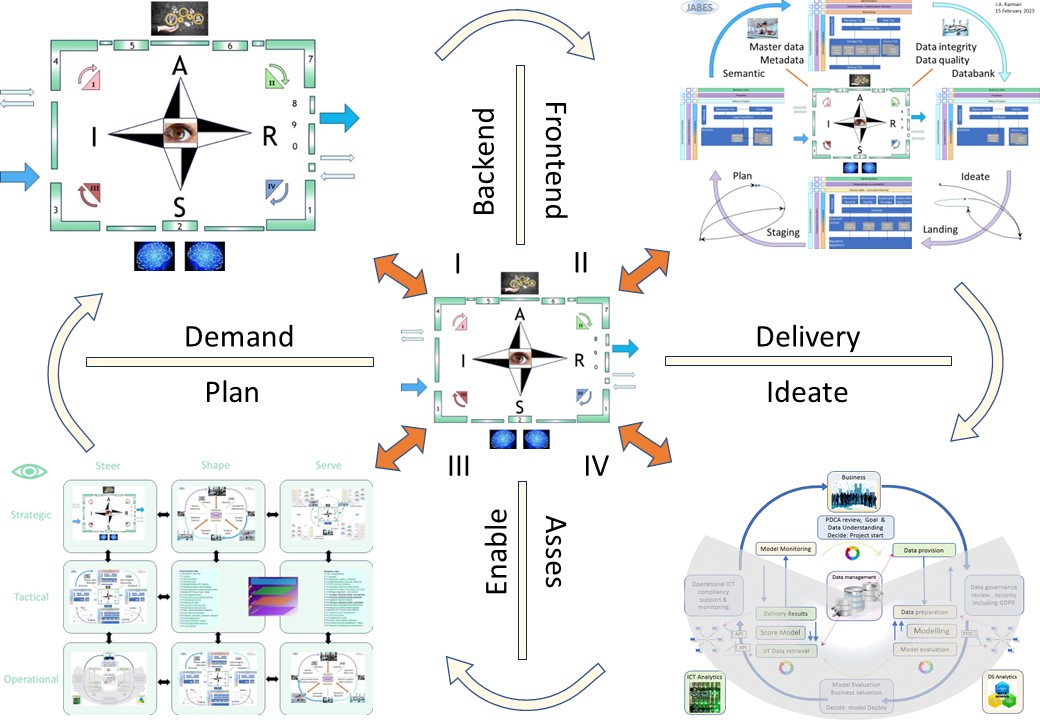 🕳👁❗
🕳👁❗Be open to find people accountable and responible doing tasks activities.
⚒ U-1.3.2 Understanding services "cyber administrative"
🤔 Understanding & cooperating Technology
Looking for who is doing and organising the work at the Shop-floor.
All attention is going to other topics:
- creating software
- New interesting technology
- What big tech advisors are saying
Better being good at is knowing and understanding the own organisation.
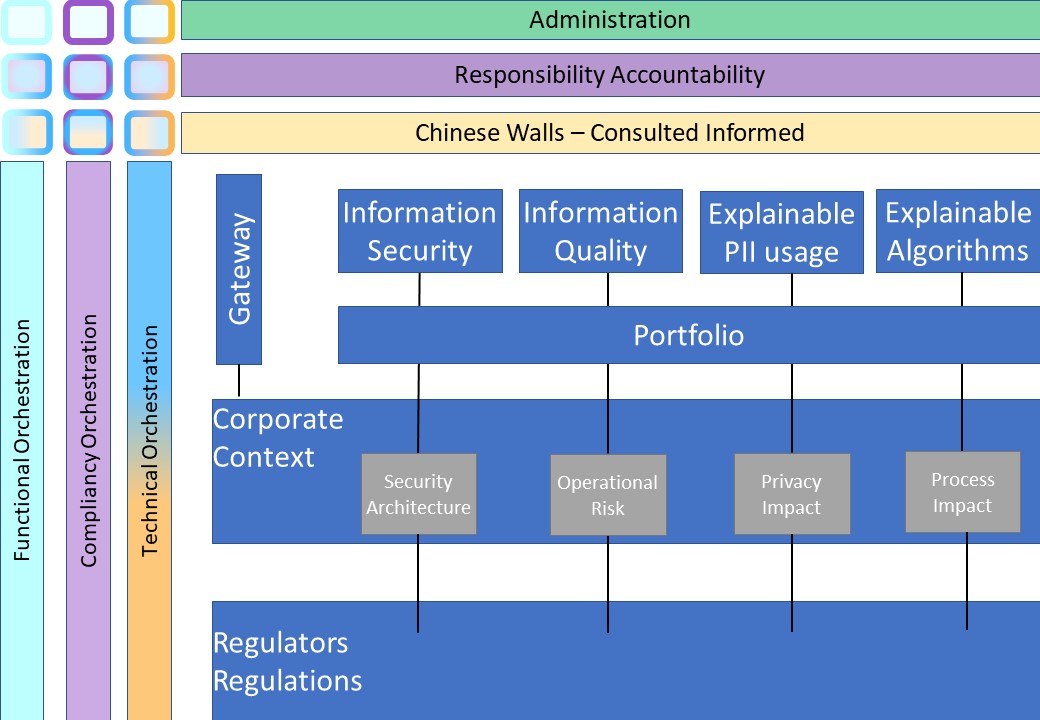
🤔 Context confusing: business - cyber technology
There is a lot of misunderstanding between the normal humans and their cyber counterpart colleagues.
Not that cyber people are not humans but they are using another language, jargon, in communication.
That culture of misunderstandings is not necessary and should be eliminated.
A translation of words to start:
| ICT | Business | | ICT | Business | | ICT | Business |
| Strategy | Control | - | Functional | Target-Value | - | Confidentiality | People |
| Tactical | Orchestration | - | Compliancy | Communication | - | Integrity | Processes |
| Operational | Realization | - | Technical | Information | - | Availability | Machines |
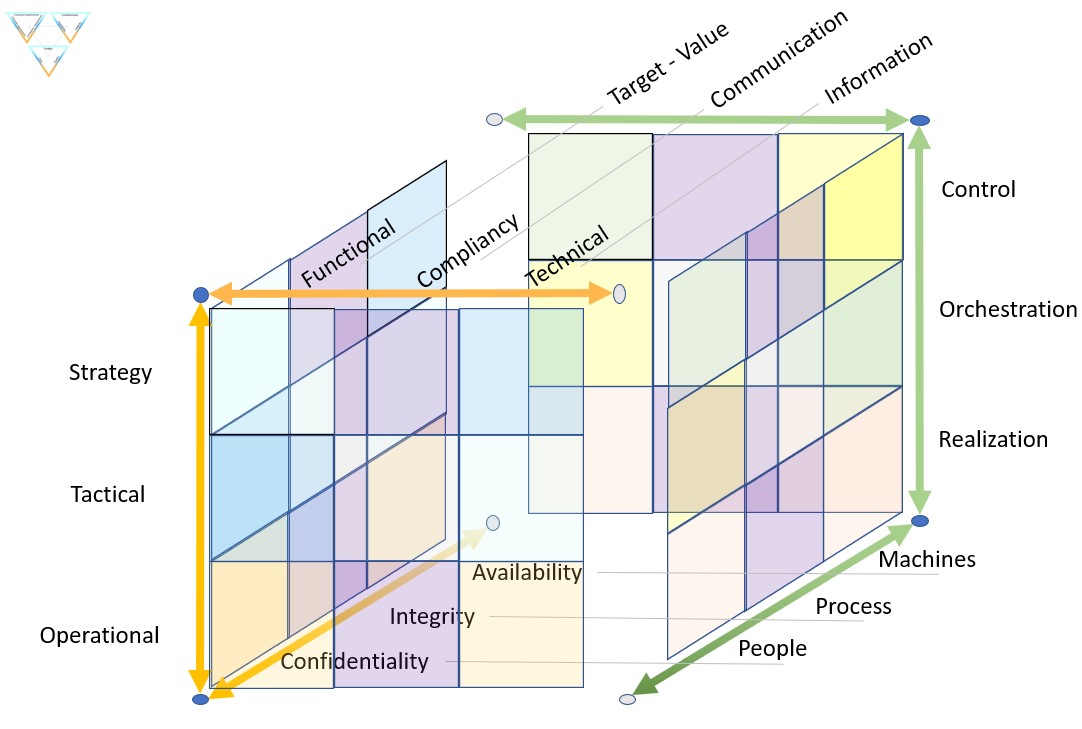
A figure:
See right side
There are several paradigm shifts:
- Leadership: "Strategy, Tactical, Operational" and "Control, Orchestration, Realisation" are both used for justifying hierarchical power.
Although that is a fit, both are incorrect. Hierarchy is just another dimension.
- At the floor: "confidentiality, Integrity,Availablity"
a good fit with: "people, Process, Machines"
- At the roof "functional, Compliancy, Technicality"
a good fit with: "Target - value, Communication, Information"
- Information : the asset "Information" is a business asset not something to be pushed off as incomprehensible "cyber".
Information processing is enabled by technology, technology acting as a service.
- Compliancy : The communication, accoutablity is placed at business context.
What is in demand by risk management considerations, to be deliverd in a service approach.
There focus is on task activies in lines to design / develop and realize / operate a product.
Out of scope are dimensions for:
- Leadership: hierachical lines of power and control.
- Time: In what a product / hierachry: was (paste) is (now) and would be (future).
- ....
⚒ U.1.3.3 A functional tasks & actions floorplan, external
functionality
Not all information is created equal. For a line there must be at least an ordinal scale.
Ordinals: variables that have a natural order, but no quantifiable difference between values.
Ordinal lines by tasks, activities (left to right):
- Business geography, innovation flexibility - Marketing governance communication
- Business geography, innovation flexibility - Customer Buyer
- Suppliers partnerships - Customer Buyer
- Suppliers partnerships - Marketing governance communication
Aside these lines other are able to get a description, there are no gaps left.
The natural ordinal did change by changing the perspective external services from the internal ones.
In a figure:

Notes:
👁 The goal for each horizontal line is at the right side (which).
👁 Interactions are only allowed vertical and horizontal not diagonal.
👁 managing design & change is conforming the SIAR cycle (PDCA/DMAIC).
functioning
Ordinal lines by tasks, activities (left to right):
- Business geography, innovation flexibility - Suppliers partnerships
- Business geography, innovation flexibility - Customer Buyer
- Marketing governance communication - Customer Buyer
- Marketing governance communication - Suppliers partnerships
In a figure:
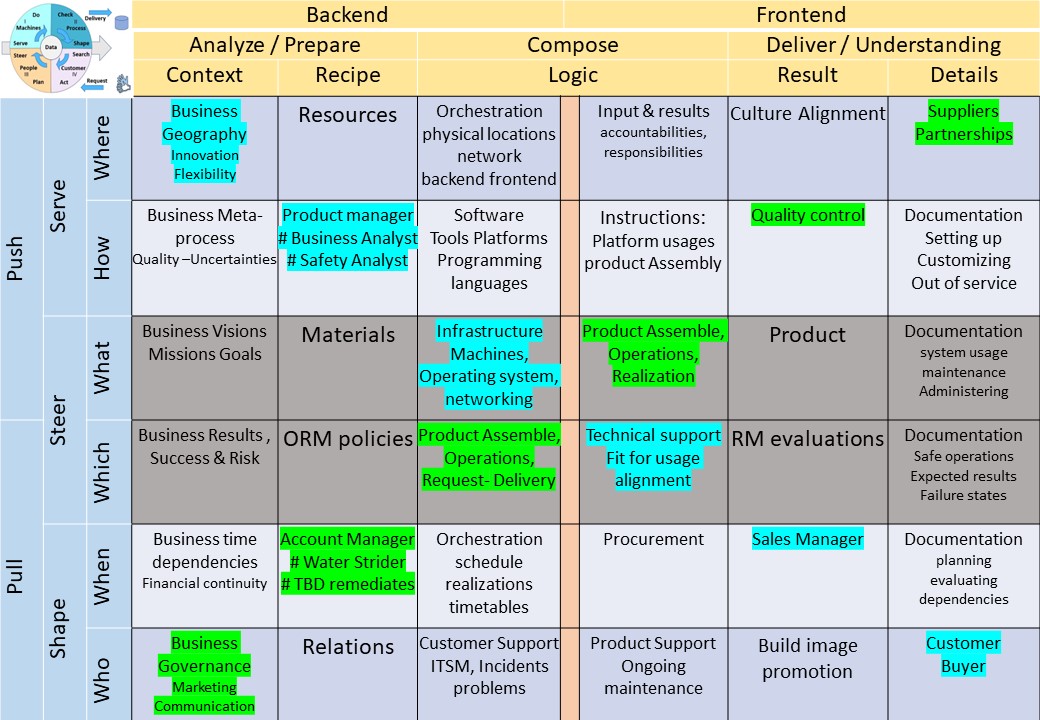 Notes:
Notes:
🎭 The perspective change to functioning is changing the goals column.
🎭 In the centre there are generic indispensable tasks activities.
⚖ Compliancy obligations
There are a lot of obligations, they are becoming mandatory by regulations.
Support To get covered by information knowledge for a portfolio:
- Ongoing Maintenance and support
- Clear accountability responsibilities
With the product a lot of knowledge has to be handed over:
- System usage, maintenance descriptions
- How to use the product in a sae way
- What is needed for interoperability and dependencies
- Installation, setting up, customizing, out of service

U-1.4 Operational Service Improvements
Creating an organisational structure that is efficient and effective is in an underdeveloped situation, unchanged since prehistory.
A lean service mindset is completely different.
What are challenges being faced?
- Ambiguity in goals, Complexities for goals
- Uncertainties for accountabilities
- Fast changing volatile circumstances
🎭 U-1.4.1 The value for the Customer, Requestor, Data subject
Defining "Value"
Customer value is essentially the worth of a product or service to a customer.
It encompasses all the benefits and costs associated with the product or service.
Customer value broken down into several types:
- Functional Value: The practical benefits of the product or service.
- Monetary Value: The cost savings or financial benefits.
- Social Value: The social benefits, such as status or acceptance.
- Psychological Value: The emotional benefits, like satisfaction or happiness.
Understanding customer value helps to meet their satisfaction.
Defining "Customer", "Requestor", "Data subject"
A customer is an individual or business that purchases goods or services from another company.
Customers are crucial because they drive revenue and help businesses thrive.
There are different types of customers:
- External Customers: individuals or businesses that buy the final products or services.
- Internal Customers: employees or departments rely on each other within the company.
Customers can also be categorized as:
- Consumers: These are customers who purchase goods or services for personal use.
- Clients: These are customers who receive personalized services, often in professional settings like law firms or consulting agencies.
Understanding who your customers are helps to meet their needs.
The why of value for: Customer, Requestor, Data subject
"Justification" is the answer for why something is in need by, or in name of: "the customer", "requestor", "data subject".
A "business case" is a financial underpinning for a delivery. The financial argument can be irrelevant but in those cases causing a new problem: the budget.
Describing "justification" is not simple, in both value and legal contexts.
Value justification:
- Affective-Cognitive Theory:
- Emotional Significance: Values stem from our emotional experiences.
- Cognitive Reasons: involves rationalizing why a value is important.
- Value Judgments:
- Cultural and Social Norms: based on the norms and traditions of a society.
- Personal Principles: based on personal beliefs or ethical principles.
Legal Justification:
- Teleological (Laws) justification :
- Outcome-Based: justified by their outcomes.
- Purpose-Driven: justified by their intended purposes.
- Deontological justification (Laws regardless of outcomes):
- Rule-Based: focuses on the inherent rightness or wrongness of actions.
- Duty-Oriented: legal actions based on duties and obligations.
Understanding the justification helps to meet their expectations.
🎭 U-1.4.2 Administrative cyberworld, Information as a product
Multi tenancy & shared resoruces
A question is about segregation, decoupling, by accountablities, responsibilities.
- What are the providers tasks
- where are the tenants coming in
A multi tenancy approach looks complicated but when considered from start will simplify things a lot.
Having many tenants supported in an ad hoc way e.g.: using dedicated (virtual) machines for each of them, will be very complex.
The outsourcing argument for having doing it all by someone else is underpinning this.
(ITIL in 2018)
Management may also need to be coordinated across multiple owners and operators.
For instance, a service provider´s infrastructure management system and the cloud customer´s application management systems should be connected (see the diagram).
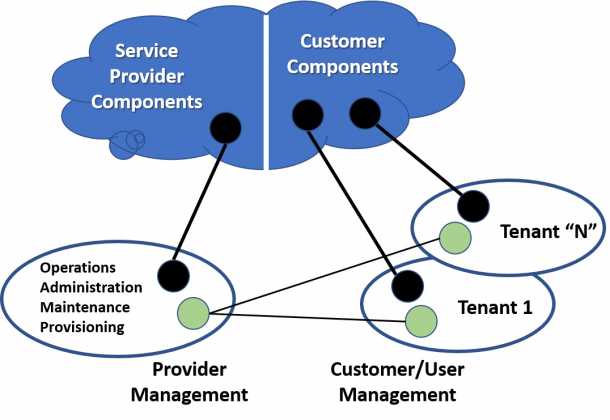
The ICT service, technology, supporting multiple services in shared infrastructural resource usage is multi tenancy.
When there is no shared infrastructe the information safety and processes like access management have no managed entity.
Multi tenancy adds requirements for:
- Clear definiton of roles and duties
- clear definitions of tasks by roles
- recognizing conflicts in combining roles, combining tasks.
thinking processess or services
Architectural thinking in the Wild West of data science (2018)
Good old CRISP-DM is too limited, an attempt to get it more structured is an IBM solution method (Asum)
ASUM-DM is part of a more generic framework called Analytics Solutions Unified Method (ASUM) that provides product- and solution-specific implementation roadmaps covering all IBM Analytics products.
This is just anoter way of the PDCA and DTAP cycle, develop, test, accept, prodcution.
I prefer my developments: SIAR, process life cycles and dependencies, they are embedding lean.
🎭 U-1.4.3 A safe environment for cyberworld information
Detailed safety cybersecurity overview
Under pressure to comply with GDPR, HIPAA, PCI-DSS, ISO27k, SP800-53 and more, you're concerned about cyber incidents. Management demands action.
About you? A 'management system' for information risk and security is more than just good practice. It enables the achievement of your organisation's business objectives.
A review 👓 of the whole
27k series (Isec ltd - secaware).
ISMS without and with PII
When there is PII (Information Security Management System) involved in the ISMS (Information Security Management System) there additional attention points to take care off.
This is not covering why or how PII information is used.
ISO 27001 vs ISO 27701: Key Differences and Similarities Explained (feb 2023 Emily Bonnie, Cavan Leung)
ISO 27001 includes six clauses that detail requirements for establishing and maintaining an effective Information Security Management System (ISMS).
- Clause 4: Context of the organization
This clause lays out the context for the ISMS, including the information assets that need to be protected and the goals for the ISMS.
- Clause 5: Leadership
Senior management must be committed to the success of the ISMS for it to be effective. Processes should be in place to monitor, test, and improve security processes over time and to ensure adequate resources are dedicated to maintaining the ISMS.
- Clause 6: Planning
This clause addresses how organizations approach both risks and opportunities. Documentation must be established that outlines how the organization identifies and treats information security risks, as well as defined goals for the ISMS.
- Clause 7: Support
This clause ensures that adequate resources will always be available to support the ISMS. In particular, subject matter experts that understand how the organization handles customer data and how the ISMS functions.
- Clause 8: Operations
A risk management strategy must be defined and documented, including how risk assessments should be carried out.
- Clauses 9-10: Performance evaluations & continuous improvement
These two clauses work together to document a plan for monitoring and improving ISMS performance over time. Periodic penetration testing and internal audits are included here, as well as plans for addressing any nonconformities that are discovered.
ISO 27701 includes four clauses that detail the requirements for establishing an effective Privacy Information Management System (PIMS).
- Clause 5: Data protection
This clause goes through ISO 27001’s Clauses 4-10 and defines where additional privacy controls may be required.
- Clause 6: PIMS guidance
This clause expands on ISO 27002 control guidelines to ensure that any and all information security measures also include data privacy.
- Clause 7: PII controller guidance
This clause is an extension of ISO 27001 Annex A controls specific to PII controllers. These controls are designed to close any gaps in data privacy not covered by ISO 27001.
- Clause 8: PII processor guidance
Annex B controls are specific to PII controllers, and address the data privacy measures not covered by ISO 27001.
Strictly speaking, ISO 27701 certification does not satisfy GDPR requirements. While ISO 27701 compliance will help you demonstrate GDPR compliance, the two are not interchangeable. ISO 27701 is a security standard; GDPR is a legal framework — and it’s important to note that ISO 27701 does not cover every aspect of the GDPR.
However, ISO 27001 and ISO 27701 compliance offer organizations a solid foundation for fulfilling GDPR requirements. By combining the two standards, organizations can build trust, demonstrate efforts to comply with current data privacy legislation, and better prepare for future privacy regulations.
reactive ISMS, Deter Detect Defend
One of many other frameworks
6 phases incident response plan
Note the differences in words when the focus is on recovering from a breach.
Accountability responsibility at the organisation:
- Impact analyses
- Preparation to recover from an incident with impact
- Validation of the preparations to recover
Putting the two partial cycles and the full one into Jabes:
- Using invented scenarios knowing the environment and using open source known vulnerabilities:
- Delivery review (Plan) Communicate what to learn, options for improvements.
- Preparations (Do) Realisation of proposed improvements..
- Analyse Scope: (Check) goal limit to what is applicable & avoid overload.
- Analyse adverse effects: (Act) Avoid being the cause of unintended outages.
The goal is an assumed safe environment but events can still happen.
- Several steps are avoided because of involved impact. These need to be designed engineered build and validated their own cycle:
- Continuity Recovery From several scenarios that systems are corrupted or unavailable how to solve those.
- Monitor & respond What is monitored for possible signals covering scenarios.
- Stop the line How to isolate and contain in case of events from scenarios.
- Root cause mitigations Form scenarios what possible actions are.
The goal is getting prepared for the unexpected.
- The full circle: validate what is prepared is an action on regular planned time schedules.
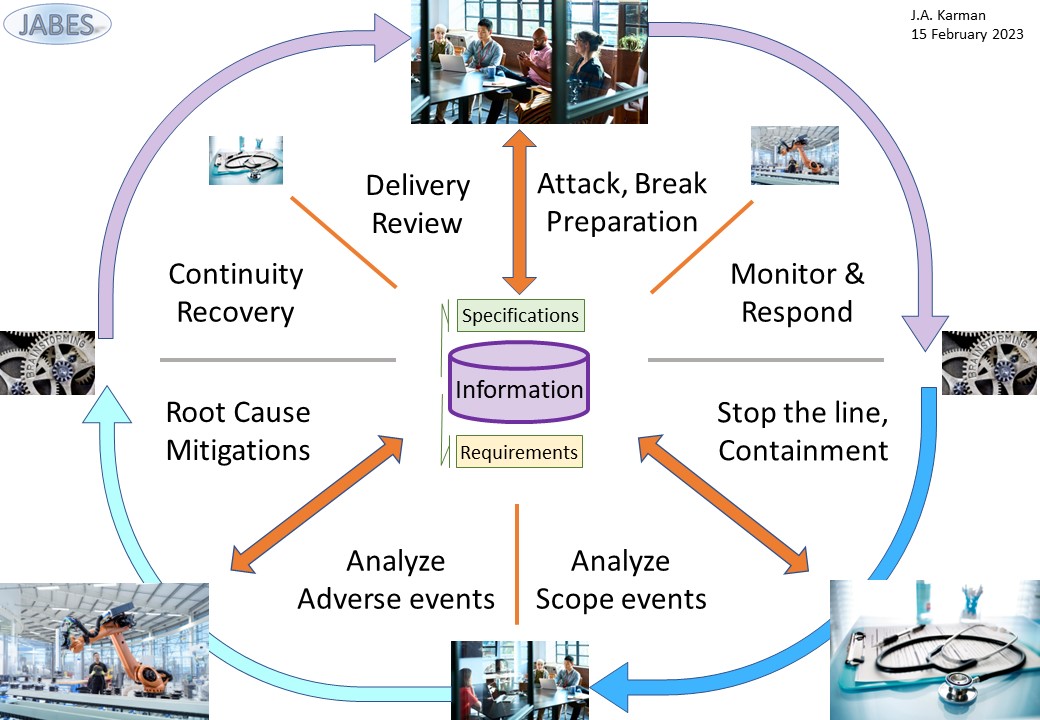
In a figure:
proactive ISMS, pentesting
Almost nobody likes Penetration Tests (Dietmar Margraff may 2023)
Reasons may include but are not limited to:
- Compliance: regular penetration testing by compliance reasons, regulations/legislation.
- risk department: theoretically a subset of compliance. Compliance is driven internally.
- Improvement: for the purpose improving security of a system. (preferred justification).
Some of the problems we face in penetration tests:
- The results are often so complex that only penetration testers completely understand what took place.
- Penetration tests are expensive and often take quite a bit of time.
- The perceived value of a penetration test is low.
In order to attempt to solve these problems, we can derive goals ...
in order to use penetration tests as effectively as possible, it is important that we position them appropriately namely as a link in the larger cybersecurity process. The penetration test does not exist as its own separate process but should be intimately integrated into our existing processes.
...
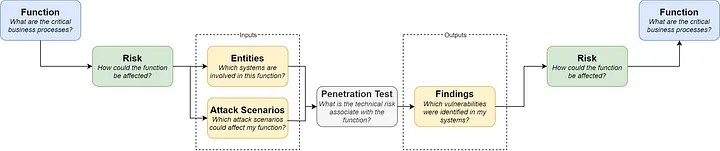
- Risk Management: by starting with risk management and working back towards it, we can increase the value of the risk analysis by more accurately classifying the risks.
- Change Management: changes to infrastructure or products should include a risk analysis to ensure that they do not expose us to additional risk.
The return of the V-model approach is remarkable to take notice off.
This uncommon vision for cyber security gives a way for restructuring it into organisations.
💡👁❗ Risk based information safety indispensable components of organisational processes.
💡👁❗ Architectural lead for information safety embedded for organisational processes.
💡👁❗ Operational activities for information safety embedded in organisational processes.

U-1.5 Shape: Manage Information Services
Optimising services is the goal for lean "processes cyber adminstrative".
When the technology connection is under control the challenge is going for services.
Where to pay attention on:
- T - Operational Excellence
- I - Service Excellence
- P - Customer Excelence
🎭 U-1.5.1 ITIL: service management technology driven
ITL Layered service structure
The ICT service with a perspective in the technology provisioning is nicely described at:
ITIL in 2018 – cloudy days ahead? (InsightaaS an analyst firm)
Modern IT requires an expanded range of management capabilities as is illustrated in the diagram below (this is not an exhaustive list of topics, however!).
Three levels of management need to be considered:
- systems from multiple providers,
- services that combine multiple components,
- endpoints (users and "things") that access the services.
ITIL currently addresses some parts of each level.
This is clearly a technology perspective when access, business, location and device are placed at the customer part.
The customer is not the customer in the perspective of the organisation "external customer", the organisation is the customer "internal customer".
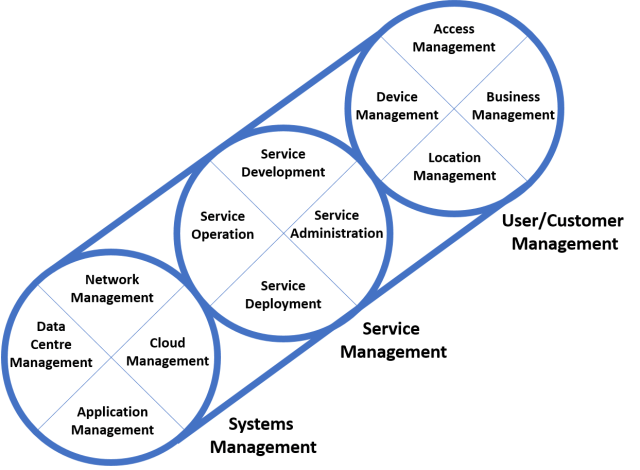
A figure, see right side:
Systems: Technology infrastructure.
Services: Limited to Technology infrastructure.
User/Customer: Limited to Technology infrastructure.
 The diagram was used in ITIL 2011 to illustrate the relationships between ITIL´s core guidance topics.
The implied model is functional and siloed, i.e., a model based on a sequential plan-build-deploy paradigm.
Today, "mass collaboration" using agile methods and team-based DevOps projects is changing the management model.
The diagram was used in ITIL 2011 to illustrate the relationships between ITIL´s core guidance topics.
The implied model is functional and siloed, i.e., a model based on a sequential plan-build-deploy paradigm.
Today, "mass collaboration" using agile methods and team-based DevOps projects is changing the management model.
Changes without justifications are clueless. Peter Drucker:
“There is nothing quite so useless, as doing with great efficiency, something that should not be done at all.”
What is needed are efficient effectieve services. Why to change in the service before what and how to change.
🎭 U-1.5.2 Simplify USM: using words, lean agile

Words matter - Vocubalary (USM)
There is lot of misunderstanding confusion by using words in different meanings different intentions.
The
USM principles (Unified Service Management) are mentioning this and suffering from this.
An attempt to do a cleanup is removing from the prinicples definitions and methodologies.
Important methodologies to isolate are about lean & agile.
Definitions:
- Service: is a supported facility. The facility is specified in terms of goods and actions, and the service is evaluated in terms of functionality and functioning.
⚠ 👉🏾 What is a service? (USM)
Inventory of 100 ISO/IEC definitions of 'service' revealed that they have made rather a mess of this.
The popular best practice frameworks do the same.
- Agile, Lean: Unfortunately, a) we do not have a good definition of lean, and b) not everybody means the same thing when they talk about lean.
Definition of Lean
It is like the elephant. When you know one you will recognize a similar one, when you don't know one it is impossible to define and recognize.
⚠ 👉🏾 Inventory of agile definitions reveales that this is a complete mess. “Lean Standard” ISO 18404 – A Questionable Idea … and
Agile Lean Glossary .
- Process: Throughout the organization, everyone consistently applies the same pure definition of the term 'process'.
Processes describe (only) activities, in an unambiguous and structured manner, and are included in an integral and integrated process model.
The term 'process' is used all the time for matters which are not processes, but practical routines of the type of procedure or work instruction.
- description deals only with 'what' (activities), there is no 'who' and 'how' in that.
- consists only of activities and can thus be indicated with a verb.
- is countable: how often the process has been executed, from start to finish.
- description is independent of practical conditions and therefore never contains a practical 'gateway' in which the course of the process is split.
- have a unique, customer-relevant goal in a customer-oriented service.
- can be split up into sub-processes, but because of this the process does not change.
- the model orders the processes.
- the model is integral: it includes all activities for managing all services.
- the model is integrated: each activity occurs only once in a process model.
- is monitored (control) to ensure that the intended result is actually achieved.
- Routines: type of procedure or work instruction.
- is structured based on processes, not based on an organization or products.
- at the end of the day, the majority of routines is not project-based.
- variations lies in the people, the technology used, and the services produced.
- Reorganizing is relocating tasks, authorities, and responsibilities (TAR), without adjusting those processes.
The question who carries out the process activities varies over time, just like the technology resources that these employees use.
In a reorganization, only procedures and/or practices are adjusted.
Intentions matter - Lean vocubalary (USM)
Lean Agile methodologies. The flow-shop (process-based), job-shop (line-based) project-shop (project-based) are three methodologies known in lean.
Service providers achieve better results with process-based work than with project-based or line-based work.
Preferences:
- Process-based goes before project-based or line-based.
lean - the preference for: flow-shops using pull-push etc
- What goes before who and how.
- Avoid superfluous material, superfluous actions, superfluous resources.
lean 3M
Methodologies:
- Process-based End-to-end overview and insight into the service delivery
- teams pass on their contributions to the end-result to each other in a chain.
- being able to steer on that end-result.
- line-based No overview in end-to-end overview and insight into the service delivery.
- persons pass on their contributions to the end-result to each other in a chain.
- not being able to steer on that end-result.
- project-based .
- persons pass on their contributions to the end-result. There is no handover in a chain.
- work can only make a partial contribution to the service delivery.
- Standardization to relevant topics & components of the service management system.
For example, standard: process descriptions, workflows, calls, profiles for process and line management, tool configurations, forms ...
work standard: key to continuous improvement - , 5S
- visual confirmation of routines and structures in a uniform design.
In order to promote the recognizability to all parties involved, the organization uses:
- simple structures and pictures
- recognizable components
- uniform and elementary colors
- uniform dimensions
- arrows for logical relations
lean - not a tool but a culture. -
- motivated people Team decisions all serve the enterprise interest.
- respect for people Teams and organizations are aware of they are only a link in supply chains and networks.
What applies within organizations with regard to cooperation and integration also applies between organizations.
lean -
+
ningensoncho ningenseisoncho a culture shock.
🎭 U-1.5.3 Cleaned up USM principles
USM principles
USM, Unified Service Management, specifies a service management architecture based on principles and not on practices.
The principles are organized according to the domains of the service management system in the USM Customer-Provider Interaction Model.
Provider:
Reduce complexity by segmenting and creating standardized building blocks, and apply those building blocks consistently in continuously improving service delivery.
- Plan - Enable
- Be consistent with the principles, but not uniform.
- Make everything as simple as possible, but not too simple.
- Standardization secures predictability of performance.
- Structure systems by segmenting them and monitoring the relationships.
- Improve service delivery continually to keep customers satisfied.
Services Architecting functionality:
Specify and evaluate services according to a simple and unambiguous structure.
- Process:
- Specify each service in terms of facilities and support, in order to manage and integrate services unambiguously and uniformly.
- Assess a service unambiguously, uniformly in terms of functionality and functioning.
- The management system process model includes all activities relevant to managing service delivery and each activity appears only once in the process model.
- Prioritization of risks (both innovations and threats) takes place through the same prioritization system as the prioritization of reactive actions.
- People:
- Promote control by organizationally separating tasks, authorities, and responsibilities that may cause conflicts.
- Apply "Separation of Duties" to processes, by distinguishing management between: a/ process, b/ functionality (specification) and c/ line (technology realization).
If Separation of Duties is used between process and line management, use the same structures and profiles throughout the organization.
- Matrix organizations by distinguishing coordination between process and team.
- Organize the coordination of executive actions unambiguously, through either hierarchical lines or process logic.
- Tools:
- The service provider stimulates all employees and stakeholders to propose improvement initiatives, and handles these initiatives in a structured way.
- The service provider steers for improvements in a structured way, by removing threats as well as realizing innovations (internal).
- The service provider manages a register of improvements.
- Risk management is a standard part of the process model of the service provider.
Services Provisioning functioning:
Specify each service in terms of facilities and support, in order to manage and integrate services unambiguously and uniformly.
- Process:
- Make an inventory of the infrastructure, components into which it is divided.
See that unwanted complexity is avoided by directing it towards segmentation.
- Each service is specified in terms of facilities and support.
For example:
- service agreements
- service reports
- request forms
- customer satisfaction surveys
- managed infrastructure registers
- Include guidelines in routines, regulations, and checklists.
Organize all work according to a uniform set of workflows.
- Optimal service delivery requires a systematic and structured design of routines, categorized by process, procedure and work instruction.
- People:
- All employee profiles are related to and structured according to the same process model, throughout the organization, for an organization-wide profile structure.
- Set an upper limit on the size of projects and changes.
- Similar work is performed with similar processes, throughout the organization.
- Technological tools support employees in carrying out their activities in the processes.
- Tools:
- Support structured routines with structured communication.
- The organization has established a design policy and manual.
- Audit the infrastructure and practices for compliance.
- All service reports follow the same structure.
Forms for requesting or modifying the services also follow that structure.
Customer, Requestor, Data subject:
Strive for value creation in a mature service delivery, by focusing on the customer's interests.
- Ideate - Asses:
- Service providers know and understand their customers business.
- Service agreements are described in terms of the customer's business interests, and specify how the facilities and support contribute to these.
- The service provider involves the customer as much as necessary and possible in the handling of the service delivery and keeps the customer well-informed.
The customer is able to account service delvieries into the execution of its business.
- To support proactive service delivery additional incentives, in the form of reserving a minimum amount of time for handling risks.
This incentives helps to break 'the delusion of the day' to support continuous service improvement.
The customer interests are concretely served by eliminating threats and exploiting innovations.
- The service provider steers for improvements in a structured way, by removing threats as well as realizing innovations (external).
This restructured version of USM principles gives many new ideas for promotions and realisations.
💡👁❗Promotion how to integrate lean principles.
💡👁❗Promotion how to understand service principles.
💡👁❗A realisaton roadmap how to create a service organsiation using lean principles.

U-1.6 Maturity 3: Fundaments Services
"Managing services" is a prerequisite for "processes: cyber/adminstrative".
The focus should be on the value stream services and processes. It starts by knowing the shop floor.
From the three TIP, interrelated scopes:
- ❌ T - Operational technology services
- ✅ I - Information processing services
- ❌ P - customer excellence services
⚖ U-1.6.1 The goal & maturity of the internal organisation
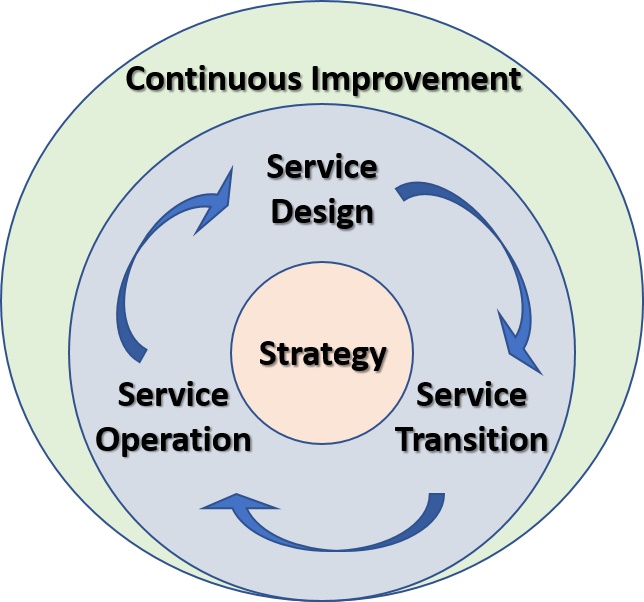
Open for change: PDCA - DMAIC - SIAR , lean
This is the first image: dynamic, static & stages for flow & control.
Change:
PDCA
DMAIC
- define, measure,
- analyze, improve
- control
SIAR
- situation,
- input
- activity/analyse
- result/request
What Descriptive or the situation in areas with cycles:
- functionality: Control, Collect, Execution, Evaluation
Management in avoiding issues an doing improvements is done by empathy, good feeling, with good luck.
😉 Improving requires acceptance to unlearn and learn consciously.
👉🏾 Needed is a culture mindset: wanting improvements.
⚖ U-1.6.2 The goal & maturity of the organisation servicing external
Functionality fucntioning, internal, external
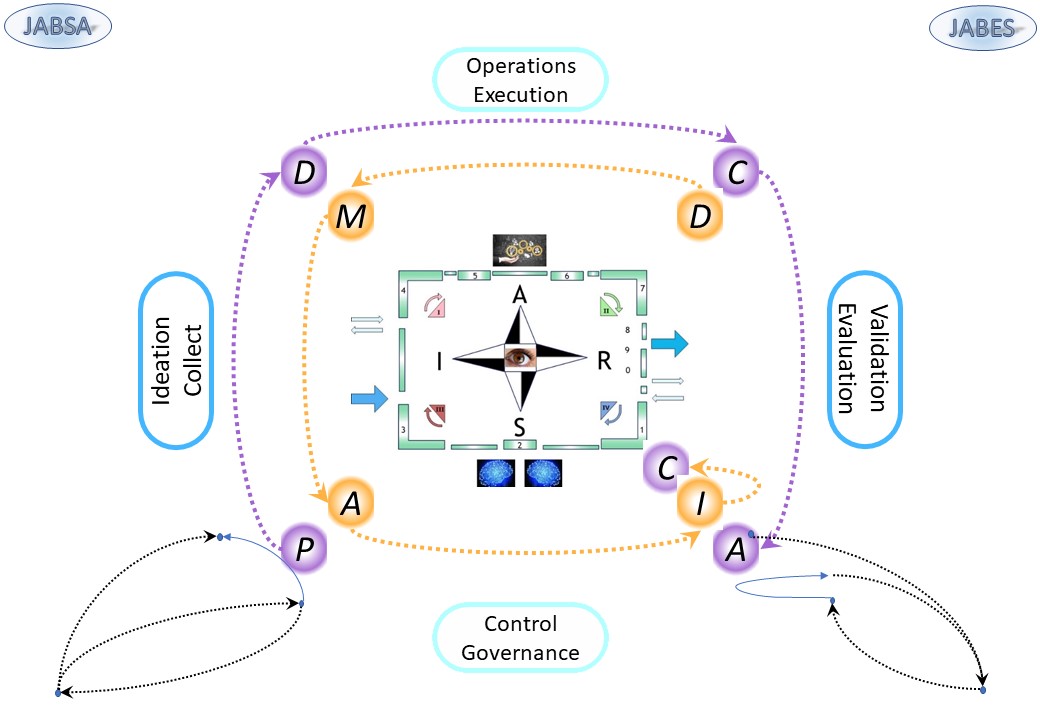
🎭 The difference between designing functionality and designing for functioning is hard to underestimate.
Who is communicating with who, interacting for what to service the service is different by goal and initiative.
🎭 The two diagonals are representing these service lines one for functionality one for functioning.
👉🏾 Both functionality and functioning must be in scope.
🎭 The difference between managing the internal organisation and one supporting external contacts hard to underestimate.
In the centre of lines for functionality and functioning with activities there are complete different sets to manage.
🎭 The two diagonals are representing service lines that can be internal or external.
👉🏾 Both external and internal must be in scope.
⚒ U-1.6.3 Result: Value creation for Customer, Requestor, Data subject
Defining "value"
Knowing and understanding business, agreements in business interests, a well-informed customer, all are requiring alignment on value.
⚠ The alignment on value is not easy, not easy in definitions and not easy in understanding.
It must be tried , however there is not a generic approach available for evaluating and measuring.
⌛⏳ Suitability by: completeness, correctness, appropriateness, efficiency, compatibility, interaction capability, will be ever lasting challenges for improvements.
⚙ U-1.6.4 Safety: Capabilities for managing uncertainties & risks
Risk management, safety
Analysis: Chief Compliance Officer (N.Dean Meyer)
Many functions can fall into the scapegoat trap by claiming authority over, and hence accepting accountability for, others behaviors.
- A "security" group that thinks it's accountable for security, rather than helping everyone to operate in a secure manner.
- A "business continuity" group. that unilaterally designs the plan.
- A "quality assurance" or "testing" group that tries to take accountability for quality through inspection and control, rather than by providing a testing service to others who are accountable for producing quality products.
Producing products, and the quality of those products, are not two distinct jobs. Experiences in every industry prove the same principle: Responsibility for compliance, safety, security, and every other aspect of quality should never be separated from responsibility for doing the work.
Coordinators help others with their accountabilities. And if oversight (Audit) is needed, it must be kept arm's-length from service-oriented Coordinators.
👉🏾 In a service oriented mindset, tasks roles and activities for safety, quality, security will get an understandable position.
CISO advisory
👉🏾 Being service oriented, the CISO can sell "compliance assessment studies" that help managers get ready for the real external audit, or know how their subordinates are doing.
⚙ U-1.6.5 The goal & maturity of the organisation as service provider
Understanding lean, example USM clean up
😉 The defined principles of USM are not bad work.
They are very well defined by a list of architectural decisions with a rationale and implications.
Although that high quality and grateful for that, I was convinced in doing a clean up.
The most important aspect is not the result, but the journey in isolating what is covered by lean.
👉🏾 Understanding lean, the issue:
Agile, Lean:
Unfortunately, a) we do not have a good definition of lean, and b) not everybody means the same thing when they talk about lean.
Definition of Lean
It is like the elephant.
When you know one you will recognize a similar one, when you don't know one it is impossible to define and recognize.
It is like defining what is car an automobile. When you search for it, try to do this the results are dissatisfying.
The legal solution is describing the justification in properties, attributes and purpose.
❓ The question is: how to recognise "lean", evaluate "lean" practice.
❗ Do the journey by recognizing details of lean and order them in order of importance.

An attempt for lean in properties, attributes and purpose:
- respect for people ningensoncho ningenseisoncho a culture shock.
The most important one but the one least mentioned. About:
lean motivation
leadership .
Teams and organizations are aware of they are only a link in supply chains and networks.
What applies within organizations with regard to cooperation and integration also applies between organizations.
- motivated people Team decisions all serve the enterprise interest.
This one is seen at the "agile manifesto" for building software.
- lean - not a tool but a culture. Hence, you have to convince your people that lean can help them.
This is also often called a mindset change. This is fundamentally different from installing a machine or developing a new product.
-
visual confirmation of routines and structures in a uniform design.
In order to promote the recognizability to all parties involved, the organization uses:
- simple structures and pictures
- recognizable components
- uniform and elementary colors
- uniform dimensions
- arrows for logical relations
- work standard: key to continuous improvement - , 5S
The objective of a standard is to provide a clear depiction of a task, deconstructing it into distinct stages. It ought to encompass all relevant elements, with a particular emphasis on those linked to safety and quality.
A standard can encompass visual aids, textual explanations, or a combination of both. While it should include all necessary details, it also should strike a balance between too much and too few details. ...
Work standards are best for repeatable processes. The higher the repeatability, the easier it is to write a standard. ...
Standardization to relevant topics & components of the service management system.
For example, standard: process descriptions, workflows, calls, profiles for process and line management, tool configurations, forms ...
- Muda, Mura, Muri: The Three Evils of Manufacturing , 3M
- The most famous of the three evils of manufacturing is waste (muda). You will never reach the full potential if you only look at one of the three evils.
- Unevenness was probably the last of the three evils that have been identified in manufacturing.
- Depending on the type of overburden and the system, a different solution may help.
superfluous Avoid superfluous material, superfluous actions, superfluous resources.
- The flow-shop (process-based) , job-shop (line-based) project-shop (project-based) are three methodologies known in lean.
normal” industry uses flow shops or job shops, construction usually uses project shops.
Service providers achieve better results with process-based work than with project-based or line-based work.
The assumption is: there is a scale in repetition by routines for process-based service.
A project-based delivery is able to profit from lean using: lean services, lean routines.
- Continous improvement: PDCA, DMAIC, closed loop
Any of those is hard the measure, difficult to give a clear unambigous definition.
✅ When they all are recognized and combined, I am convinced seeing lean.

Scaling and being efficient & effective
⚠ Scale of an organisations matters.
- When the organisational environment is relative small people are very well capable to organize their work.
- When the scale increase communication for alignment of work increase fast into chaotic complicated situations.
- Structuring tasks processes services brings back simplicity in ordered situations when there is to much complexity.
👉🏾 Structuring for scale to achieve simplicity is a big challenge, there is no silver bullet.
Association for the size of an organisation doing some choice.
For example: scale at airports:
- tiny: the internal organisation is relative small.
- big: the internal organisation is relative big.

Cleaned up USM, roadmap with lean
😉 The defined principles of USM are not bad work.
They are very well defined by a list of architectural decisions with a rationale and implications.
Although that high quality and grateful for that, I was convinced in doing a clean up.
The most important aspect is not the result, but the journey in going for simplicity and understanding.
👉🏾 Understanding simplicity, the issue is this list should als be applied on the principles:
- Be consistent with the principles, but not uniform.
- Make everything as simple as possible, but not too simple.
- Standardization secures predictability of performance.
- Structure systems by segmenting them and monitoring the relationships.
- Improve service delivery continually to keep customers satisfied.

There are only a few number principles left in each Logical group. In this way they are more easy this way to be translated in visions, missions, goals.
Goals and realisations:
⚖ Defined goals with a closed loop control.
⚙ Use the PDCA DMAI cycles with a pull-push.
⚒ At realisations for "People", "Tools" a different focus.
Jabes maturity vs service maturity
For Jabes there is maturity evalution for 36 attention areas. What is metnioned for service maturity is covered.
There are pinciples defined in USM that are covered by Jabes.
- Specify each service in terms of facilities and support.
Documenting specficiations is what Jabes is about
- The service provider manages a register of improvements.
Documenting improvements from idea to realasition is what Jabes is about
- Make an inventory of the infrastructure, components into which it is divided.
Documenting the portfolio for all kind of details is what Jabes is about
- Include guidelines in routines, regulations, and checklists.
Documenting the operatiing guidelines risks of details is what Jabes is about
⚖ P.1.6.6 Short checklist organisational impediments
What is to be solved:
- ❌ ✅ Internal organisation Shop Floor accountabilities responsibility's.
- ❌ ✅ The organisation servicing externally Shop Floor accountabilities responsibility's.
- ❌ ✅ Understandable results for intended value creation customer, requestor, data subject.
- ❌ ✅ Responsibility for clear safety, security at the shop floor.
- ❌ ✅ Responsibility for managing services processes at the shop floor.
These are to be understood solved and managed by management at the higher levels.
U-2 Ideate improving value streams, reducings risks

U-2.1 Safety - Access Management processes
Connecting Business & Risk management
There is ❌ not a lot of attention for this kind of knowledge. It is the enablement 🎭 people doing intended work and 📚 technology.
The realisation is full with misunderstandings and problems:
- Uncertainties for roles and for technology
- Complexities by roles and technology
- Ambiguity for safety levels internal/external
⚙ U-2.1.1 Central management: names, gid id LDAP, AD
Authentication - names
❶ In the beginning authentication was based on using logical names.
The old classic mainframe machines with all the middleware used this approach. An account, logonid, being associated to a person or a function limited to use 7 characters.
Advantages:
It is in revival with web security needing to build authentication authorisations in web logic.
Disadvantages:
- Hard to get really safe, every threat to solve in a specific way.
- Changing the name of a logon-id, account, requires change it in any related system.
Authentication - files
❷ The -nix machines are using an id (number) that is translated into a logonid name with some other attributes.
The dogma in this is that anything is a file. There are exceptions to this. A logon id groupid, I have not seen them as being files.
Disadvantage: There is no clustered approach for machines possible using LDAP for id, gid has the consequence they must be exactly synchronised to all local machines identical.
Advantage: Understandable at the operating system level for file although the inheritance of directories as files and files for content is usually misunderstood.
Understanding /etc/passwd and /etc/shadow Files
The /etc/passwd file is a plain-text database housing fundamental user information.
Each line in the file represents a user account and is divided into fields separated by colons (:)
Fields: login shell, home directory, user information, default did, user id, encrypted password, user or login name.
For improved security, critical user authentication information, particularly hashed passwords, resides in the /etc/shadow file, accessible exclusively to privileged users.
Advantages:
- A simple "this is your machine machine" approach.
- A lot of hooks for safety although these are not consistent all over the system.
Disadvantages:
- The options are for nerds getting it safe, not understandble for other persons.
- Not consistent all over an environment. Applications are out of context for safety.
- Managing clusters of machines is not a feature by design.
Authentication - Objects
❸ Windows (vax history NT) is using an object oriented approach. Evything is an object, files logon-ids whatever.
This looks not a a real difference but it really is a big step. Every object has a descriptions of the content with detailed definions of types.
Parsing of what the meaning of contents could be is obsolete, the object type is mandatory present. This whole concept is not the DOS history.
Dave Cutler (VAX NT AD Azure )
Several important safety concepts:
🤔
Security principals (Microsoft)
A security principal is any entity that can be authenticated by the operating system, such as a user account, a computer account, or a thread or process that runs in the security context of a user or computer account, or the security groups for these accounts.
... Each security principal is represented in the operating system by a unique security identifier (SID).
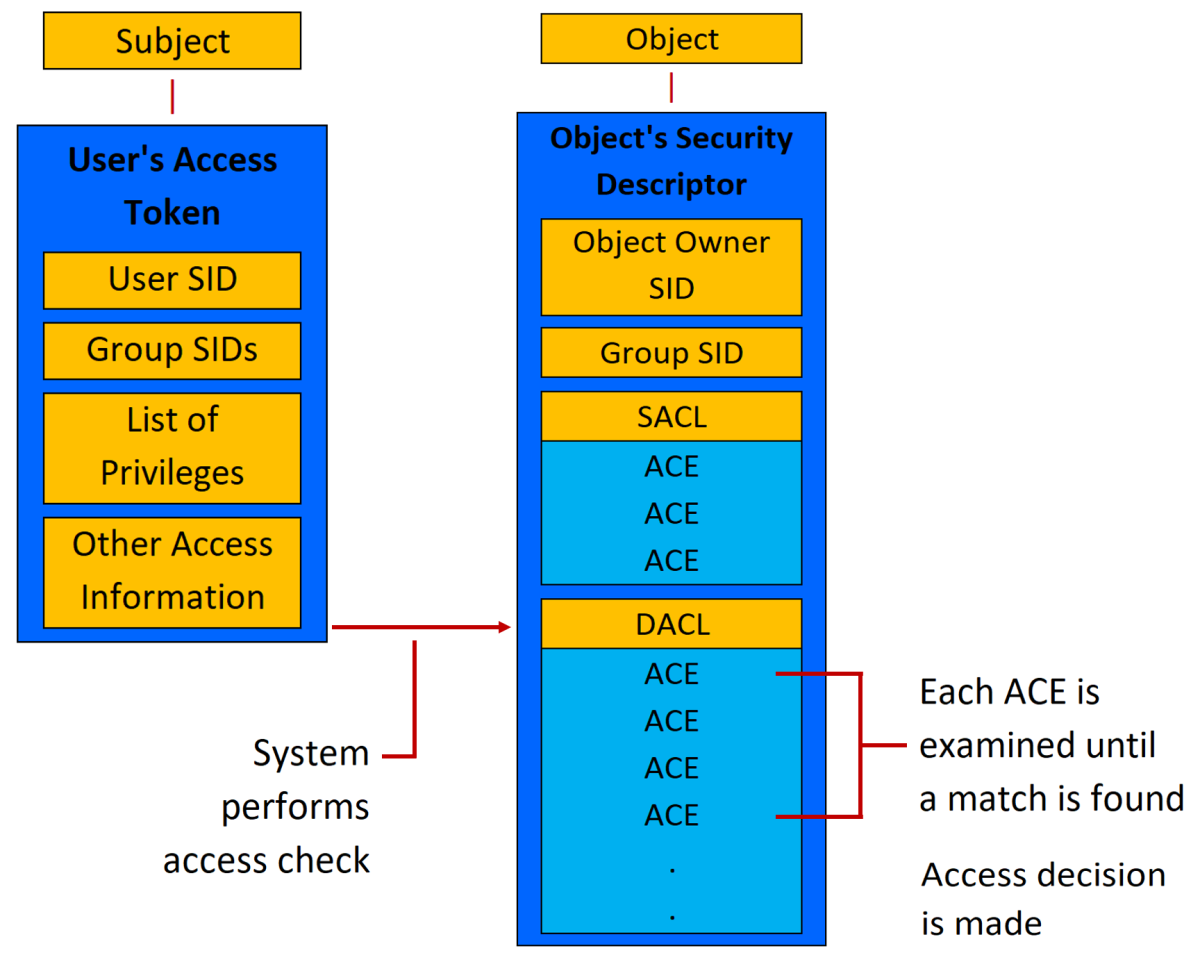 ... An access token is a protected object that contains information about the identity and user rights that are associated with a user account.
➡ When a user signs in interactively or tries to make a network connection to a computer running Windows, the sign-in process authenticates the user’s credentials.
If authentication is successful, the process returns a SID for the user and a list of SIDs for the user’s security groups.
... An access token is a protected object that contains information about the identity and user rights that are associated with a user account.
➡ When a user signs in interactively or tries to make a network connection to a computer running Windows, the sign-in process authenticates the user’s credentials.
If authentication is successful, the process returns a SID for the user and a list of SIDs for the user’s security groups.
...
Security principals are closely related to the following components and technologies:
- Security identifiers
- Access tokens
- Security descriptors and access control lists
- Permissions
🤔
Service accounts (Microsoft)
A service account is a user account that's created explicitly to provide a security context for services that are running on Windows Server operating systems.
The security context determines the service's ability to access local and network resources. ...
Group-managed service accounts provide a single identity solution for services that are running on a server farm, or on systems that use Network Load Balancing.
... By using dMSA, users can prevent the common issue of credential harvesting using a compromised account that is associated with traditional service accounts.
🤔
Active Directory security groups, group scope (Microsoft)
Active Directory has two forms of common security principals: user accounts and computer accounts. These accounts represent a physical entity that is either a person or a computer.
A user account also can be used as a dedicated service account for some applications. ...
Each group has a scope that identifies the extent to which the group is applied in the domain tree or forest. The scope of a group defines where in the network permissions can be granted for the group. Active Directory defines the following three group scopes:
- Universal
- Global
- Domain Local
Advantages:
- Covers almost any possible object.
- Easy interfaces for managing content.
Disadvantages:
- Overwhelming in the number of options and coverage.
- Failures made in content are impacting the whole environment.
⚙ U-2.1.2 Security processes - Identities access
❗❓ Who is the CSO?
Security of the assets owned by the organisation is too often seen as something technical.
💣 conflicts between ICT department pretending to be in security control, HR staff and business.
👉🏾 Solutiuon: The business is accountable for the safety, security. A CSO advices.
generic security access
There is a "Devil´s Triangle" on its own with IAM. Conflicting types of interest:
- Giving granting access to humans. Conforming the hierarchical organisation structure.
- Securing technical systems, the supply chain included.
- Design secure Platforms, secure organisational business information processes.
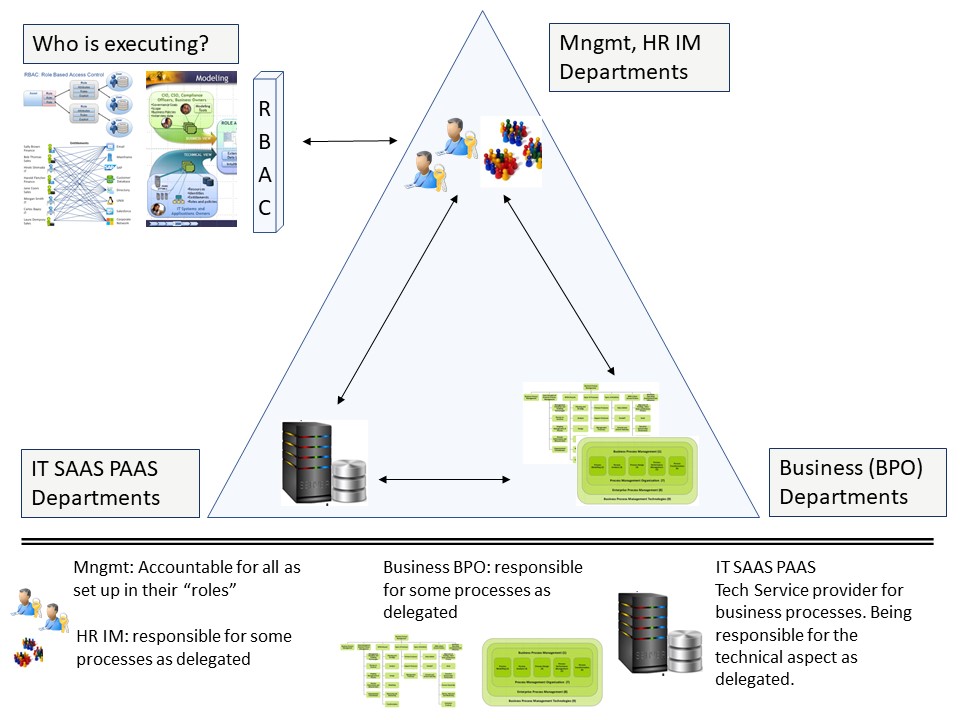
A figure:
See right side
PoLP Principle of Least privilege
What happened to:
"PoLP is an information security concept which maintains that a user or entity should only have access to the specific data, resources and applications needed to complete a required task."
?
What is PoLP
The benefits are clear:
- Prevents the spread of malware.
- Decreases chances of a cyber attack.
- Improves user productivity.
- Helps demonstrate compliance.
- Helps with data classification.
💣 The issue: without thorough knowledge of the floor and the tasks to be performed on the floor, this is a mission impossible.

🎭 P-2.1.3 A Safe environment quest (I)
Stop the line, being lean, cost saving
Keep Calm and Stop the Line—Part 2
In manufacturing, a common sentiment is that the line (or generally the process) must run.
There is some truth to that, but—counterintuitively—for a system to run well you need to know when to stop it too.
This is my second post in a series giving you an overview on when it may be better to stop the line rather than keeping it running (and making everything worse).
Hence, your operators need to stop the line if there are problems that they cannot resolve within the cycle.
This is even the justification for the well-known Toyota approach of Jidoka, or autonomation.
Jidoka means a process stops automatically if there are any irregularities.
Yet, you want to stop the line as little as possible. For this there is the andon line pulled by the operator in case of problem. This pull gives signal to an andon board, which then calls help.
The key here is to provide help to the operator quickly.

Why not a ServiceDesk, ITSM, ITIL, using tickets?
If the operator has to fill out a maintenance request so that maintenance shows up two hours later, then your line stops for at least two hours, which is a bit much.
Stop the Line If There Is a Safety Risk!
Another reason to stop the line is if there is a safety risk. The health and safety of your operators should be paramount to your production output, and a health risk (both short-term accident and long-term hazards) must stop the line.
A secure safe environment
How safe is your environment? Monitor then number of incidents. This is a goed idea to do simmilar for cyber safety.
See:
The Toyota KPI Dashboard—Safety
Safety is also one of the main headings of the Toyota Hoshin Kanri, their structure for setting targets from the top down across all hierarchies.
I found pretty much everywhere is the safety cross. This is a simple cross with the days of a month (i.e., 1 to 31). Every day the previous day is filled out.
Green stands for no accident. Yellow stands for a minor accident. And red stands for a major accident. Throughout the month a very visual representation of the safety statistic emerges.
🎭 P-2.1.4 A Safe environment quest (II)
Security frameworks
For the administrative/cyber world
CSF 2.0 Nist
The Cybersecurity Framework (CSF) 2.0 is designed to help organizations of all sizes and sectors — including industry, government, academia, and nonprofit — to manage and reduce their cybersecurity risks.
It is useful regardless of the maturity level and techncal sophistication of an organization’s cybersecurity programs.
Nevertheless, the CSF does not embrace a one-size-fits all approach.
Each organization has both common and unique risks, as well as varying risk appetites and tolerances, specific missions, and objectives to achieve those missions.
By necessity, the way organizations implement the CSF will vary.
Ideally, the CSF will be used to address cybersecurity risks alongside other risks of the enterprise, including those that are financial, privacy, supply chain, reputational, technological, or physical in nature.
To control govern the process there is cycle:
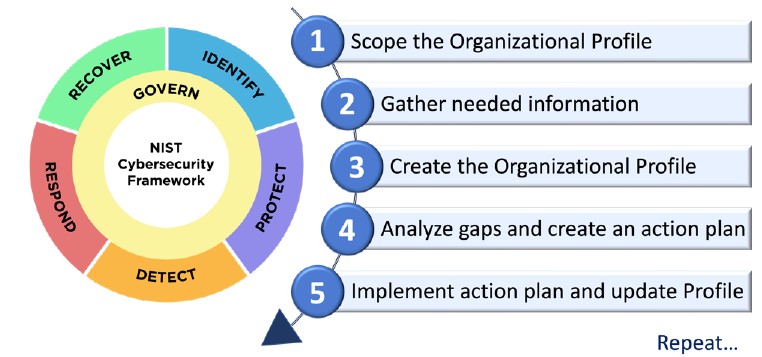
A figure,
(NIST CSF 2.0)
See right side
This one is confusing:
❶ The left cycle is the process to act on an event, the right numbering with a "repeat" is the planning preparation etc to enable acting on a event.
Usually a PDCS reference is done.
One of many other frameworks is:
6 phases incident response plan
- Preparation This phase will be the work horse of your incident response planning, and in the end, the most crucial phase to protect your business.
- Your response plan should be well documented, thoroughly explaining everyone’s roles and responsibilities.
- The plan must be tested to assure employees will perform as they were trained.
- The more prepared employees are, the less likely critical mistakes are.
- Identification This phase will be the work horse of your incident response planning, and in the end, the most crucial phase to protect your business.
- Containment Contain the breach so it doesn’t spread and cause further damage to your business.
... Have short-term and long-term containment strategies ready. It’s also good to have a redundant system back-up to help restore business operations.
That way, any compromised data isn’t lost forever.
- Eradication Once you’ve contained the issue, you need to find and eliminate the root cause of the breach.
- Recovery This is the process of restoring and returning affected systems and devices back into your business environment.
- Lessons Learned Once the investigation is complete, this is where you will analyze and document everything about the breach.
The vision that safety, cyber security, is a business organisational accountability has important consequences.
💡👁❗Chief Information Security Officer: important advisory role (risk management).
💡👁❗An understandable security scheme using PoLP, a design challenge (CSO advisory).
💡👁❗Preparing managing events identified for risks is indispensable for continuity.

U-2.2 Processes internal partially solving services
Connecting Business, Product & Project management is a big challenge.
There is ❌ not a lot of attention for this kind of attitude
Problems in organisations:
- Fast changing volatile circumstances for demand and quality
- Natural uncertainties at quality of material and transformations
- Complexities for goals, miscommunication, misunderstanding
- Ambiguity in goals, miscommunication, misunderstanding
⚒ U-2.2.1 Positive wanted functionality & negative ones with their impact
The goal
Define:
- What are: approved results using objective measurements.
- What are: drop-outs fall-outs objective measurements.
Applying materialized Information
The states of Information, has the following path:
- Collecting what is needed: determine, verify:
- What are needed functional data information assets.
- How are the functional data information assets translated into technical representations.
- How can the technical representation be stored and what is needed for that.
- Collecting How information assets should getting processed, verify:
- Processing options by supported methodologies.
- Methodologies and practices supported by operations.
- Quality control on information during operations
- Integration of information assets into usable components conform for the product.
- Have the usable components labelled conforming a master data artifact. Avoid ambiguity.
- Create the new product types of information by a defined data model.
- A clear list for the goals further extended to:
- Data governance: master-data, metadata, naming conventions
- Archiving, monitoring: Journaling delivered results, journaling processing for a result
The states by impact result evaluated on the rules, logic intentions.
Explainability with traceability are becoming mandatory requirements by auditing.
Logical floorplan visualisation
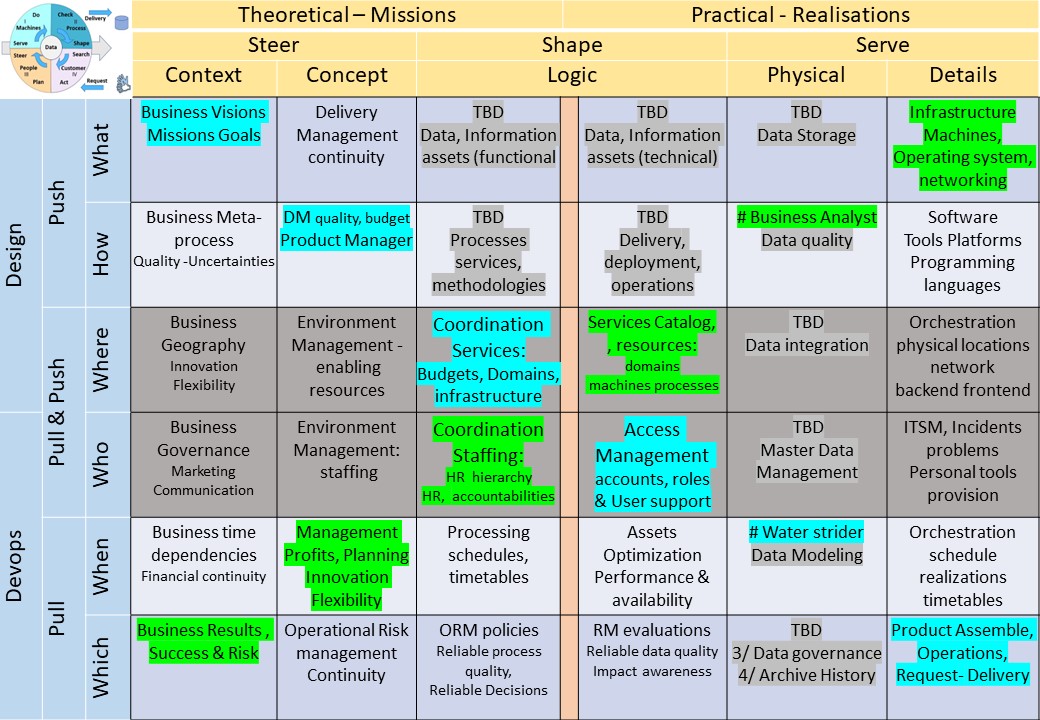
The build mirror visualisation to enlarge.

⚒ U-2.2.2 Protection of materials for wanted and unwanted functionality
The goal
A healthy organisation implements safety closed loops that are independent of the normal expected information materialisations.
Define and react on safety risks for:
- Mismatch specifications: approved results using objective measurements.
- Mismatch specifications: drop-outs fall-outs objective measurements.
- Incorrect usage Data governance: master-data, metadata, naming conventions
- Incorrect usage Archiving, monitoring: Journaling delivered results, journaling processing for a result
Processing in Applying materialized Information
The analyses on materialised Information, has the following path:
- Collecting what is needed: determine, verify:
- Accountabilities for inputs & results of materialised information.
- Responsibilities for inputs & results of materialised information.
- Technical representations and physical locations of materialised information.
- Collecting how information for business rules assets are processed, verify:
- Used Processing options, methodologies.
- Used Methodologies and practices in technologies by operations.
- Population distributions for the service and expected impact
- Reduces information about materialised information into normalised datasets.
- Use labelled components investigate for alerts, issues breaches Without ambiguity.
- Act on discoveries needing immediate actions by what is happening.
- Have a clear list for what to improve by chance and impact.
Explainability with traceability are becoming mandatory requirements by auditing.
Logical floorplan visualisation
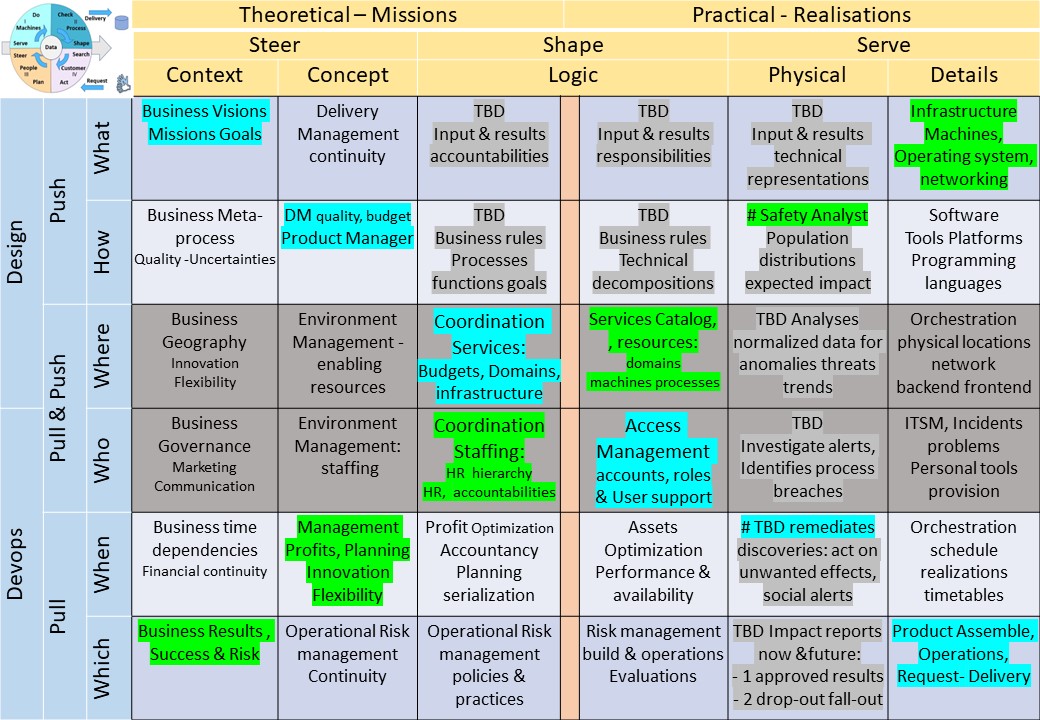
The build mirrors visualisations to enlarge.

⚒ U-2.2.3 Transforming of materials into new ones defined by functionality
The goal
Executing transformations is the fullfillment of planning:
- Creating: approved results using objective measurements.
- Creating: drop-outs fall-outs objective measurements.
- Use of Data governance: master-data, metadata, naming conventions
- Creating: Archives, Logs monitoring - Journals for delivered results, journaling processing of a result
Applying transformation usage
The Processing of Information, transformations has the perspectives:
- Collecting what is needed approved, controlled by:
- Accountabilities for the input & results. Conforming contracts.
- Responsibilities for the input & results. Processing instructions.
- Technical specifications: input & results. Quality in practices and instructions
- Collecting for what is needed conforming specifications:
- Processing instructions in methodologies for executions.
- Processing instructions for verified classified practices in executions.
- Specifications in technical representations for the information. Quality - Quantity
- Preparing information components for the specified transformation line.
- Combined planning, labelling of components, using logs, journals for executions.
- The transformation execution conform specifications / data modelling.
- Have all results for review isolated before allowing distribution.
Explainability with traceability for are becoming mandatory requirements by auditing.
Logical floorplan visualisation
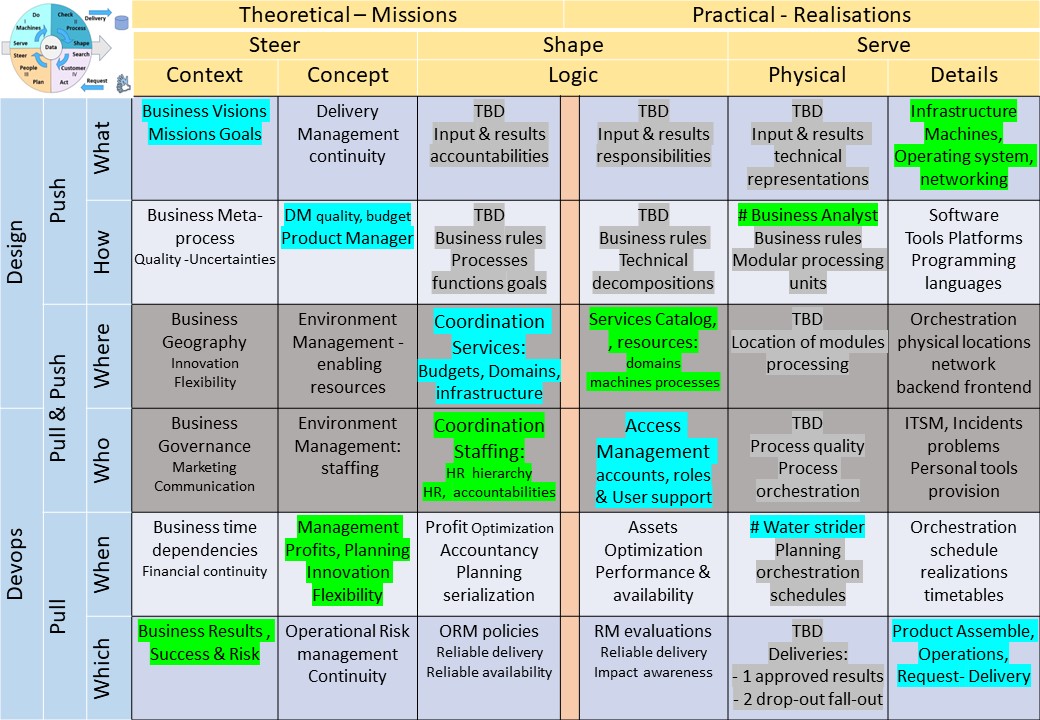
The build mirrors visualisations to enlarge:ation processing

⚒ U-2.2.4 Protecting Transformations, expected and unexpected behaviour
The goal
A healthy organisation implements safety closed loops that are independent of the normal expected value stream flow.
Define and react on safety risks for:
- mismatch expectations: approved results using objective measurements.
- mismatch expectations: drop-outs fall-outs objective measurements.
- Abuse seen in: Data governance: master-data, metadata, naming conventions
- Abuse seen in: Archiving, monitoring: Journaling delivered results, journaling processing for a result
Building the organisation materialized information, delivery -safety
- Collecting what is needed: determine, verify:
- Accountabilities for inputs & results journals logs processing.
- Responsibilities for inputs & results journals logs processing.
- Technical representations and physical locations of journals logs processing.
- Collecting how information for business rules assets are processed, verify:
- Used Processing options, methodologies.
- Used Methodologies and practices in technologies by operations.
- Population distributions for the service and expected impact
- Reduces information about journals logs processing into normalised datasets.
- Use labelled components investigate for alerts, issues breaches Without ambiguity.
- Act on discoveries needing immediate actions by what is happening.
- Have a clear list for what to improve by chance and impact.
Explainability with traceability are becoming mandatory requirements by auditing.
Logical floorplan visualisation
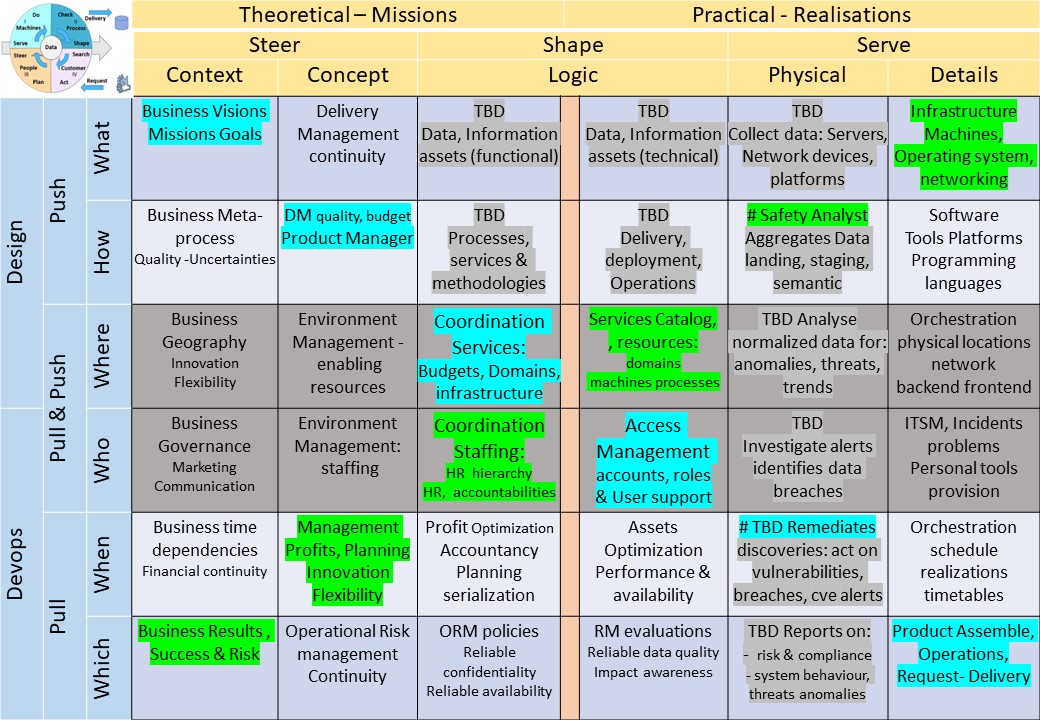
The build mirrors visualisations to enlarge:


⚒ U-2.2.5 Gemba, walking the shop floor, multiple maps
Instead of having no idea of the shop floor we have:
- Four maps for lines with internal processes procedures activities
- Two maps for the lines with external processes procedures activities
That is overwhelming and confusing. All six of them combined are making or breaking the product service.
This restructured version of doing Gemba gives many new ideas for promotions and realisations.
💡👁❗Use the logical floorplans for going, lean doing Gemba
💡👁❗Use the logical floorplans for setting goals by clear communication lines
💡👁❗Include safety, cyber security intangible in functionality, functioning activities.

U-2.3 Processes servicing customers, requestors
There is a distraction from the real business goal that information processing should solve.
A desire for easy solutions without management impact.
The reality is a needed culture change in management.
What to look at for the why:
- What is a product, purpose of a product
- Accountablity for the product
- Operational responsiblity serving Product servicing
⚖ U-2.3.1 The Product
Vocabulary
- What is (definition): A Product
is a tangible item produced to create specific value for a group of customers and to the organisation that provides it.
- solves a problem or provides a benefit to the customer
- benefits for the customer are clear and communicable
- needs a name people can remember and relate to
- it is adaptable with time, changes, in order to keep it relevant
- Products continue to be developed and supported until they reach their end of life and are discontinued
Products are considered successful if they meet customer needs and organisational goals.
- What is (definition): A Project
is
- temporary and a one-time endeavour
- creates or changes a product or service
- What is (definition): new product development (NPD)
is a series of steps that includes the conceptualization, design, development and marketing of newly created or rebranded goods and services.
😉 Duck test: "If it looks like, swims like, quacks like a duck, then it probably is a duck."
😱 What we should not do: "A seagull has feathers, any being with feathers is a seagull."
- Confusing use of words:
People often confuse products with features, capabilities, components and services:
- Feature/Capability – a product characteristic that customers can interact with to perform a specified task.
A feature or capability does not solve a problem on its own, it requires additional features to address customer needs.
- Component – an architectural building block developed for a product.
Individual components do not create measurable value for the organisation but instead are constituent parts of the product.
- Channel the method used to interact with customers. A channel may be a website, promotional event, a product package or in-person consultancy.
Life isn't black/white, there are many complications within the area of product engineering.
Note: A little bit modified what looks not to be being updated anymore.
Product LCM
product lifecycle (gartner, Clifton Gilley 2022)
A good summing up:
Many fast-growing solutions lose focus over time, as product teams add new features while keeping old ones that have outlived their usefulness.
This can drain resources and create unwieldy customer experiences.
This research equips product managers to:
- Identify product features that have outlived their usefulness
- Review and revise the customer experience to optimize functionality and workflows
- Help customers plan for product feature changes
Making sound technology product life cycle decisions starts with a complete view of the maturity levels of the products across your portfolio.
Categorize each product or service into one of the following product life cycle stages:
- Early stage, which spans from ideation to minimum marketable product
- Middle stage, spanning from early release to self-sustaining
- Late stage, ranging from late maturity to end-of-life products
A products age doesn't necessarily determine its life cycle stage.
Some products profitably meet the needs of customers for years.
Others see initial enthusiasm but soon stagnate.
To ensure a more informed categorization:
- Monitor customer feedback using product analytics tools and voice-of-the-customer (VoC) processes to gather, analyze and prioritize the customer perspective.
- Query the work management system to report the mix of work done.
The work on an early-stage product will include significant experimentation, design and prototyping.
- Interview product managers and business stakeholders.
Ask them about transitions, transformations or disruptions underway in a product's market that may not be apparent in the product roadmap or work plan.
- Get a market assessment from product management.
For products with significant internal or external competition, information on competitors or internal alternatives can inform the life cycle assessment.
- Obtain the past three years of a products profit and loss (P&L).
Nothing says declining product more than declining revenue and market share, even if the product is still generating profits and cash for the business.
- Seek external data on customer demand, customer satisfaction, competitors product offerings and potential for market disruption to understand the broader context.
Use a data-driven approach with a defined standard of evidence to categorize the product life cycle.
This removes the emotion and cuts short what might otherwise be long arguments.
Standard metrics aligned with the product life cycle provide a common language that business and technology stakeholders can all align on.
These data-based insights also help inform subsequent product management decisions, such as refining product strategy and product roadmaps, and deciding whether to maintain, refresh or retire a product.
⚖ U-2.3.2 The Product Manager
Responsibility Without Authority
💣
👓
Perhaps the greatest challenge of product management is that while product managers are responsible for the outcome of the product, they have very little actual power over the process.
❓ Those responsible for implementation, sales, marketing, support, and other key functions don't work for product managers.
They seldom share the same manager. Often the organizational chart doesn't see a common boss until it gets up to the CEO.
Thus, the work can get messy and sometimes political.
🕳 The challenge with product management is that without a flexible tool that integrates or replaces your other systems, you can't effectively align the team, collaborate on your roadmaps, and measure your work’s impact.
Another name:
chief product officer (CPO)
The CPO focuses on the why of the product ,the CTO focuses on the how of the product,
Product manager vs Projectmanger
There is a lot of confusion by PM, Product management or project management. Porject management is well visible by changes prodcut management is out of sight.
| Product Manager | Project manager |
| Researching | Breaking down initiatives into tasks |
| Setting Product vision | Planning Project timelines |
| Communicating vision to stakeholders | Allocating project resources |
| Developing strategic plan | Monitoring task completion |
| Creating and maintaining product roadmap | Communicating progress to stakeholders |
Product Manager Skills
product manager skills
Product management requires a combination of specific hard skills and soft people skills to effectively shepherd a product through the various phases of its lifecycle.
- A concrete understanding of the role and product development processes and frameworks is essential.
Product managers must be able to speak their language, comprehend the expectations, and know the scope of their job versus that of project managers, UX professionals, architects, and the like.
- Product managers also need a solid understanding of fundamental business and economic policies. If they’re unable to turn the underlying unit economics into a profitable and scalable business, they’ll have a pretty short career.
- Prioritization is at the core of product management. Assessing the relative value and impact of each potential feature, technical debt, project, and initiative, and creating a coherent strategy is the most critical part of the job.
A coherent strategy includes being able to say no when the time comes, as well as recognizing the need for a pivot or strategic shift if applicable.
- communication lies at the heart of any successful product manager. They must be a cipher and be comfortable speaking with all sorts of people filling different roles. They speak with customers, internal teams, and stakeholders.
Product managers must get along with engineers and relate to the perspectives of stakeholders.
| Product roadmap | Release Plan |
| Communicates the "why" | Details the "what" |
| Might cover a year or more | Spans only a few mmonths |
| Often shared wiht executive stakeholders | Typically an internal working document for the product and development teams |
| Serves as a high-level visual summary | Takes the strategy into an actionable plan built on specifications |
What are the 5 Ps?
Product Strategy (Chisle blog )
The 5 Ps are also known as the Marketing Mix.
They are the five pillars of a successful marketing strategy.
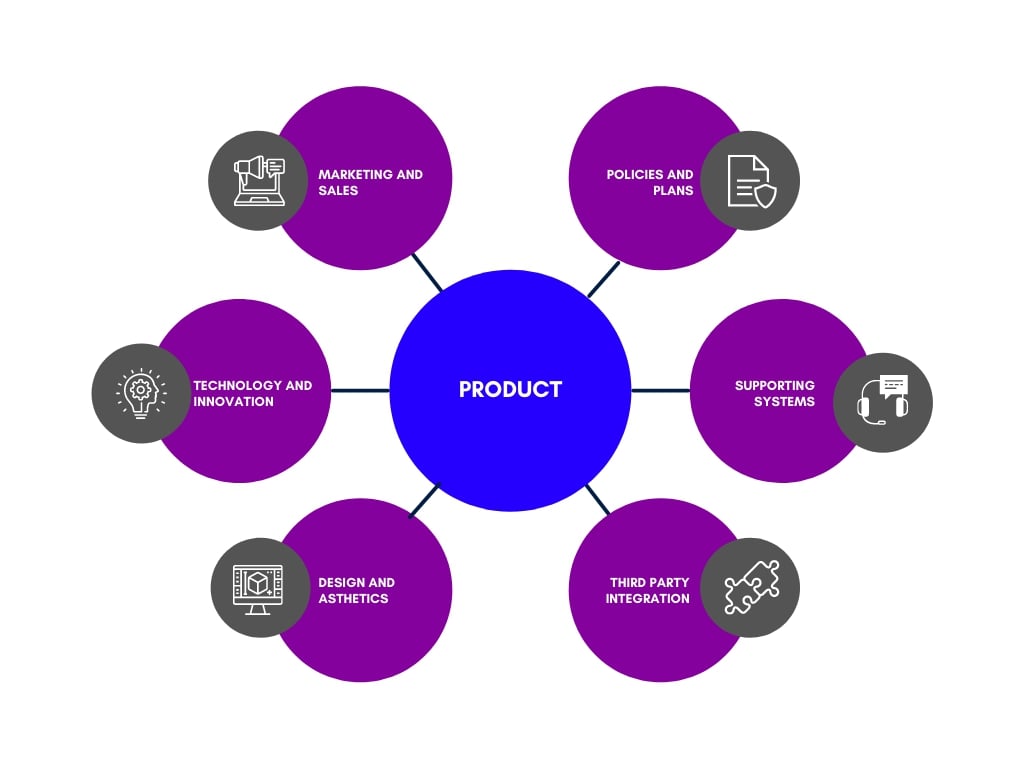 Here, the product manager comes in. They are responsible for planning and maintaining the product, whether physical or virtual, throughout its lifecycle.
Here, the product manager comes in. They are responsible for planning and maintaining the product, whether physical or virtual, throughout its lifecycle.
- Marketing & sales,
- Policies & Plans,
- Supporting Systems,
- Third party integration,
- Design and aesthetics,
- Technology & innovation.
The figure, see right side.
The 5 P’s are:
place, price, product, promotion and people. >
⚖ U-2.3.3 The Waterstrider
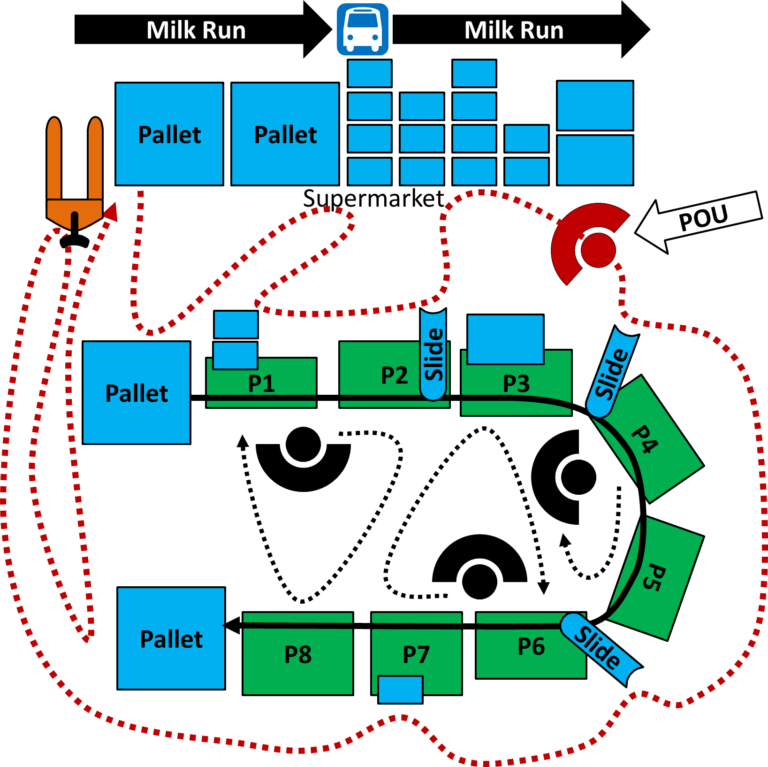
Preparations at processes.
Physical assembly Linea are logical not really different to cyber administrative ones.
Imagine materials are coming in, administrative requests, results to deliver.
With the PoU function at an administrative cyber process, the role: "Functional Management" becomes clear.
Introduction to Point-of-Use Providers (or Mizusumashi)
The primary objective of the point-of-use provider is to keep the workers supplied with material. Hence the workers can focus on the work and do not need to leave their post looking for material.
Therefore we achieve the separation of cyclic work (the workers) and non-cyclic work (the point-of-use provider) to improve efficiency.
❗ The POU, waterstrider, manages the shop floor.
First of all, do not create an additional kanban loop between the supermarket and the assembly line. ...
Instead, the point-of-use provider is close enough to the line to keep an overview about what is needed.
Rather than handling additional kanban cards, his job is merely to fill up the material at the line to its target levels.
Preparations at processes.
Administrative lines are often more segregated ones in dependent chains.
For worse when there is a siloed organisation, islands, different responsibilities, different goals.
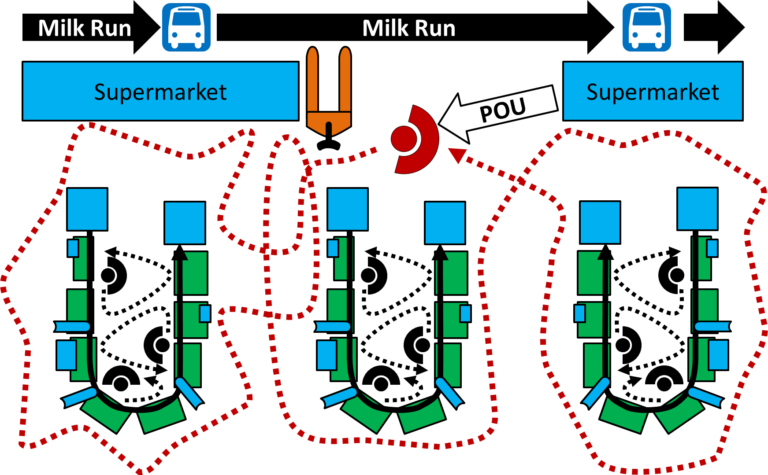 Point-of-Use Provider Routing
Many point-of-use providers are circling around one line, with the material being supplied to a supermarket close to the line through a milk run.
If the line does not need much material and the worker has a lot of idle time, he may be able to take care of the material supply for more than one line or cell at the same time.
Point-of-Use Provider Routing
Many point-of-use providers are circling around one line, with the material being supplied to a supermarket close to the line through a milk run.
If the line does not need much material and the worker has a lot of idle time, he may be able to take care of the material supply for more than one line or cell at the same time.
❗ The waterstrider extending over the shop floor.
However, it is also possible to have a point-of-use provider that gets the material from a central warehouse.
This is illustrated below. However, this significantly increases his walking distance.
In these cases, it is highly suggested to give the point-of-use provider additional tools to help him transport more at the same time.
The PoU, water strider, functional management, task at operations solves some common challenges.
A shortlist:
- Who is responsible for information coming in from external but needed at processing.
- Who cares for issues when the assembly artifacts are not consistent for the process.
- Point of interest where problems and options for improvements at the shop floor are.
⚒ U-2.3.4 PoLP Principle of Least Privilege
PoLP autentication, autorisation scheme
Now we have defined roles for:
- accountability for a product service: The CPO, product manager
- responsibilities by activities for product, service: water strider, fucntional manager
It is realistic with advice from others to define with tasks, procedures for instructions what the least privileges needed for those are.
A person can use multiple accounts for minimizing stacking high privileges on normal limited accounts.
An account can have multiple tasks depending an what is approved for procedure types.
Cyber hygiene
❗
What is cyber hygiene and why is it important?
The goal of cyber hygiene is to keep sensitive data secure and strengthen the organization's ability to recover if and when a successful attack occurs.
Many security professionals find achieving an optimal security posture complex and overwhelming, with a plethora of recommendations and a constantly shifting threat landscape.
❗ A risk-based security strategy helps navigate this confusion, enabling security teams to prioritize cyber hygiene practices that most protect the business while still letting it operate efficiently.
While maintaining good cyber hygiene is critical, it is far from easy. Consider the following common challenges:
- The breadth and complexity of IT environments.
- Monotony: a never-ending stream of important behaviors and tasks.
- User buy-in. Starting with this, dismissis IT security teams being in lead.
lists for attentions points:
- practices for users:
Backups, Education, Encryption, Firewalls, Password hygiene, Patch management, Online discretion, Security Software
- practices for organisations:
Allowlisting/blocklisting, Authentication and access control, Backup strategy, Cloud access security broker (CASB), Cloud configuration review,
Cybersecurity asset management, Encryption, Endpoint security, Incident response and management strategy, Password policy, Patch management,
Secure remote access, Security awareness training, Security log management, Security monitoring, Shadow IT management, Threat detection and response
The review for "product" gives is a revival for ideas for promotions and realisations.
💡👁❗ Understand the big difference PM Product Management - PM Project Management.
💡👁❗ Acknowledge the value of products by clear responsibilities by Product Management.
💡👁❗ Have the accountability with authority for product management (CPO) in place.

U-2.4 Safety & quality embedded in services
There is a distraction from the real business goal that information processing should solve.
A desire for easy solutions without management impact.
The reality is a needed culture change in management.
What to look at for the why:
- Processing, lean workunit: one action point of many
- Information Processing: transformations
- Technology: just tools for achieving missions
⚖ U-2.4.1 Safety procedures at an organisation
Safety accountability
The safety, security practices at an organisation is going:
- Although there is a lot attention for technology it is not accountability in technology
- far beyond the scope of a product service scope accountability
💣 Security frameworks like ISO/IEC 27001 always have stated that accountability for safety security is in the boardroom (CEO).
For some reason this was never materialised and they succeeded in ignoring their accountability not being held responsible by regulators.
Comply to regulations, Dora NIS2
With NIS2 and Dora the cybersecurity should brought at a level that the expected risk/impact is at an acceptable level.
What is new:
- Accountablity: Clear set to executives of the organisation for important services.
- External providers (Dora): When part of a comitted service, included for all activities.
❶ The recent years it it obvious data breaches are a an accountablity for the organisation.
The accountablity for safety is changing from a volontary advice to clear legal mandatory at the leaders level. Examples:
- NIS-2 (Directive (EU) 2022/2555)
The number, magnitude, sophistication, frequency and impact of incidents are increasing, and present a major threat to the functioning of network and information systems.
As a result, incidents can impede the pursuit of economic activities in the internal market, generate financial loss, undermine user confidence and cause major damage to the Union’s economy and society.
Cybersecurity preparedness and effectiveness are therefore now more essential than ever to the proper functioning of the internal market.
Moreover, cybersecurity is a key enabler for many critical sectors to successfully embrace the digital transformation and to fully grasp the economic, social and sustainable benefits of digitalisation.
- Dora (Regulation (EU) 2022/2554)
In the digital age, information and communication technology (ICT) supports complex systems used for everyday activities.
It keeps our economies running in key sectors, including the financial sector, and enhances the functioning of the internal market.
Increased digitalisation and interconnectedness also amplify ICT risk, making society as a whole, and the financial system in particular, more vulnerable to cyber threats or ICT disruptions. ...
To date, due to the ICT risk related provisions being only partially addressed at Union level, there are gaps or overlaps in important areas, such as ICT-related incident reporting and digital operational resilience testing,
and inconsistencies as a result of emerging divergent national rules or cost-ineffective application of overlapping rules. ...
As the Single Rulebook has not been accompanied by a comprehensive ICT or operational risk framework, further harmonisation of key digital operational resilience requirements for all financial entities is required. ...
❷ What is new:
- duty of care Carry out a risk assessments, the base for appropriate measures.
- reporting obligation: dedicated incidents to the supervisor within 24 hours.
- Registration obligation Applicable entities for NIS2, Dora are required to register.
- Supervision Compliance obligations, e.g. the duty of care, reporting, are examined.
Existing security frameworks are not obsolete, they are the ones for appropriate measures.
A regulation is immediate active, a directive has an obligation to the member state.
❸ Should the persons in the boardroom being accountable doing the work themself?
The assumption is they are enabling the work is done according the guidelines / regulations and are validating that is it done by closed loop reports.
Product Management is including a lot, aside line functionality also safety. Some of the activities will land there but not all of them.
⚖ U-2.4.2 Safety practices at an organisation
Who is doing what?
The existing frameworks are helpful in expectations for this by categorizations.
Categorization
There is a lot to do, a categorziation suitable to metadata identifications is helful in simplifying the work.
A good starting point is (NIST CSF 2.0):
- Govern is something directly under controle by executives
- Identify is delegated to risk Managemnent at high abstraction level
- Protect is generic for the organisation supported by advices of the CISO
- Detect, Respond, Recover is for the product related service at the CPO for others at facilities management.
CSF 2.0 Nist
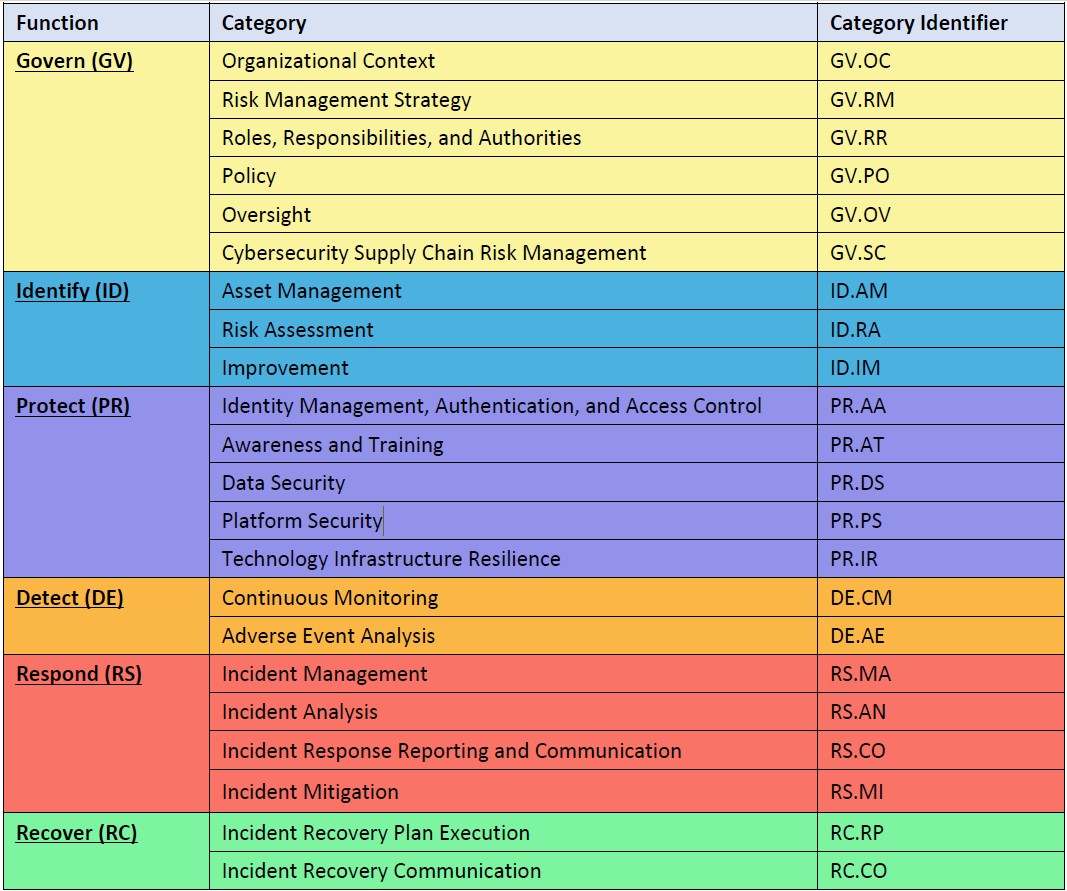
Recognized being important but 😱 lost in space
One would assume a regulation with a supervisor would result in clear operational instructions.
This assumption is not true for several reasons.

The situation:
- A safe working environment is seen as a cost factor, not adding value.
Cyber security is going with a lot of investment costs.
- Improving a productline, gets a lot of attention but lacking the real why's for the improvements.
What I am indicating is missing the focus for:
- Quality of the administrative/cyber processing line.
- Safety of the administrative/cyber processing line.
- Accepting short term approaches, not understanding the PDCA.
❓ Question: How would the core product be in quality quantity continuity safety and cost with all this kind of uncertainties?
Involved persons 😱lost in space
The standard hierarchy (strategy tactical operations) gives a process by two loops.
The figure look sensible until asking:
- Who are those managers? CPO product managers, Facilities management, HR management, IT Service desk management?
- Who are those PR actioners? water striders functional management, technical staff, users at operational values stream, IT service desk?
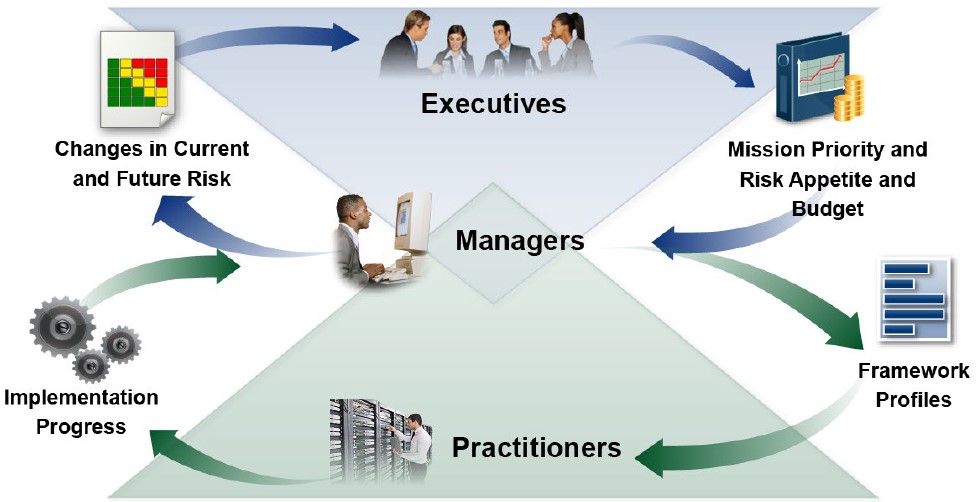
A figure,
(NIST CSF 2.0)
See right side
⚖ U-2.4.3 Risk management principles
risk frameworks
There are not that many frameworks with the focus on risk. However for financial services risk management is quite mature.
After some horrific incidents regulations were set for this and still expanding by more incidents.
credit risk
💰 Risk management analytics offers opportunities to improve decision-making ability and ensure compliance with requirements possibly related to the organization's credit risk management policy and external regulatory systems, often risk analytics is implemented at several different levels in the organization.
Developing a credit policy can be a business issue, in which case decisions are made in the so-called in the first line of defence, but on the other hand, the risk management function participates in ensuring that the credit decisions made are in line with the agreed credit policy and the operational policy of risk management.
💰 Different accounting standards often set requirements for how different provisions for bad debts can be recorded. The organization must be familiar with the principles of the accounting standards followed in its area (for example, US FASB CECL vs IFRS 9) for evaluating loan loss provisions and their accounting treatment.
It is necessary to use resources for information management and information management in order to achieve the goals for each of the areas presented above, but on the other hand, it should be noted that these target areas often use the same information sources, with slightly different goals.
➡ One international reference framework for risk management information management is BCBS 239 – principles (Basel Committee on Banking Supervision – Principles for effective risk data aggregation and risk reporting) from 2013.

BCBS 239 Principles
❸ bcbs239
(January 2013, Bank for international settlements) The principles are generic when not seeing "bank".
The Principles cover four closely related sections:
- Overarching governance and infrastructure (1,2)
- Risk data aggregation capabilities (3,4,5,6)
- Risk reporting practices (7,8,9,10,11)
- Supervisory review, tools and cooperation (12,13,14)
- Governance data aggregation capabilities and risk reporting practices should be subject to strong governance arrangements consistent with other principles and guidance.
- Data architecture and IT infrastructure – design, build and maintain data architecture and IT infrastructure which fully supports its risk data aggregation capabilities and risk reporting practices not only in normal times but also during times of stress or crisis, while still meeting the other principles.
- Accuracy and Integrity be able to generate accurate and reliable risk data to meet normal and stress/crisis reporting accuracy requirements.
Data should be aggregated on a largely automated basis so as to minimise the probability of errors.
- Completeness be able to capture and aggregate all material risk data across the group.
Data should be available by business line, legal entity, asset type, industry, region and other groupings, as relevant for the risk in question, that permit identifying and reporting risk exposures, concentrations and emerging risks.
- Timeliness be able to generate aggregate and up-to-date risk data in a timely manner while also meeting the principles relating to accuracy and integrity, completeness and adaptability.
The precise timing will depend upon the nature and potential volatility of the risk being measured as well as its criticality to the overall risk profile.
The precise timing will also depend on the specific frequency requirements for risk management reporting, under both normal and stress/crisis situations, set based on the characteristics and overall risk profile of the bank.
- Adaptability be able to generate aggregate risk data to meet a broad range of on-demand, ad hoc risk management reporting requests, including requests during stress/crisis situations, requests due to changing internal needs and requests to meet supervisory queries.
- Accuracy - Risk management reports should accurately and precisely convey aggregated risk data and reflect risk in an exact manner. Reports should be reconciled and validated.
- Comprehensiveness - Risk management reports should cover all material risk areas within the organisation.
The depth and scope of these reports should be consistent with the size and complexity of the bank’s operations and risk profile, as well as the requirements of the recipients.
- Clarity and usefulness - Risk management reports should communicate information in a clear and concise manner.
Reports should be easy to understand yet comprehensive enough to facilitate informed decision-making.
Reports should include meaningful information tailored to the needs of the recipients.
- Frequency The board and senior management (or other recipients as appropriate) should set the frequency of risk management report production and distribution.
Frequency requirements should reflect the needs of the recipients, the nature of the risk reported, and the speed, at which the risk can change, as well as the importance of reports in contributing to sound risk management and effective and efficient decision-making across the bank.
The frequency of reports should be increased during times of stress/crisis.
- Distribution - Risk management reports should be distributed to the relevant parties while ensuring confidentiality is maintained.
- Review - Supervisors should periodically review and evaluate compliance with the eleven Principles above.
- Remedial actions and supervisory measures - Supervisors should have and use the appropriate tools and resources to require effective and timely remedial action to address deficiencies in its risk data aggregation capabilities and risk reporting practices.
Supervisors should have the ability to use a range of tools, including Pillar 2.
- Home/host cooperation - Supervisors should cooperate with relevant supervisors in other jurisdictions regarding the supervision and review of the Principles, and the implementation of any remedial action if necessary.
Reusing BCBS 239 Principles
The principles are ready for use at any risk management questions.
The data processing for risk management is analytics, using business information but is not about improving the product, describing something of the product.
The goal and usage of data processing is very different although sharing of technology for doing analytics is possible.
This review for managing risk at a product gives a change by ideas for managing functionality and functioning realisations.
💡👁❗Using a mindset to improve safety cybersecurity based on product accountabilities.
💡👁❗Promotion for a safe environment intangible part of the shop floor.
💡👁❗How to achieve a safe environment using existing knowledge and guidelines.

U-2.5 Service lines functionality functioning
Optimising "services: cyber/adminstrative" is the goal behind USM.
Although it is not explicitly stated in the USM pinciples it is using lean principles.
Value stream processes are core business lines for services.
Where to pay attention on:
- T - Operational technology services
- I - Information processing services
- P - Customer excellence services
⚒ U-2.5.1 Services, processes, practices, instructions
The USM Service, processes
Process model
If we test the 'processes' from all current frameworks, standards, and reference architectures against these 10 requirements, it can be demonstrated that they all describe combinations of people, process and technology: the what, the who and the how.
Therefore, they all fail the very first of the 10 requirements.
They actually describe practices, and practices are not processes: practices are derived from processes by adding the who and the how to the what. ...
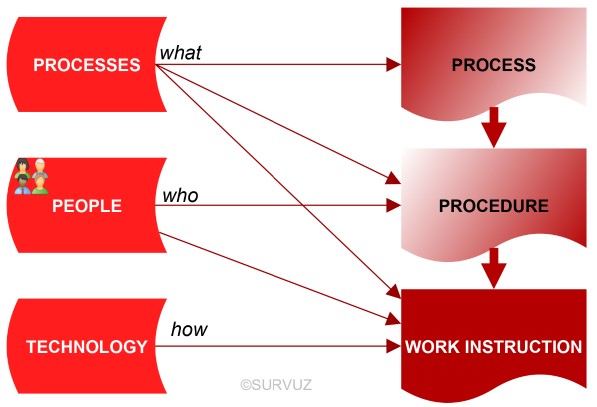
The difference between:
⚖ processes
⚙ Procedures practices
⚒ Work instructions
The detailed descriptions in different aspects for differences is more clear in a figure (see left side).
Confusion:
Most "processes" are internal affairs for the service provider, and as such, they are only part of the customer-facing processes.
In a process model that meets all the 10 requirements, performance is achieved with workflows: composite flows of activities, which consist of non-overlapping fragments of individual processes from the integrated process model.
Some process requirements aren't clear understandable, excerpt details:
- “A process can be divided into sub-processes, but that does not change the process.”
👉🏾 E.g., software development is an internal activity. The customer couldn’t care less how the functionality is generated, as long as it is.
- “A process model organizes the processes.”
👉🏾 Enterprise Service Management requires one captain on the ship
👉🏾 In a complex environment, interoperability is key
- “An integral process model includes all service management activities.”
👉🏾 An issue: Project management is not product management.
👉🏾 See the organization through the eyes of one integrated management system.
- “In an integrated process model, each activity occurs only once.”
👉🏾 Issues: "Best practices", local organizational structure, local selection of tools.
👉🏾 Start with the things you do to realize your organization’s mission and goals
The USM Service, process model
🎭❗ Principle:
Removing all who and how from these practices then leads to the core material of a process architecture: only the what.
🎭 A solution, of multiple alternatives:
In that process model we find only five processes that are independent of the line of business of the organization.
Four of these processes are reactive: they are triggered externally, by the customer.
These reactive processes are used to respond to the customer's demand.
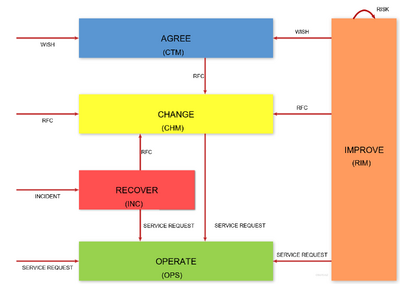
In a figure see right side:
- Agree (Contract Management - CTM):
drawing up and maintaining service agreements and steering their deployment.
- Change (Change Management - CHM):
controlled development and release of changes to the infrastructure.
- Recover (Incident Management - INC):
repair and recovery of the service as agreed.
- Operate (Operations Management - OPS):
planned execution of all operational actions for the agreed service and the monitoring of the performance of the infrastructure and all its components.
- Improve (Risk management - RIM):
prevention of detrimental effects to the agreed services (mitigating threats).
structural improvements promotion in the agreed services (fostering innovations).
Reasons for an alternative:
🤔 Missing is the service owner.
🤔 Proactive improvements avoiding failures is better than waiting them to happen.
🤔 The requirement for monitoring is neot seen in the USM model.
⚒ U-2.5.2 facility - support, functionality - functioning
The USM Service
A classification for tasks activities at
Process model is a well thought interesting statement.
Functionality- functioning is a better one than design - build or theoretical practical although they are all having the same intention.
Facility - Support
Composition of a service:
- facility: the 'something' that is made available to a customer in the course of service delivery and that is supported by the provider in its use by that customer
- support: the assistance that a customer receives from the provider when using the facility
A service involves a customer who is interacting with that facility (the 'use' by the user).
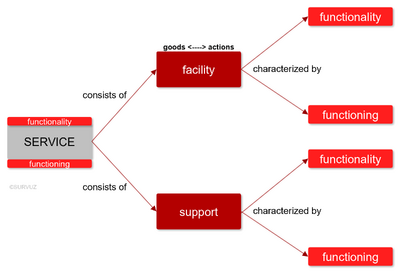
Two by two:
- Functionality
- Functioning
See figure right side
Facility
A facility is always a mix of goods and actions:
- Goods may be tangible and intangible, visible and invisible. E.g., in passenger transport of the type of 'railways', a tangible good is the train that brings you from A to B, and an intangible good is the travel app that shows you at what times these trains depart and arrive.
In telephony services, the mobile phone in your hand is visible, but the network that enables the phone calls is invisible.
- Actions may involve anything that is done by people, e.g. the actions of a masseur in a massaging service, the actions of a consultant in a consulting service, the actions of a babysitter in a babysitting service. These actions normally are visible, but intangible.
The support
The support involves the response to support requests submitted by the customer (user). These support requests trigger the reactive processes of the service provider.
Service evaluation
- IV functionality of the facility: specifies what a facility can do, or what a user can do with it.
- III functionality of the support : specifies what kind of support the user gets.
- I functioning of the facility: specifies how well the facility performs its functionality.
- II functioning of the support: specifies how well the support is delivered.
Reasons for an alternative:
🤔 Missing in the USM service soultion is what about faclity and support.
🤔 The tweak done is to have a fit with the SIAR model (Pull-Push PDCA DMAIC).
The USM goal
🎭
We need at least a control approach at an end-to-end level: an Enterprise Service Management strategy that focuses on complexity reduction.
provides the concept of the universal link that can be used to build endless supply chains and service ecosystems, based on a simple service management architecture, with only customer-relevant processes.
🎭
effective and efficient collaboration requires normalization of the way the teams contribute to the enterprise goal.
And normalization requires some level of standardization, especially on the aspect of each team’s management system.
🎭
Service management architecture: The fundamental organization of a service management system in its components, their relationships with each other and the environment, and the principles that guide its design and development.
⚒ U-2.5.3 The Service quantum
Incompleteness USM
What is not mentioned although clearly touched:
- Accountability (Service Management - SMA):
Accountability for the service from provisioning to customer delivery.
- The supoort domain from specify (functionality) to realize (functioning)
Adding those into visualisations for two different types. One for functionality, design, and one for functioning, executing.
Executing service deliveries
The process quantum for functioning:
- IV The request is coming in from a customer
- III Processes OPS and CHM are used to organize in fulfilling the request.
Supporting processes SMA, INC for doing the right things and CTM RM/INC for doing things right.
- I After knowing what is to do, operations realizes the fulfilment for the request.
- II The result is the product for the customer.
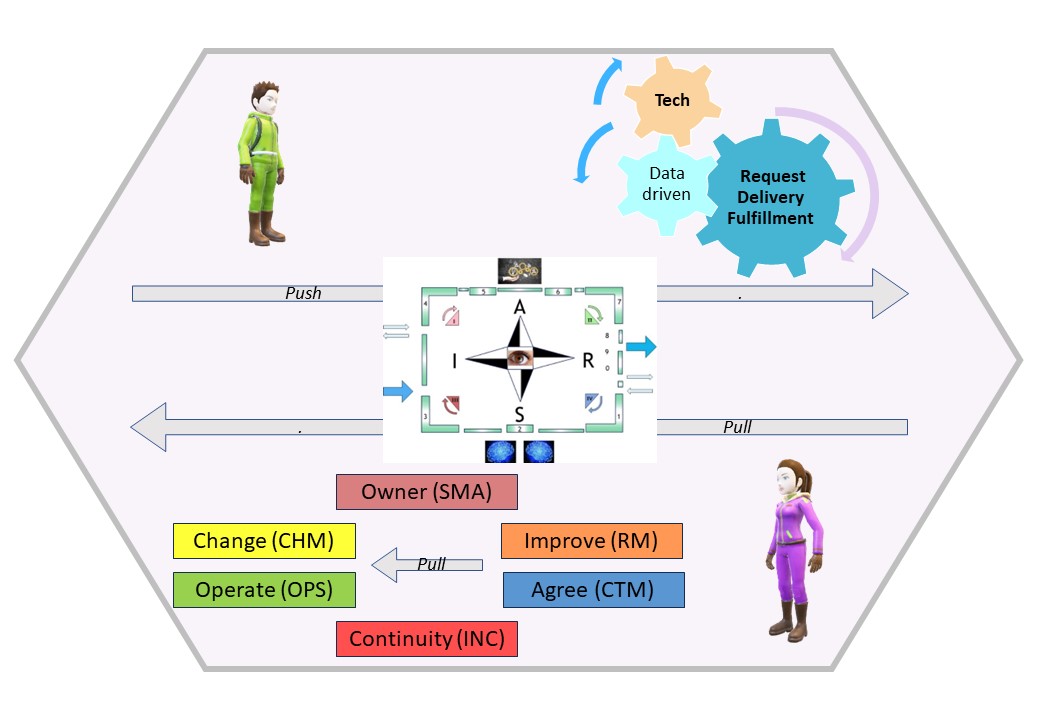
In a figure see right side:
In data mesh this is the operational plane.
Designing service deliveries
The process quantum for functionality:
- IV The request is coming in from a service owner or proactive by closed loop results
- III analyze Ideate for getting to know several options what to do.
- I Processes CHM and INC/RM are used to organize in fulfilling the request for doing the right things.
Supporting processes SMA, INC for for doing things right.
- II The result is a service specification (CTM) adjusted or new this is also realised for operations (OPS).
The result is a specification of the product intended to delivered to a customer.
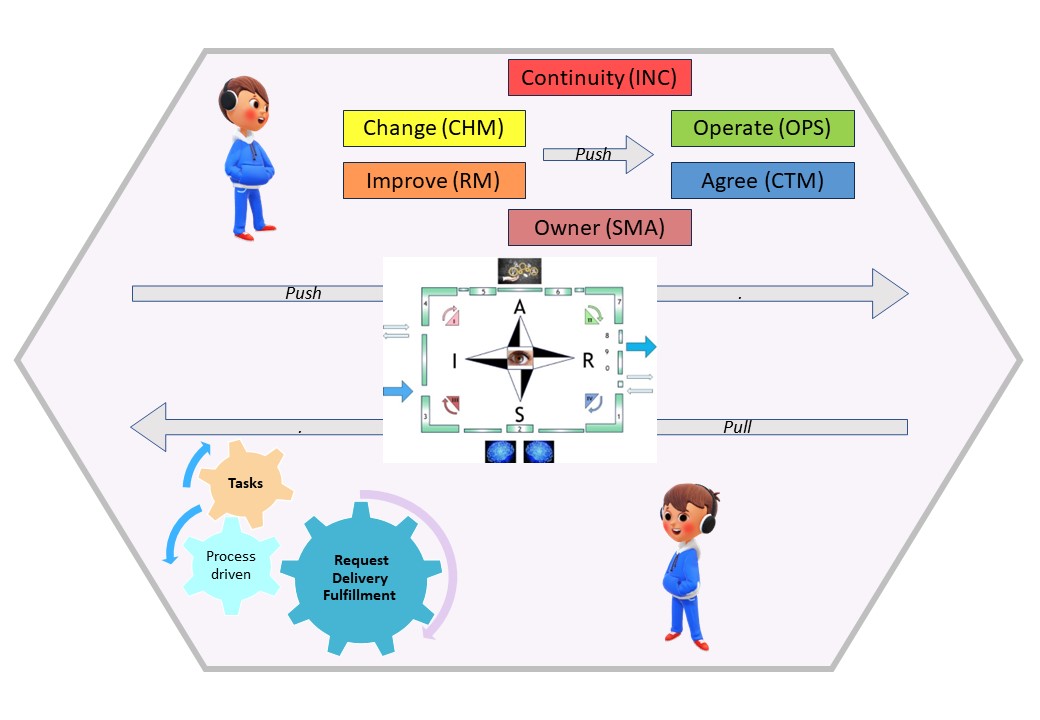
In a figure see right side:
In data mesh there are parts of this, the closed loop, in the analytical plane.
This restructured version of USM principles gives many new ideas for promotions and realisations.
💡👁❗Promotion how to differentiate between processes within services.
💡👁❗Promotion how to accept and start change, improvements .
💡👁❗Using a mindset to analyze improvements out of several options, a lean culture.

U-2.6 Maturity 4: Change Services in control
"Managing services" is a prerequisite for "processes: cyber/adminstrative".
The focus should be on the value stream services and processes. It starts by knowing the shop floor.
From the three TIP, interrelated scopes:
- ❌ T - Operational technology services
- ✅ I - Information processing services
- ❌ P - customer excellence services
⚖ U-2.6.1 Safety intangible at the internal organisation
Requirements to set, document & validate
Information processing culture is lacking the culture for structured processes by layers and is lacking culture for sufficient explanations.
😉 The jabes proposal is about structuring processes. The documental architecting engineering and operating has to cover multiple attention points.
👉🏾 Use all these four intagible for product and at the processing lines of prodcuts.
- Indispensable information part: security, safety.
- Information Quality, Integrity, Timely.
- Impact on persons for the good and bad.
- Explainable business Rules, Algorithms.

In a figure:
See right side
⚖ U-2.6.2 Clear safe assembly lines, deliveries, by the organisation
Whether the process in the information is a simple recipe, classic instructions, or diffuse complex (algorithm analytics) one, doesn't really matter.
Advanced exchange multiple products one several product lines in a figure:
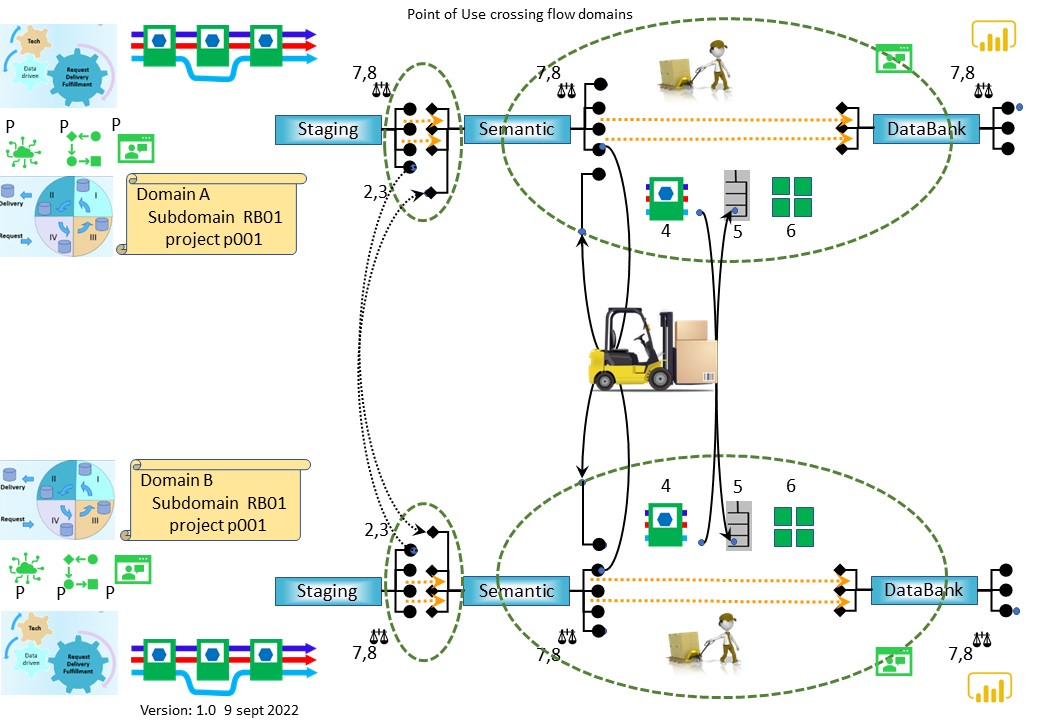 👉🏾
👉🏾 Translate the logical floorplans to easy understandable activities, practices, routines.
⚒ U-2.6.3 Product: Value creation for Customer, Requestor, Data subject
How: Product principles
There are several gaps for product management althought they should not be there.
There is a lot of knowledge and many good guidelines.
An ateempt to recap the product management challenge:
👉🏾 Using these nine aspects in 3*3 planes.
There is a difference between theory and realisation, the same aspects have different perceptions from another position, other perspective.
Difficulties in perception using a top down or bottom perspective helps in understanding decreasing those difficulties.
Selecting nine topics, ordering those in two 3*3 planes, is a new idea.
In the end there will be a multidimensional cubicle model view with three axis.
Top-down theoretical view:
The figure,
see right side
Bottom-up practical view:
The figure,
see right side
Another one is "data", analytics, business intelligence.
There are 3 closed loops for managing a product, the processing line:
- functioning of the service (operations)
- Understand the floor, work being done by doing analyses
- Understand the floor, work being expected by doing analyses
- functionality of the service (design, technical and functional)
- Getting information: What are the transitions changes planned?
- Get to know: profits & losses last 3 years, the stage of the product
- achieving the purpose of the service, for the good bad and ugly:
- direct customer feed back
- external information: demand, satisfaction, market change
This type of doing analytics for the product is competing with those for lean processing.
Bamboozled
"If we've been bamboozled long enough, we tend to reject any evidence of the bamboozle.
We're no longer interested in finding out the truth. The bamboozle has captured us.
It's simply too painful to acknowledge, even to ourselves, that we've been taken.
Once you give a charlatan power over you, you almost never get it back.” - Carl Sagan
⚙ U-2.6.4 Safety Capabilities: managing uncertainties & risks

Asking an oracle is a way to convince presumed decisions by assumptions is of all times. Ambiguity is to avoided.
😉 Alignment or decisions by help of external advisors sounds good.
Risks are by nature uncertaintities. managing uncertaainties is balancing many possible sceneraios change and their impact.
This is not an binary yes/no advice, worse when new information is added scenarios could change dramatically.
👉🏾 Needed: culture Accepting imperfection while seeking perfection.
⚙ U-2.6.5 The goal & maturity of the organisation as service provider
PDCA - DMAIC - SIAR , lean
This is the second image: dynamic, static & stages for flow & control.
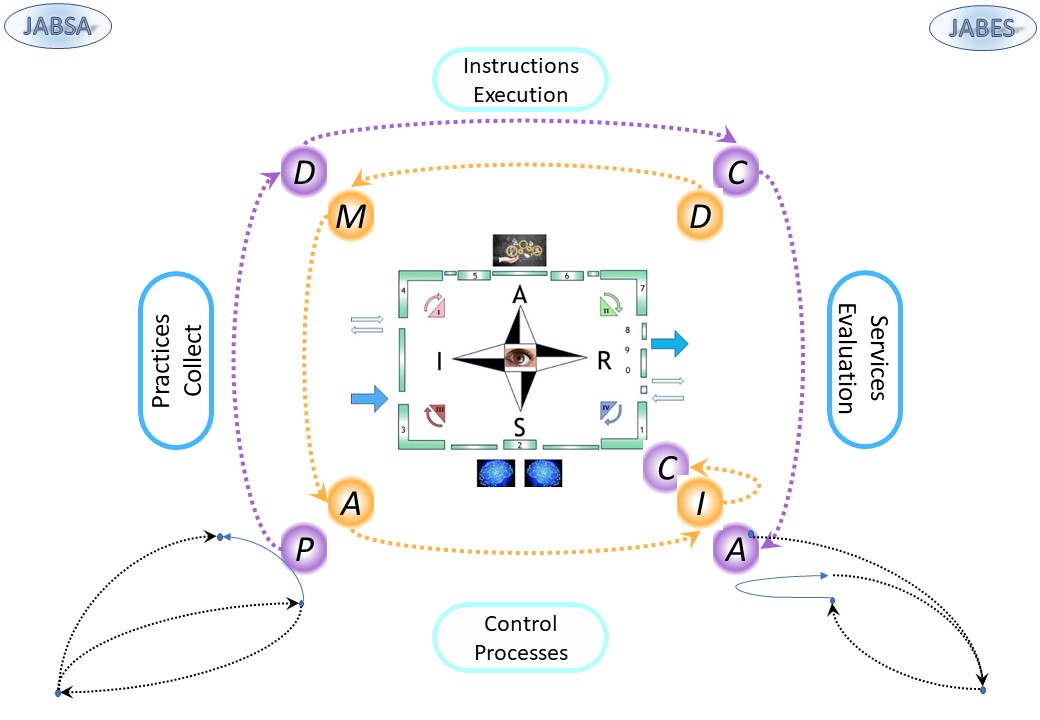
Change:
PDCA
DMAIC
- define, measure,
- analyze, improve
- control
SIAR
- situation,
- input
- activity/analyse
- result/request
How the areas with cycles, a mindset to external service delivery:
- functionality: Processes, Practices, Instructions, Services
- functioning: Control, Collect, Execution, Evaluation
It is setting a direction for goals matching the way of working.
What is needing for improvements is getting clear although the choices in priorities are left at good luck.
What the blocking constraints are and where the efforts are being spent on are not valuated.
😉 Improving requires acceptance to unlearn and learn consciously.
👉🏾 Needed is a culture mindset for understanding what the options to improve are.
PDCA DMAAC puzzle in meaning, understanding
In the image there are vertical - horizontal objects mentioned what to change, the diagonals are representing action how to change.
The PDCA DMAIC are promoted in a one way direction and not being combined.
- Pro active:
- Inspire, Appraise Mobilize, Deliberate
Reverted DMAIC, goal: getting an idea and evaluating what could be done
- Adjust, Certify, Decompose, Propose
Reverted PDCA, goal: adjusting results quality to a more appropiate level
- Reactive:
- Plan, Do, Act, Check
PDCA , goal: implemeneting a defined idea
- Define, Measure, Analyze, Improve, Control
DMAIC, goal: correcting result issues that are not appropiate
Communication over the diagonals is not forbidden, these are lines in the floorplans.
⚖ U.2.6.6 Short checklist floor impediments
Need having solved:
- ❌ ✅ Shop Floor accountabilities.
- ❌ ✅ Shared glossary with cooperation for technology
- ❌ ✅ Responsibility for clear security at the shop floor.
- ❌ ✅ Responsibility for managing processes at the shop floor.
These are to be understood solved and managed by management at the high levels. This can be measured by maturity metrics.
The usual situation is: none of them is in place. Worse, there is even no awareness, CMM level-0.
U-3 Realisations improved value streams, reduced risks

U-3.1 Simple information & services
Running services is without a clear defined craftmanship.
Variety volatility are too high in the very diverse number of circumstances.
Decision makers are needing information, using other persons skills to help in underpinned decisions.
General focus areas:
- 🎭 Structure of services
- 🎭 Culture in for services
- 📚 Missions & visions for services
- 📚 Processes & information by services
⟳ U-3.1.1 Dualities: Materialised - Transforming
⚖ Complex numbers
Understanding and teaching complex numbers (Ait Jaokar)
👓 In high school, you are taught complex numbers as a type of number that goes beyond the familiar real numbers (like 1, -3, or 4.5) we use every day.
They are made up of two parts: a real part and an imaginary part.
'i' is defined as the imaginary unit and is the square root of -1.
Then you are taught that you can perform various operations on complex numbers because you can think of complex numbers as points or vectors on a plane called the complex plane.
... Complex numbers provide a powerful mathematical framework to describe and analyze physical phenomena that involve two interrelated components, often oscillatory or wave-like.

⚖ The why of complex numbers at information processing
There are two components in processing information:
- Data materialisations, representing information
- Transformations, changing the information
If we could measure each of them by numbers the complex number mathematics would be useable.
Imagination: the transformation is changing the intention, position, content of information to something not reachable before.
- On data materialisations we can use statistical inference
- For Transformations there is a model (machine learning) inference
Challenges in machine learning
Why is machine learning challenging for some engineers? (ajit Jaokar 2024)
I do not refer to software or AI engineers.
I am referring to traditional engineers - ex mechanical / electrical etc working in those industries.
In a nutshell - engineers have a different mindset due to their perspective of Physics based modelling and simulation - which do not directly co-relate to data science (ML DL).
😱 ❓ Uhh .. what is going on here?
Electrical, electronics engineers are used to working with complex systems, wave-like systems improving what tis possible, continuously working with preferable data gathered by measuring what is going on.
 In engineering, Physics-based modelling often involves deriving equations, from first principles to describe the underlying physical processes.
A wind tunnel is an example of physics based modelling.
In engineering, Physics-based modelling often involves deriving equations, from first principles to describe the underlying physical processes.
A wind tunnel is an example of physics based modelling.
In contrast, machine learning relies on data-driven approaches, which can be a paradigm shift for engineers more accustomed to analytical solutions.
Machine learning is dependent on large volumes of data for training models.
Traditional engineering approaches do not place as much emphasis on data because many real-world problems in physics are described by linear or well-defined mathematical models.
Machine learning, especially deep learning, deals with non-linear and complex relationships that are not easily representable using traditional mathematical equations.
beginners-guide-to-aeronautics Is the reality.
What is under control by mathematic rules is preferable done by data processing. The model is fulled with new data showing the results visualised by data.
The last verification of this is a correct new model approach goes by physical simulations but only in avoiding as much as possible the high impact by mistakes.
 There are some more considerations
There are some more considerations
- In engineering, domain knowledge is used for feature engineering.
- Machine learning and deep learning try to automate this step.
- Traditional engineers are accustomed to interpretable models where each parameter has a physical meaning.
- Some machine learning models, especially complex ones like deep neural networks, are often considered "black boxes," making it challenging to interpret how they arrive at specific decisions.
- Traditional engineering models are often validated against theoretical principles and tested in controlled environments.
- Machine learning models require careful validation and consideration of their generalization to new, unseen data, which can be a novel aspect for engineers.
A lot of arguments that are indicating the opposite. Machine learning should learn more from classic engineering understanding better the system instead of hoping some API will solve it all.
Despite these challenges, the integration of machine learning with traditional engineering approaches holds great promise for solving complex problems and optimizing systems - especially when physics based modelling is not possible in some edge cases.
😉 Thus, machine learning focuses on learning patterns and making predictions from data without explicit rule-based programming.
Simulation involves creating rule-based models that replicate the behaviour of real-world systems.
Materialised information Inference
Assuming quality, trustworthiness are at known levels, what tells the information?
Understanding statistical inference (ajit Jaokar 2024)
👓 In statistical inference, it is assumed that the underlying distribution of the data can be known.(is knowable).
👓 Machine learning inference is the process of using a trained machine learning model to make predictions on new, unseen data.
This is the stage where the model, which has already been trained on a dataset, is deployed to perform tasks such as classification, regression, object detection, etc., in real-world scenarios.
❗ 😲 It is exaggerated a model is only possible by machine learning (ML).
Instructions for a model, rules, given by a leader by good feelings is acting the same.
The difference is only those good feelings are missing the proof by what is in information.
❗ 😲 In fact ML is replacing the unexplainable freedom human decision makers have with all their privileges.
They are getting evaluated and still accountable leaders.
What are the steps involved in statistical inference?
Because of the need for the underlying distribution to be knowable, statistical inference involves two steps:
-
Firstly checking if the models assumptions about the underlying distribution are reasonable.
This is mostly achieved using visual tests and
-
Goodness of fit tests are statistical tests used to determine how well a statistical model fits a set of observations.
Essentially, they help assess whether the observed data matches the expected data distribution based on a specific model.
These tests are crucial for validating the assumptions of statistical models and ensuring their accuracy in representing the underlying data.

⟳ U-3.1.2 Inference Statistical - Machine Learning
Culture clashes
Understand the maths of data science (ajit Jaokar 2024)
👓 Everyone is traditionally taught that statistics is the foundation of machine learning. It is not that simple.
Data models are rarely used in ML DL.
👓 The approach is that nature produces data in a black box whose insides are complex, mysterious, and, at least, partly unknowable.
What is observed is a set of x's that go in and a subsequent set of y's that come out.
The problem is to find an algorithm fx such that for future x in a test set, fx will be a good predictor of y.
❗ 😲 This is describing just "fitting the line" by bacl box assumptions using api's.
I would prefer using determined set of predictors of combined dependent correlated features. those are more stable and predictable.
The goals in statistics are to use data to predict and to get information about the underlying data mechanism.
In some situations they are the most appropriate way to solve the problem. But the emphasis needs to be on the problem and on the data.
😱 ❓ Uhh .. what is going on here?
A seen distribution would be prove for some assumed solution?
How to Lie with Statistics (D.Huff 1954)
Themes as: "Correlation does not imply causation"
, an example of a questionable-cause logical fallacy, in which two events occurring together are taken to have established a cause-and-effect relationship.
The assumption that A causes B simply because A correlates with B is not accepted as a legitimate form of argument.
It is weird to see even scientist are using that not legitimate argumemtation to convince other people.
Model, transformations Inference
understanding statistical inference (ajit Jaokar 2024)
Statistical inference is the process of drawing conclusions about a population's characteristics or parameters based on a sample of data taken from that population.
- It involves using statistical methods to estimate population parameters, test hypotheses, and make predictions.
- The existence of a population and a sample are key to statistical inference.
- The entire group of individuals or observations that we are interested in studying is the population.
❗ For statisticians anything beyond describing the population is a black box.
Example: statisticians are able to create nice statistics on construction materials for an object and are at the same time clueless for the engineering of the construction.
The "statisistical proof" assumption:
- A subset of the population selected for study. Inferences about the population are made based on the sample data is called the sample.
- A Parameter is a numerical characteristic of a population (e.g., population mean, proportion).
- A statistic is a numerical characteristic of a sample (e.g., sample mean, proportion) used to estimate the corresponding population parameter.
- A Point Estimation involves using sample data to calculate a single value (point estimate) that serves as a best guess for an unknown population parameter (e.g., sample mean as an estimate of the population mean).
- Interval Estimation involves calculating a range of values (confidence interval) within which the population parameter is likely to lie (e.g., 95% confidence interval).
- A Null Hypothesis (H0) represents: statement of defined effect or assumed state.
- The Alternative Hypothesis (H1) represents the opposite of H0.
Finally, Type I Error involves incorrectly rejecting the null hypothesis when it is true (false positive).
Type II error is failing to reject the null hypothesis when it is false (false negative).

Model, transformations Inference
Machine learning vs Statistics (ajit Jaokar 2024)
To clarify, of course, statistical ideas are used in machine learning (ML) and deep learning (DL) but the two practises differ fundamentally when it comes to inference.
when statisticians say that machine learning and deep learning models are fundamentally unknowable (black box) it sounds like something bad.
❗ It is the same black box statisticians always had to and will be to face, they are no: surgeries, engineering, matter specialist.
ML and DL techniques lead to altogether new types of applications, for example based on image recognition.
Lives have been saved using these techniques that do not by definition require the underlying distribution to be known.
to summarise:
- Statistical Inference:
Based on known probability distributions and simpler models, suitable for smaller datasets, and provides clear interpretability and measures of uncertainty.
- ML Machine Learning Inference:
Data-driven approach that uses a variety of algorithms to learn from data, requires larger datasets, and includes both interpretable and complex models.
- DL Deep Learning Inference:
A specialized subset of machine learning that uses deep neural networks to model complex patterns, requires very large datasets and computational power, and is less interpretable.
What do we have up to now?
- Human decision makers are accepting 20% defects (pareto principle). When chosen the wrong option they are causing 80% defects.
- Support by statisticians in hindsight 5% will are wrong defect decisions. The overrating of P-values is a scientifical problem.
- Using data science there is no closed loop for evaluating failures defects. The claim, underpinned by confusion matrices, is only doing better cheaper decisions than humans.
Using statistics for undestanding the population and what the effects by services, the initial purpose, are is making more sense.
The technology is not a blocking factor anymore for follwoing any case individual.

⟳ U-3.1.3 Inference purpose information processing
Materialised information Inference
IID in machine learning (ajit Jaokar 2024)
In machine learning, "IID assumption" stands for "Independent and Identically Distributed."
The assumption of independence implies that the generation of any data point in a dataset does not influence and is not influenced by the generation of any other data point. In other words, each data point is generated without regard to the others.
And how do you know that? Through statistical tests and analysis.
And therein lies the touchpoint between the two approaches.
Just add:
- Use engineering insights reducing brittelness by combining correlated features.
- Use statistics on closed loops evaluating the purpose.

Underfitting - overfitting
Bias variance tradeoff - a simple analogy (ajit Jaokar 2024)
Underfitting:
- is a modeling error that occurs when a machine learning model is too simple to capture the underlying patterns in the data.
- This leads to poor performance both on the training set and the test set.
Underfitting can be identified when a model has high bias and low variance, meaning it makes strong assumptions about the data and fails to learn from the training data effectively. This results in a model that does not perform well even on the training data, let alone on new, unseen data.
Overfitting:
- is a modeling error that occurs when a machine learning model learns the training data too well, capturing noise and random fluctuations rather than the underlying patterns.
- This leads to poor generalization to new, unseen data, as the model becomes overly complex and specific to the training dataset.
Overfitting is characterized by low bias and high variance, meaning the model makes few assumptions and fits the training data very closely but performs poorly on test data.
When the purpose is understood the level of fitting will tell something how appropiate the model is, how appropiate the pupose is.
This unique view on data, information processing gives several ideas why there ar that many difficulties in understanding.
💡👁❓Avoiding classic engineering skills and managing risks by chance-impact, why?
💡👁❓Not using classic statistics for evaluation product line purpose results, why?
💡👁❓Underfitting overfitting no matter of model origin. Model: a specified purpose.

U-3.2 Interactions in a complicated landscape
Running services is without a clear defined craftmanship.
Variety volatility are too high in the very diverse number of circumstances.
Decision makers are needing information, using other persons skills to help in underpinned decisions.
General focus areas:
- 📚 Missions & visions for services
- 📚 Processes & information by services
- 🎭 Structure of services
- 🎭 Culture in for services
⚖ U-3.2.1 Perspectives activies in the centre

Understanding changing perspectives
When there is perspective changes between functionality and functioning the goals to achieve are changing.
Having a fixed starting point for the pull-push and PDCA, DMAIC cycles the axis are changing, a mirror over the product diagonal.
The interactions over horizontal and vertical lines are also changing. it is who, task activity, is taken initiative who, task activity is following in what path order.
Functionality internal

🎭 For designing product quality internal two important central activities are about budget and access.
🎭 For designing product usage internal other two important central activities: the service and staffing people.
❗⚠ In the context of working at design there is different context to working for usage.
👉🏾 Impact Interactions: hard to underestimate.
Functioning internal
🎭 For designing product quality internal two important central activities are about budget and access.
🎭 For designing product usage internal other two important central activities: the service and staffing people.
❗⚠ There is a different location, change in ordering in connections to designing the product.
👉🏾 Impact Interactions: hard to underestimate.
Functionality external

🎭 For designing product delivery external two important central activities are about infrastructure and technical support.
🎭 For designing product usage internal other two important central activities: planning realization and fullfilling request delivery.
❗⚠ In the context of working at design there is different context to working for usage.
👉🏾 Impact Interactions: hard to underestimate.
Functioning external
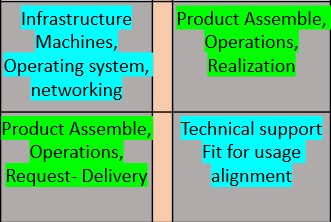
🎭 For designing product quality internal two important central activities are about budget and access.
🎭 For designing product usage internal other two important central activities: the service and staffing people.
❗⚠ There is a different location, change in ordering in connections to designing the service.
👉🏾 Impact Interactions: hard to underestimate.
⚖ U-3.2.2 Perspectives activies over axis

Understanding changing perspectives
When there are perspective changes between internal and external the goals to achieve are also changing.
This has an effect in ordinal orderings at axis and the ordinal order in categorisation.
- The where - what are exchanged and the who - which are exchanged.
- Backend - frontend the first level with pull-push at the other side.
- What how Where and Which When Who being reordered by goals.
Functionality internal
🎭 For designing products internal, levels in categorisations:
- Mirror: Design functionality, Devops functioning - Theoretical , Practical
About high level simplified stages
- ❗ Stable: Steer, Shape, Serve - Pull, Pull& Push, Push
About closed-loops and cycles for incremental progressing
- Mirror: What, How, Where, Who, When, Which - context, concept, logic 2x, physical, details
About stages in architecting engineering and abstraction levels.
A friction point at architecting - engineering (logic 2x).
👉🏾 Impact Interactions: hard to underestimate.
Functioning internal
🎭 When the activities are mirrored from functionality into functioning there is an reordering in:
- communication lines
- the closed-loops and cycles for incremental progresing
👉🏾 Impact Interactions: hard to underestimate.
Functionality external
🎭 For designing products external, levels in categorisations:
- ❗ Stable: Backend, Frontend - PUsh, Pull
About closed-loops and cycles for incremental progressing
- Mirror: Steer, Shape, Serve - Analyze/Prepare, Compose, Deliver/Understandng
About high level simplified stages
- Mirror: Where, How, What, Which, When, Who - context, recipe, logic 2x, result, details
About stages in architecting engineering and abstraction levels.
A friction point at architecting - engineering (logic 2x).
👉🏾 Impact Interactions: hard to underestimate.
Functioning external
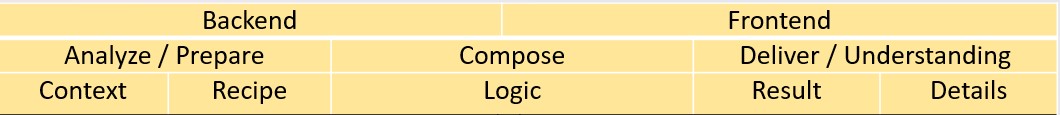
🎭 When the activities are mirrored from functionality into functioning there is an reordering in:
- communication lines
- the closed-loops and cycles for incremental progresing
👉🏾 Impact Interactions: hard to underestimate.
⚖ U-3.2.3 Walking over floorplan lines
Communication: Organisation ⇄ Technology
Strategic alignment Venkatraman ea
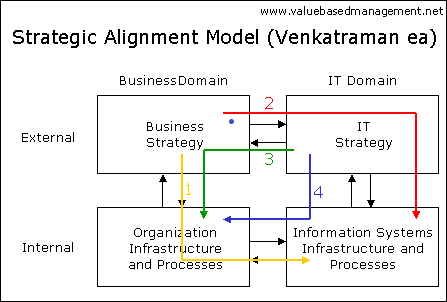 Venkatraman ea argue in 1993 that the difficulty to realize value from IT investments is:
Venkatraman ea argue in 1993 that the difficulty to realize value from IT investments is:
❶ firstly due to the lack of alignment between the business and IT strategy of the organizations that are making investments, and
❷ secondly due to the lack of a dynamic administrative process to ensure continuous alignment between the business and IT domains.
- (yellow) Strategy Execution: Business is strategy formulator, IT is implementor follower.
- (red) Technology Potential: Business strategy drives IT strategy, the organisaton follows.
- (green) Competitive Potential: emerging IT capabilities drives new business strategy.
- (blue) Service Level: The role of business strategy is indirect. "It should work."
The four options for who is in the lead and who is following are resulting in wich opportunities are possible.
The translation into the lines vertical horizontal, diagonal with six areas interactions should go is following the idea of Venkatraman ea.
Floorplan: Interactions over lines
😉 In a small environment most is covered by the same persons.
The question and challenges of managing interactions can be ignored.

🤔 In big environments there is a split by:
- many persons with different type of specialisms
- deeper knowledge in specialisms
- different levels of abstractions
- confusing high levels of abstractions
- using severla other languages in jargon
- managed by a confusing hierarchical control
Enough causes to see battles by those differences harming the organsisation.
Floorplan: Interactions lines by specialists
Walking over lines:
- Horizontal: Same abstraction level
- different type of knowledge, specialism.
following the line forward and backward receiving direct confirmation for understanding.

😉 This is the natural way of workers accepting others working in that same functional flow line.
Prerequisite culture: working in lines for a shared goal.
🤔 There is no hierarchical control.

Floorplan: Interactions lines by abstracions
Walking over lines:
- Vertical: Different abstraction level
- same type of knowledge, specialism.
following the line top-down and bottom-up receiving direct confirmation for understanding.
😉 This is the natural way of workers accepting orders in hierachy, a boss.
Prerequisite culture: a boss hierarchical knowing all what to do.
🤔 There is no collaboration over workers.
For a small organisation this will work.
What Size Company Is Right for You? (hbr 2024)
Summary: Medium-Scale Organizations (one thousand to several thousand employees)
These organizations typically offer a positive balance between the agility of startups and the structure of larger organizations.
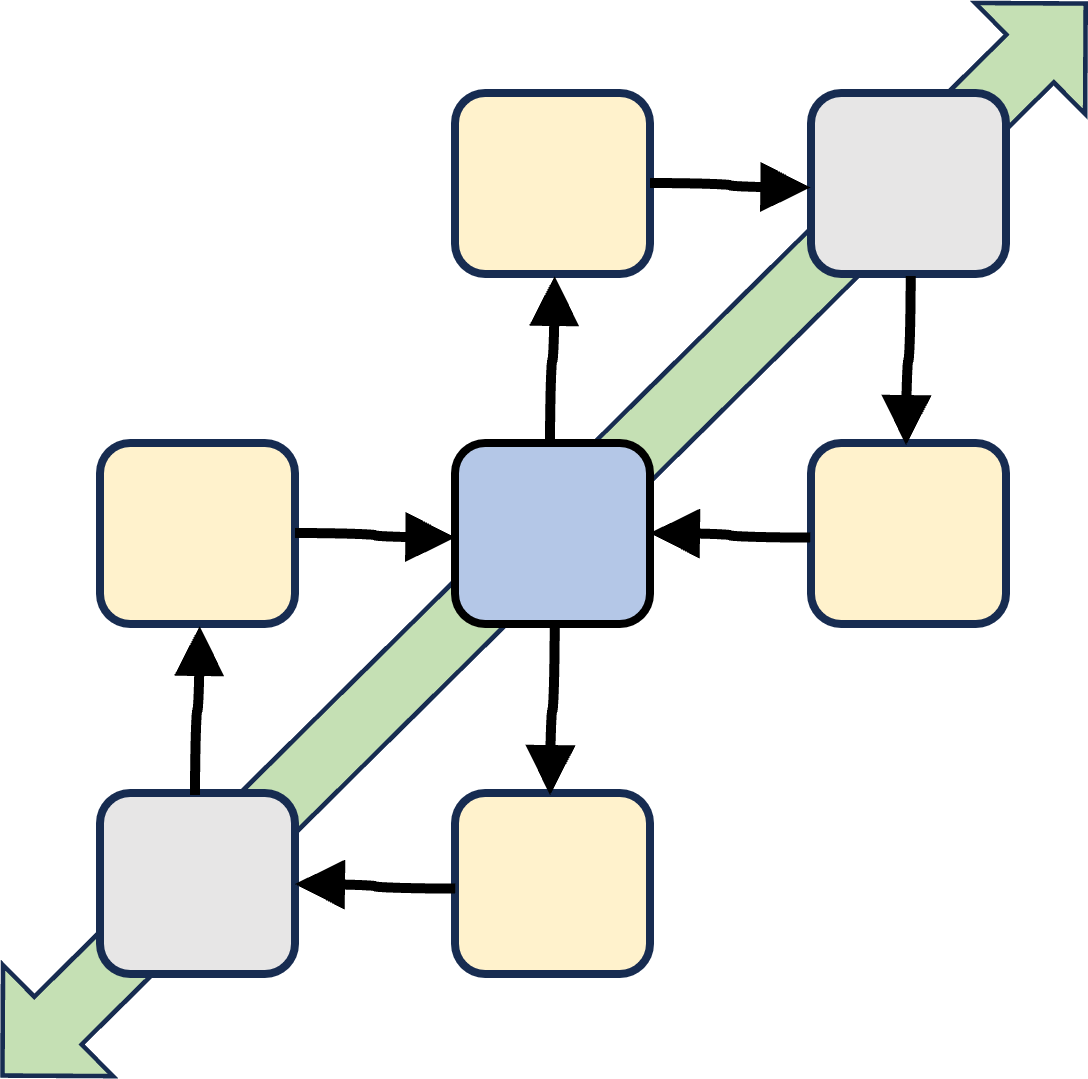
Interactions diagonals started by abstracions
Walking over lines:
- Diagonals: Different abstraction level
different type of knowledge, specialism.
- Vertical: Different abstraction level
same type of knowledge, specialism.
- Horizontal: Same abstraction level
different type of knowledge, specialism.
😉 This is a complicated way of workers and hierarchy in collaboration crossing abstraction levels and specialisms in cycles for feed-back.
Prerequisite culture: working for a shared goal.
🤔 Initiative hierarchical lines, feedback by specialisms.
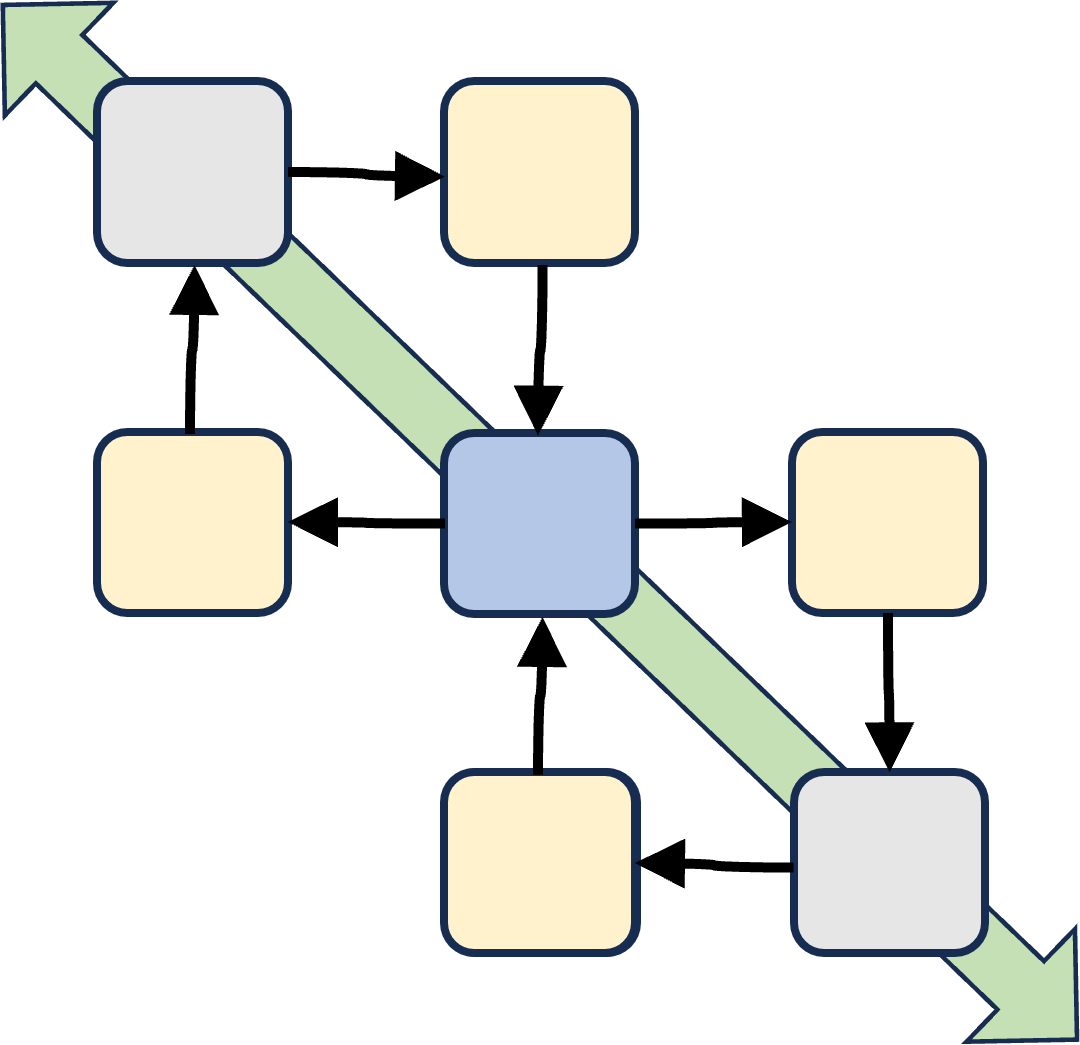
Interactions diagonals started by specialists
Walking over lines:
- Horizontal: Same abstraction level
different type of knowledge, specialism.
- Vertical: Different abstraction level
same type of knowledge, specialism.
- Diagonals: Different abstraction level
different type of knowledge, specialism.
😉 This is a complicated way of workers and hierarchy in collaboration crossing abstraction levels and specialisms in cylces for feed-back.
Prerequisite culture: working for a shared goal.
🤔 Initiative by specialisms, feedback hierarchical.
Communication interactions over all floorplans
There are in total six floorplan for all different perspectives.
- Functioning :conforming specifications
- services
- deliveries of products, information products for customer (external) value
- transformations for creating information products representing customer (external) value
- Functionality / design creating and validating specifications:
- transformations creating information products for customer (external) value
- products, information products representing customer (external) value
- services
Travelling over all floorplans is moving around in three dimensions.
This restructured version of how to commmunicatie using floorplans ives many new ideas for promotions and realisations.
💡👁❗Promotion in using several of the communication strategies.
💡👁❗Promotion how to solve communication over the diagonal flow lines.
💡👁❗Investments in time and conflict solving for adequate alignments.

U-3.3 Ideate the purpose for the Enterprise
Why a product, why events, why unexpected successes/failures is: why we are living, why we need each other.
Easier is describing what successful products are than defining how to achieve that a product will become successful.
Those skills for seeing some future is "vision".
Challenges:
- Your environment is changing fast
- You lack the data to make confident decisions
- Your operations is sprawled with internal processes
⟳ U-3.3.1 Enterprise Culture vision
Leadership
3C models
- Leaders CHALLENGE the status quo by:
- moving others out of their comfort zones
- creating a compelling vision
- establishing stretch goals
- asking challenging questions
- Leaders build CONFIDENCE by
- believing in people
- pointing out their strengths and affirming talents
- rewarding and recognizing improvement
- empowering people with authority
- Leaders are COACHES by:
- clarifying what top performance looks like
- conducting practice sessions
- providing helpful feedback
Focus Priority
3C models
The 3Cs model points out that a business strategist should focus on three key factors for success.
In the construction of a business strategy, three main elements must be taken into account:
- The Company
- The Customers
- The Competitors
Only by integrating these three can a sustained competitive advantage exist. Ohmae refers to these key factors as the three Cs or the strategic triangle.
There is also a new [when?] 3 Cs model emerging which centers on sustainability. This model is:
- Capability
- Consistency
- The Competitors
The idea behind the new 3 Cs model revolves around the concept of shared value to the company, the environment, and the community.
people, money and things
A favorite phrase of Japanese business planners is hito-kane-mono, standing for people, money and things (or assets)
Confusing titles
product manager skills
"Technical product managers" typically exist in larger product management teams.
The title comes with its own particular set of expectations and responsibilities. A technical product manager is expected to possess significant, practical knowledge about programming, system design, and the like. ...
They sometimes own responsibility for a particular part of the product but are also often deployed on an ad hoc basis to manage the technical aspects of different initiatives.
How does the AI product manager differ from the traditional product manager? (Ajit Jaolar 2024 )
A software product spans Customer value, business model and Technology.
- An AI pipeline has at least the roles: data engineer, data scientist and devops engineer.
- AI project manager is concerned overseeing: the collection, processing, and utilization of data necessary for training AI model and ensuring data privacy, compliance, regulations.
- The user experience of AI product is fast evolving especially towards chatbots and autonomous AI agents. At which point the UX as we know today, may not exist.
- The iterative development and deployment process for AI product managers involves continuous monitoring and improvement of model performance and retraining.
- Ethical considerations are crucial for AI product managers, as they address biases in AI models and ensure transparency and fairness in decision-making processes.
- Alignment to business: how does the AI metric align to the business metric. For example: how does the AI metric improve the current state of the art in the business.
- What are the limitations of AI technologies and how are these limitations being overcome
- Understanding the optimization of AI models, requiring skills in evaluating model performance, tuning hyperparameters, and addressing issues like overfitting or bias.
- The costs of building a model, including cloud provider costs and GPU costs are complex and rapidly evolving. A product manager needs an understanding of these
- The cost of training and improvement should also be balanced against business needs
- (more) ....
⟳ U-3.3.2 Culture expectation threats

The blame game
Blame Culture Is Toxic. Here's How to Stop It. (HBR Michael Timms 2022)
At work, we show kindness by doing things like paying someone a compliment with no ulterior motive or holding the door open for a colleague.
Now think about the rare occasions when we're feeling stressed and snap at a coworker or criticize their ideas.
Are we still kind?
- It turns out we may not be nearly as kind as we think we are.
A study shows that the brain responds more strongly to bad experiences than good ones and that it retains the memory of bad experiences longer.
In fact, about five positive experiences are equal to one negative experience.
- While the most destructive behavior in relationships at work may be criticism or stonewalling, the most lethal is blame.
We're naturally hardwired to blame other people when things go wrong.
But a bigger challenge is that we don't realize how often we blame.
- To eliminate blame and promote kindness on your teams, switch your mindset to a learning mindset and openly share mistakes.
That way, teammates will be more likely to acknowledge their part in making a mistake, and stop passing the buck.
Next, focus on what you can change. Use a systems approach to problem solving.
Instead of asking, "Who's at fault?" ask, "Where did the process break down?"
Agile gold Rush
The Agile Community Shat The Bed (Scott Ambler 2024 I)
is a harsh examination on the agile hype.
The agile gold rush is over and it isn’t coming back.
Executives are clearly frustrated with agile, having seen little return on investment (ROI) after sometimes spending millions on agile training and coaching.
Some snapshots of the fads:
-
Failing fast certainly has its place, but there are other, often faster and cheaper, ways to learn. Teams could have reduced their failures through better risk management (evil though it may be) and greater investment in technical skills (stuff rather than fluff).
-
Many times I ran into people who would tell me about this fantastic agile training they had taken, how they played games and learned a bunch of great ideas, only to go back to work and not know how to apply those ideas in practice.
-
The idea is that a group of people will come up with better ideas than a single person, even an expert. In many cases this is true. But when expertise is really required, it certainly isn’t.
Failing fast certainly has its place, but there are other, often faster and cheaper, ways to learn. Teams could have reduced their failures through better risk management (evil though it may be) and greater investment in technical skills (stuff rather than fluff).
Many times I ran into people who would tell me about this fantastic agile training they had taken, how they played games and learned a bunch of great ideas, only to go back to work and not know how to apply those ideas in practice.
"The road to hell is paved with good intentions."
How Agilists Can Move Forward (II)
Agile Principles
Harsh but clear examinations:
Agile Alliance Principles Examined (G Alleman 2023)
🚧 Our highest priority is to satisfy the customer through early and continuous delivery of valuable software.
➡ The concept of customer value for work performed is well-developed in any business domain.
However, definitions of value, early, and satisfaction are not provided, so domain-specific definitions must be developed before this principle can be of practical use in a specific circumstance.
🚧 Working software is the primary measure of progress.
➡ Although working software is an outcome of development, many Agile processes do not address other critical deliverables and measures of progress.
The focus on software alone misses many opportunities for process improvement before and after code generation.
🚧 The best architectures, requirements, and designs emerge from self-organizing teams.
➡ This is conjecture and not based on analytical measurements.
This principle does not state the domains in which it is applicable.
Systems engineering science has much to say here, but no recognition of this previous work is provided.
⟳ U-3.3.3 Threats by accountability nature
Threats with Changes
Prosci Explore the Levels of Change Management
Your projects and initiatives have a significant impact on the ways individual people do their work on a day-to-day basis.
Change can impact processes, systems, tools, job roles, workflows, mindsets, behaviors and more.
 All too often, organizational changes end up meeting requirements without delivering expected results.
They deliver the necessary outputs without delivering expected outcomes.
This is what happens when the organization focuses efforts on the solution itself, rather than its benefits.
All too often, organizational changes end up meeting requirements without delivering expected results.
They deliver the necessary outputs without delivering expected outcomes.
This is what happens when the organization focuses efforts on the solution itself, rather than its benefits.
Another variation in PDCA / DMAIC:
The word "ADKAR" is an acronym for the five outcomes an individual needs to achieve for a change to be successful: Awareness, Desire, Knowledge, Ability and Reinforcement.

Change: Threats, risks
Serious change management problems:
- doing any not verified change in the assembly line,
Internal product life cycle, new features can break continuity
- Certificates, licenses. Needed in time, continuity fails when not changed.
- Required security fixes. Ad hoc by external events, not known urgency.
Continuity can break when not done or when done
- Abandoning an old product when the new one is not ready.
⚠ The usual change management process in place (ITIL) doesn't have a vision for change categories evaluating associated risks.
Acountablity responsiblity, risks
My first surprise was that there the product management accountability isn't visible.
Using the floorplans many positions with a key product activity were found with natural conflicting interests.
A CPO, chief product officer, is the most logical position for coordination.

Accountabilities, roles:
- ⚖ Product manager: coordinating operations, changes, innovations.
focus: functionality - functioning
- ⚖ Business analyst: manages informed product advisories by analyses.
focus: functionality - appropiate
- ⚖ Account manager: coordinating flow, financial operations.
focus: quantity availablity - profitability
- ⚙ Sales manager: coordinating to external customers, martketing.
focus: profitability - appropiate
- ⚙ Water Strider: coordinating flow, product operations.
focus: functioning - quantity availablity
- ⚠ Quality Control: Safe products by quality by specficiations.
focus: functioning - acceptable quality
- ⚠ Safety analyst: Safe environment for internal and external stakeholders.
focus: Safety - functionality
- ⚠ #TBD remediates: Safe environment internal and external stakeholders.
focus: Safety - functioning
The conflicting type of interests needs to be solved by additional C-parties.
In a figure:

"The road to hell is paved with good intentions."
Using logical floorplans gives many solutions and very sadly new challenges to solve.
💡👁❓Human nature is poisoned by the risky blame game, how to avoid that?
💡👁❓Changing anything is not without risks, how to manage risks?
💡👁❓Managing the product holistic with all conflicting interests, a real challenge.

A-3.4 Evolving technical operational organisations
Optimising lean "processes: cyber/adminstrative" is the goal Jabes is helping to focus on.
Value stream processes are core business lines. These are dependent on the quality & quantity of a technology connection.
Where to pay attention on:
- T - Technology product service alignment
- I - Technology service technology optimization
- P - Technology service Functional processes
⚖ U-3.4.1 From Chaos to Control
The Throughput Improvement Process (TIP)
Strategy For New Design? (K.Kohls 2024)
Improving plant throughput to the design process: implementing the Throughput Improvement Process (TIP) based on the Theory of Constraints (TOC).
The core principle is straightforward: the throughput of the system is limited by its bottleneck.
The performance of this bottleneck dictates the performance of the entire plant.
➡ ❗
The goal: integrate system optimization into the design process.
Rather than striving for perfection, we aimed to create a capable system—one that doesn’t introduce new bottlenecks.
This approach requires a shift in mindset: no need perfectly accurate data; just avoid making decisions that would cripple the system.
This approach transformed the design process. Decisions that once seemed logical in isolation but harmful to the system were now easily overruled.
Collaboration improved as groups worked together to achieve the common goal: ensuring the plant could run at its designed rate.
Master Data management
❗ The role of the Chief Data officer. Should not be about technology but about understandng information.
Master data management (MDM)
Master data management (MDM) is a process that creates a uniform set of data on customers, products, suppliers and other business entities across different IT systems.
One of the core disciplines in the overall data management process, MDM helps improve the quality of an organization's data by ensuring that identifiers and other key data elements about those entities are accurate and consistent, enterprise-wide.
Naming Conventions
Using naming conventions can be very helpful for master data management. An successful classification mechanism is:
The Dewey Decimal Classification (DDC)
, colloquially known as the Dewey Decimal System, is a proprietary library classification system which allows new books to be added to a library in their appropriate location based on subject.
An example that could be copied, extended in information technology.
This is not easy to achieve. Note: nothing of this is usually in place, causing al lot of miscommunication, misinterpretations, wrong expectations.
⚖ U-3.4.2 Service quality versions adding value

The enterpise organisation, executive
When the product service is what is about, the CPO (Chief Product Officer) has a pivotal role.
A CPO is more then than the COO (Chief Operations Officer) it is including innovation (Chief Innovation Officer), technology alignment, involving empowered people.
A proposal for a new abstract strcuture:
- CFO Chief Finance officer, CDO Chief Data officer, CEO Chief executive officer
- CAIO Chief Analytics & intelligence officer, CPO , CTO Chief technology officer
- FM/HR Facilities and Humanity, CSO Chief Safety officer, CRO Chief risk officer
All of them are exchangable to other enterprise
Top-down theoretical view:
Figure, see right side
The enterpise organisation, shop floor
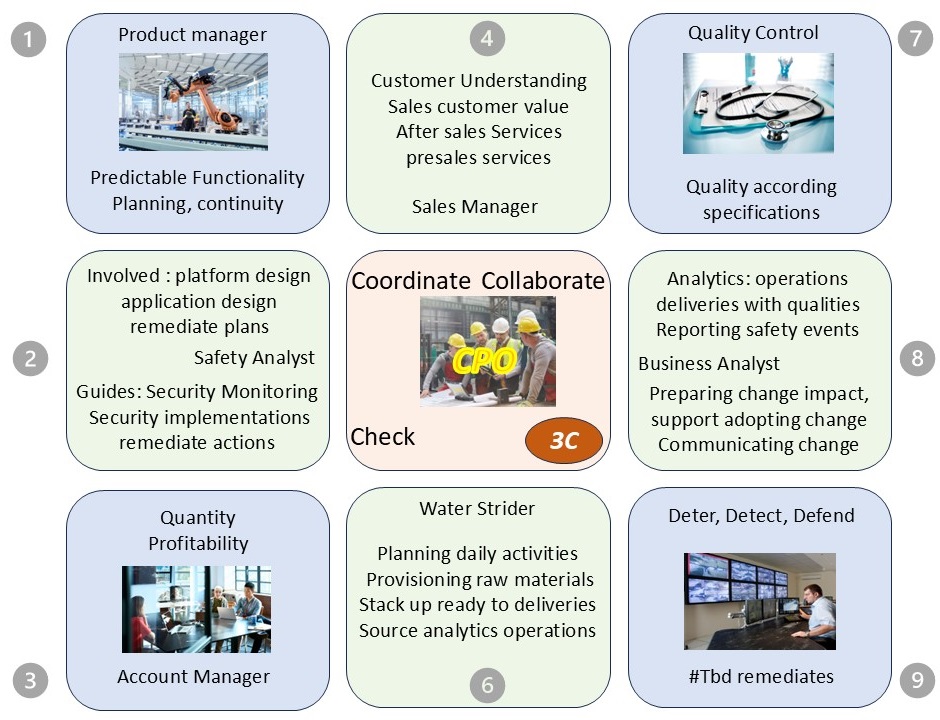
Bottom-up practical view:
Figure, see right side
Supporting Explainable transformations
Enabling any kind of activity is realised by financial budgetting.
Investment-based Budgeting (NDMA 2024)
forecasting the costs of planned projects and services, not just what you plan to spend.
Planning forecasting, evaluating, doing accounting is analytics.
In traditional processes, each department submits a budget to get money to pay its costs.
The budget is a forecast of spending on expenses such as compensation, travel, training, and vendor services.
➡ Why is this bad?
- This kind of budget just begs for micro-management. ...
Top executives really don't know what you need to run your business.
But what have you given them to talk about?
- Perhaps the worst effect is that traditional budgets don't support sensible decision making.
Scarce resources (money) should be allocated to the best investment opportunities.
😱 But there's no way to analyze ROI.
- Once approved, traditional budgets provide no basis for demand management.
Clients may say, "You got all that money, so why can't you do everything I want for free!?".
🤔 You have no way to explain what is, and what's not, funded by your budget.
- Also, traditional budgets don't support cost accounting.
There's no way to know what portion of your budget should be allocated to each of the various business units.
➡ ❗ Change from budgetting in hindsight to forecasting with insight.
In internal market economics, business and budget planning take a different form.
As a business within a business, you don't get money to pay your costs. You're given money to "buy" your products and services.
- Investment-based budgeting looks at scenarios telling you what different levels of funding will "buy" from each support organization in the year ahead, so as to decide funding based on business needs and investment opportunities.
Not: last year +/- a percentage.
- Investment-based budgeting review costs over the organization's entire product line, including internal services of support functions, not just a few external numbers.
- Internal customers will defend your budget by explaining their needs and the business value of your products/services.
This is appropriate, since customers are the ones who suffer when your budget is cut and they're the ones who benefit from giving you a larger budget.
- There's no place for the "do more with less" edict, which forces managers to commit to more than they have resources to deliver.
This ultimately leads to failures in delivery, not efficiencies.
- You have a realistic basis for profitability analysis.
Knowing: total costs, direct and indirect, and have pro forma profit/loss statements by business unit, product line, or customer.
- Executives can better know the full cost of strategic initiatives, not just in the lead business unit (the tip of the iceberg) but across all the relevant support functions.
⚖ U-3.4.3 Data governance, analytics - business intelligence
Chief data officer (CDO)
The role of a CDO is far more than:
- master data management
- naming conventions
Aside those not easy topic getting the enterprise aligned is the goal:
- defining & using communication channels
- being the guide in using shared vocabularies
- Help in explanations when words are misinterpreted
- helping others in using communications
Information chains by time
In the ancient times of ICT storage was very expensive.
Less used information was eliminated although those could be very important.
A technical and logical holistic review on how to manage previous states of important information has never materialised.
That is technical and logical data debt that should get solved. Technical is about technology (CTO), logical about data governance (CDO).
Chief Analytics &mp Intelligence (CAIO)
The role of a CAIO is not an existing one, it is not about the technoloy.
Support, help for:
- Product understanding
- Process understanding
- what do in compliancy for regulations
- being the guide in using shared vocabularies
It is more advanced role what a statistcian would do for understanding usage of statistics.
Logs, journals - data collectors
The CDO is the coordinator for collecting understanding relevant data transforming into meaningful information on the floor.
The safety on the floor supports the operational connections. The business analyst is providing accountable managers what they need for forecasting, planning.
Both the safety analyst business analyst can use the same resources there is only a different perspective in the goal.
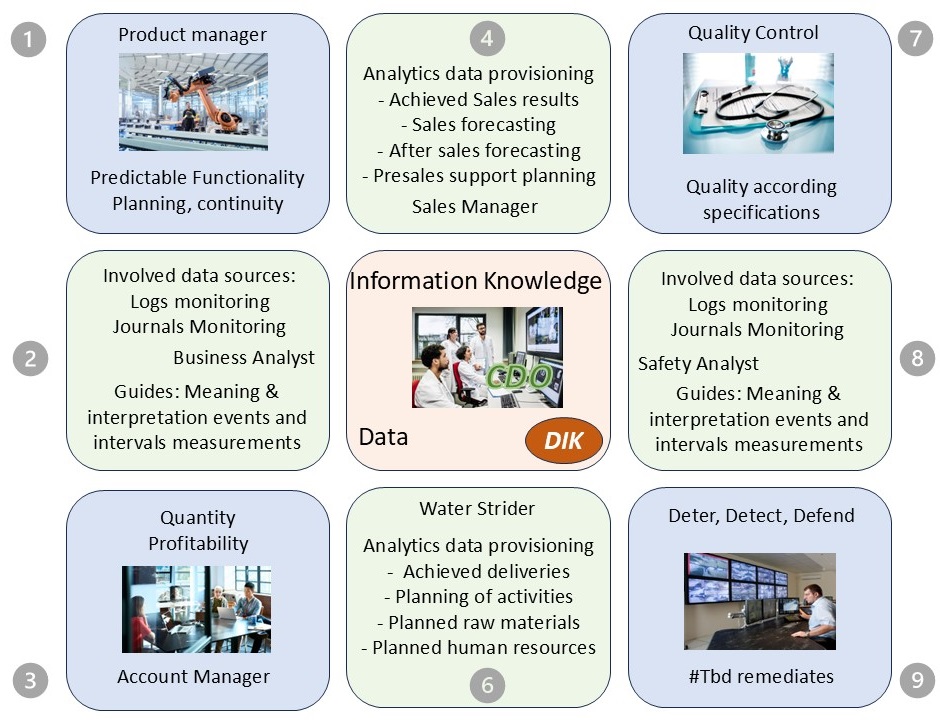
Bottom-up practical view:
Figure, see right side
➡ Logs are the accepted way for extracting an collecting information.
Logs are usual created for technical reasons not intended for a specific goal.
-
Advantage:
- Generic presence of logs, ease of modification limited effort budget isa tempting start for getting to know what is going on.
Disadvantages:
- logs are probably not the real match for answers on questions what is going on.
- low data quality
➡ ❗ Journals are more specific designed events for data-collectors. They have a more defined specfic goal.
Logs and journals would look similar, a more clear difference is logs are registering technical events e.g. the time snap with of specfic an event,
journals are registering logical information events e.g. the time snap the change of specfic information type.
Advantage:
-
journals have a more meaningfull understandable logical information type with their time snaps.
- high data quality
Disadvantage:
- journals are not generic. Efforts is required, investments budget, for getting good ones.
Analytics, intelligence operational risk
For "closed loop" analytics, transforming information into knowledge to achieve insight for decisions.
The only difference between the CPO and the CAIO is: The CAIO is looking at how the analytics is done, for what goal.
Decision makers giving underpinning in the why at decisions.
Top-down theoretical view:
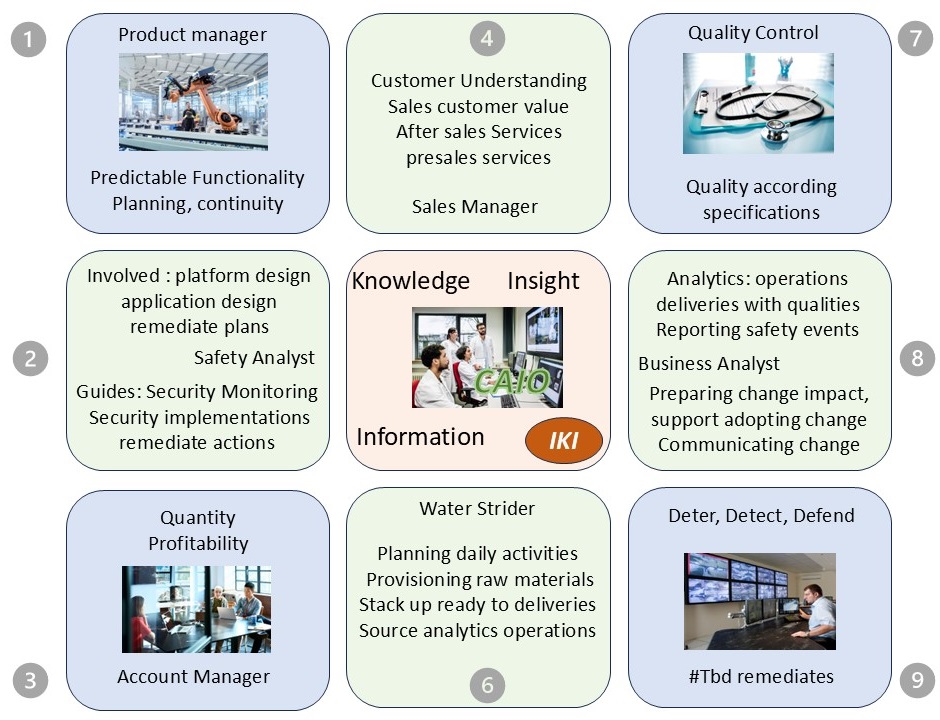
Figure see right side
This view on using data information, lean, product lines, is very unusual but logical.
💡👁❗ Measurements for understandable attributes in functionality and functioning.
💡👁❗ Have a shared glossary vocabulary in understanding language for insights.
💡👁❗ Planning for the future while knowing the history.

U-3.5 Realizing optimised lean services
Optimising lean "processes: cyber/adminstrative" is the goal Jabes is helping to focus on.
Value stream processes are core business lines. These are dependent on the quality & quantity of a technology connection.
Where to pay attention on:
- T - Alignment product service alignment
- I - Alignment service technology optimization
- P - Alignment service Functional processes
⚒ U-3.5.1 OPS Serve functioning
The process quantum on the shop floor
The key factor is a functioning product delivery to customers (external).
In an oversimplified approach there is only a single process, a single factory, that is doing the work for the delivery to the external stake holder.
The factory has several flows and several closed-loops.
The functioning flows:
- product deliveries (green, push ltr)
- product adjustments, changes (yellow)
One additional input:
- product change, factory change (blue)
Three closed loops and a disturbing one:
- Capabilities functioning factory (green)
- Product functionality quality (blue)
- Service purpose performance (red)
- External events influencing intentions (black)
In a figure, see right side.
Interactions between process quantums on the shop floor
A product is never created from scratch without materials being supplied, with tools being supplied.
There are several complicated supply chains:
- The chain of materials
- The chain of tools in use serviced by suppliers
Tools are products that should comply to service agreements for products by other parties.
This is something of the same kind as the product created serviced internally to external stakeholders.
The chain of supply in materials is a complicated one by dependencies other external products, reuse of partial information products.
Just an attempt to visualize by a fictive example:
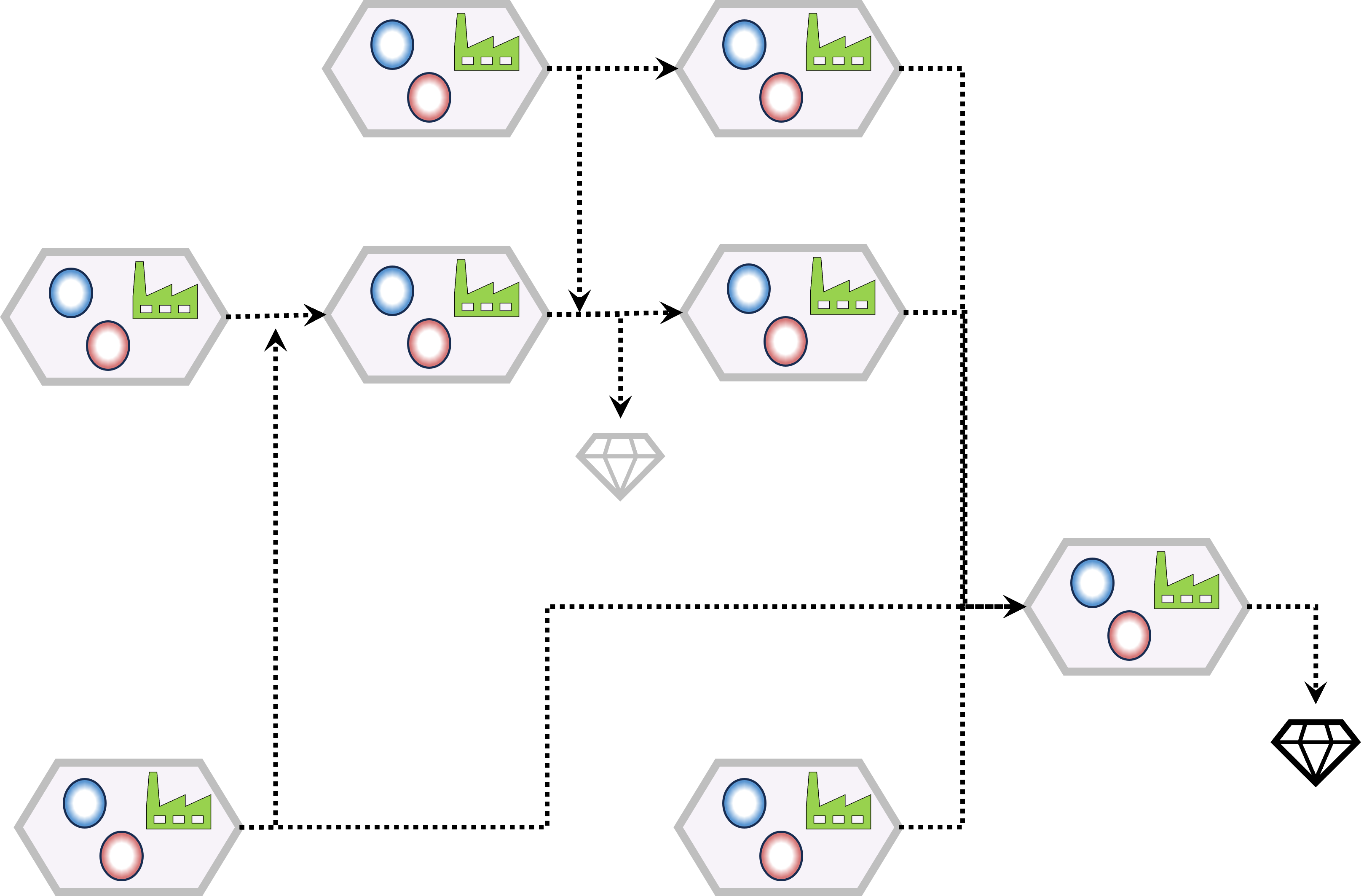
see right side.
This is the most lively environment:
😉 Optimizing the factory should be a normal a normal activity within the factory.
😉 Replacing tools by more appropriate ones should be a normal within the factory.
😉 As long as the responsibility for functionality and the accountability for service are in place and there is a demand for the product functionality the factory has a underpinning for existence.
⚒ U-3.5.2 CTM Shape functionality
The process quantum for the shop floor
The key factor is a product functionality usable for deliveries customers (external).
In an oversimplified approach there is only a single process, a single line of design, that is defining, creating the functionality and enabling deliveries for external stake holders.
Designing the functionality has several flows and several closed-loops.
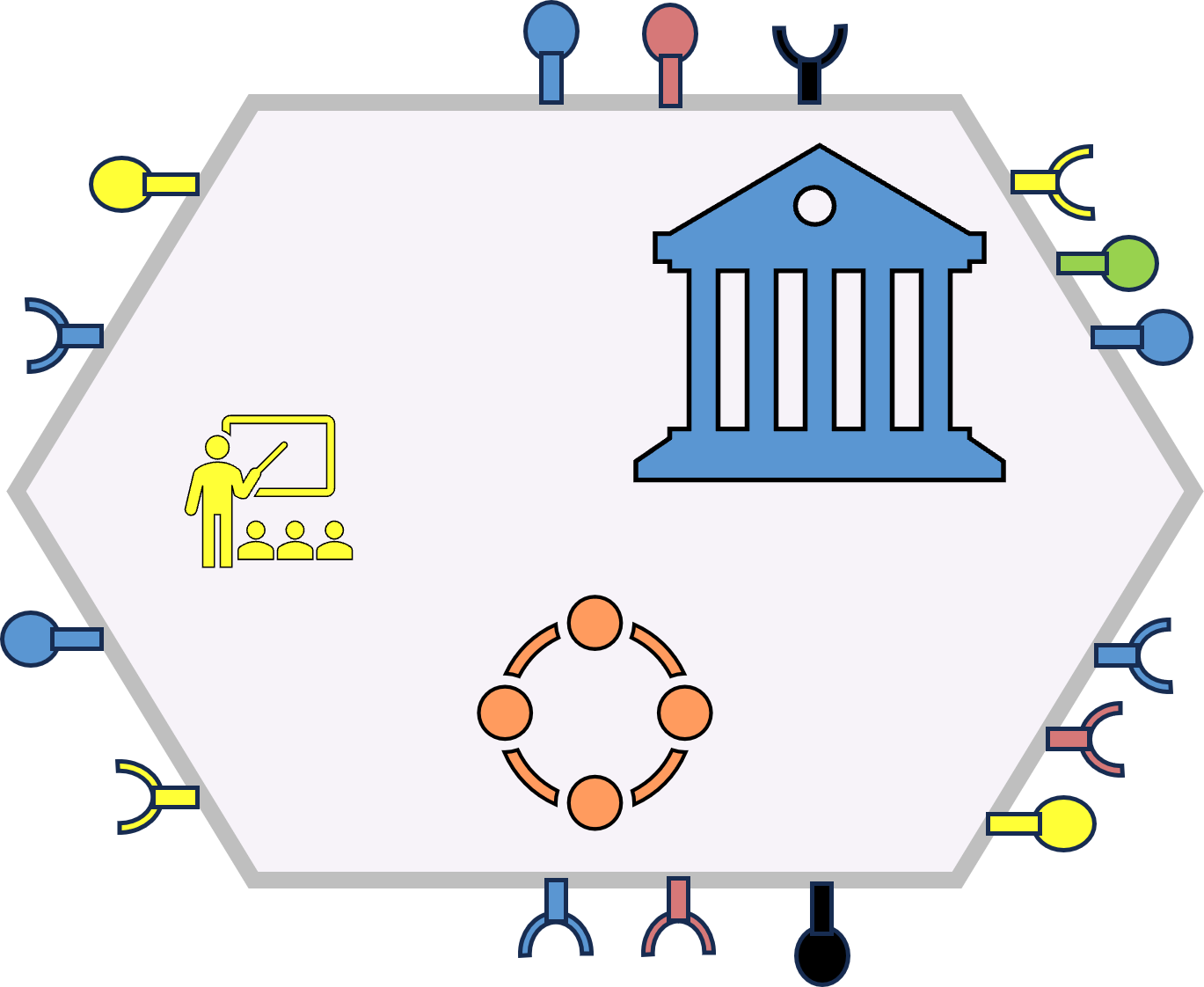
The functionality flows:
- product base qualities (blue, push ltr)
- product adjustments, changes (yellow)
two additional input/output lines:
- In: Purpose adjustments, base qualities change (red)
- Out: Deliveries change, factory change (green)
Two closed loops and a disturbing one:
- Product functionality quality (blue)
- Purpose translated into functionalities (red)
- External events influencing intentions (black)
In a figure, see right side.
The process quantum for the shop floor
It would be simple when there was just a single responsible body for functionality and capabilities at functioning.
In reality there are several bodies with different type of expertise.
In a figure, see right side.
This environment is not that lively :
😉 Creating and optimizing the functionality for one or more factories is very well possible by a single responsible body.
😉 Having accountability and responsibility for functionality and being responsible for the service capabilities is a challenge for closed loop evaluations.
⚠ A closed-loop direct from functioning of the service to the accountable person for the service is a requirement for quality for the service and quantity with the service.
⚒ U-3.5.3 SMA Steer purpose
The key factor is a product functionality usable for deliveries customers (external).
In an oversimplified approach there is only a single process, a single line of design, that is defining, creating the functionality and enabling deliveries for external stake holders.
Designing the functionality has several flows and several closed-loops.
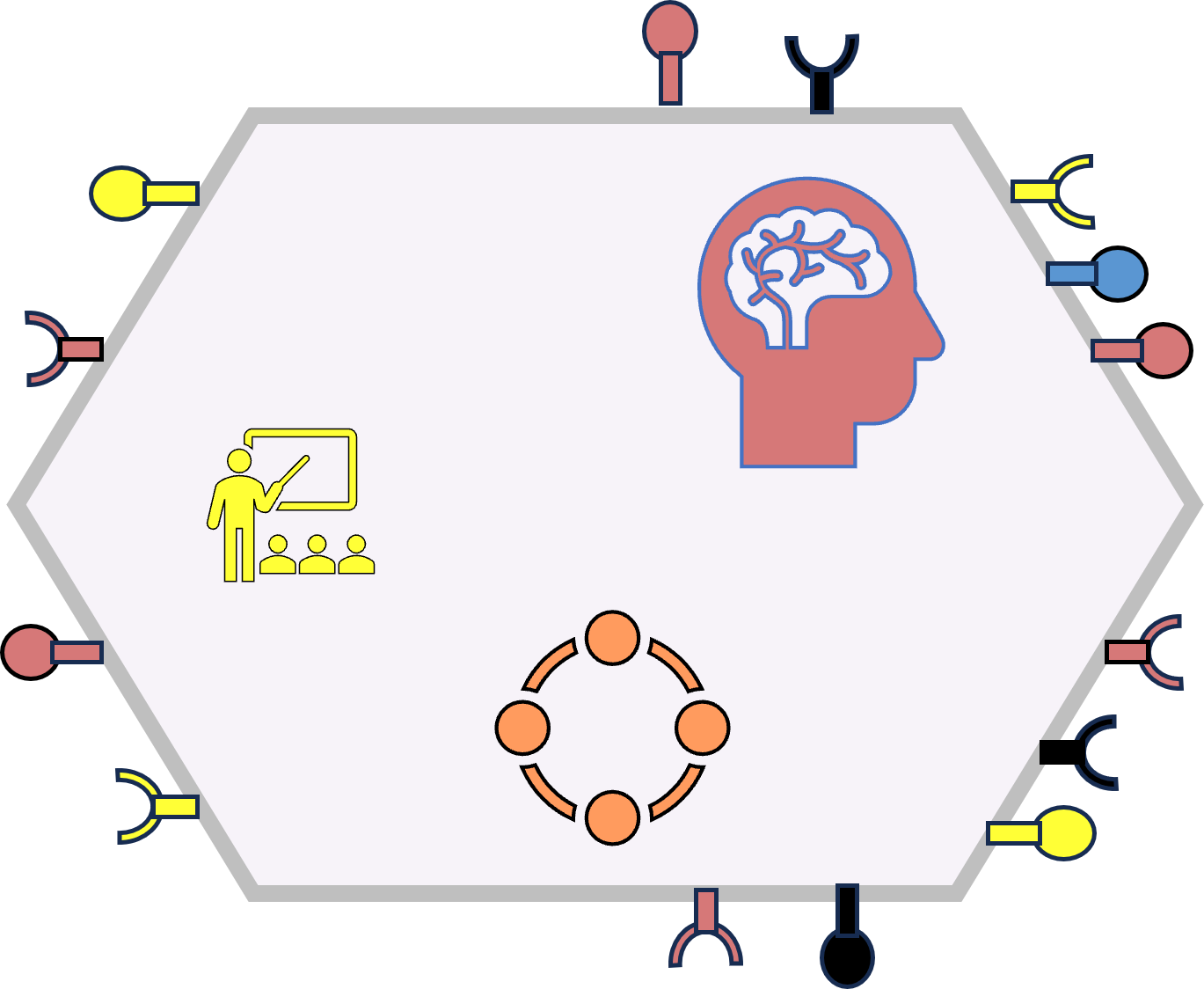
The purpose flows are for:
- Service intentions (red, push ltr)
- intentions adjustments, changes (yellow)
two additional input/output lines:
- In: purpose change externally driven (black)
- Out: Purpose adjustments, qualities change (blue)
One closed loops and a disturbing one:
- Purpose translated into functionalities (red)
- External events influencing intentions (black)
In a figure, see right side.
The process quantum for the shop floor
It would be simple when there was just a single accountable person for the purpose of service.
In reality there are several areas with other accountable persons in the material flow.
This impacts the options in functionality.
In a figure, see right side.
This environment is the hitting the public arena:
😉 Issues in the service possible escalate into events hurting the flow or helping the flow.
⚠ Collaboration between accountable persons involved in the service is required.
When collaboration fails a negative spiral is a possible outcome.
⚠ Managing both functionality and functioning is needed avoiding, resolving conflicts.
A negative spiral for the service is possible when misunderstandings, conflicts escalate.
⚒ U-3.5.4 Maturity Steer Shape Serve
Maturity evalution market options
The Global Business Services maturity model (kpmg 2016)
KPMG was mentioned to be an origin .Still ambigue with not clear visions, not clear understandabel actions.
Operational cost reductions remain a high priority for Global Business Services (GBS) organizations, but increasingly they are viewed as a given.
Much greater emphasis is placed on delivering measurable business value and innovation beyond cost savings.
Seeing an offering an evaluation for maturity, the figure is the interesting part.
Digital Maturity Assessment (kpmg 2023)
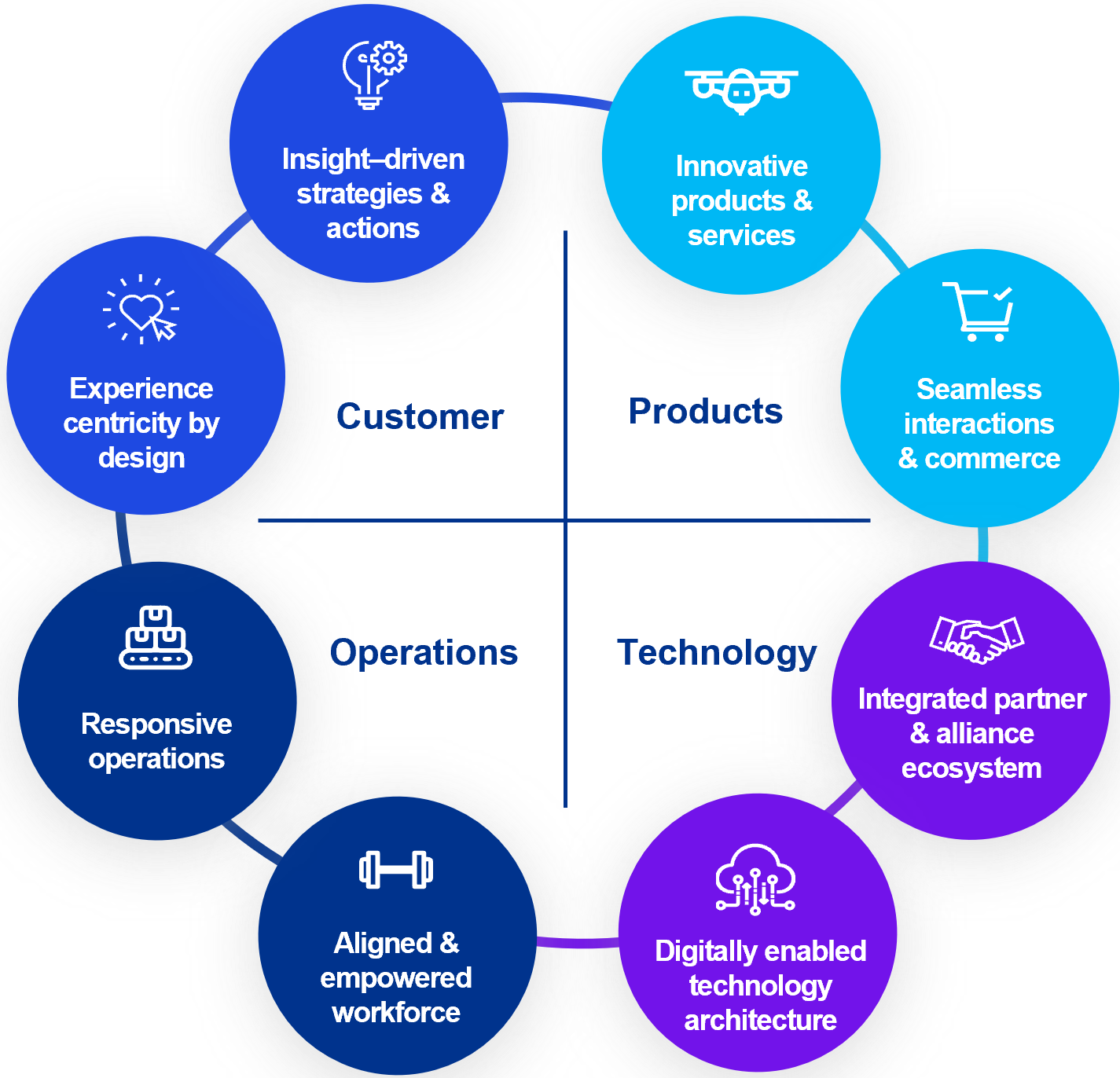
See the figure right side:
Aligned to the SIAR model.
At the top left to right, Pull (request):
- IV Customer Ideate Asses:
experience centricity by design,
insight-driven strategies & actions
- III Products Plan Enable:
innovative products & services,
seamless interactions & commerce
At the bottom right to left, Push (result):
- I Technology Demand Backend:
integrated partner & alliance ecosystem,
digitally enabled technology architecture
- II Operations Frontend Delivery:
aligned & empowered workforce,
responsive operations
New words, new attentions points to consider.
USM Value Maturity Model
The term maturity is frequently confused with the term 'capability' (skill, competence).
Capability refers to the degree of perfection with which a party delivers a certain performance, according to the definition of that performance.
However, that says nothing about the value of that performance for the customer.
Services have only one goal: to create value.
For that reason, USM considers maturity from the perspective of value creation.
USM Value Maturity Model
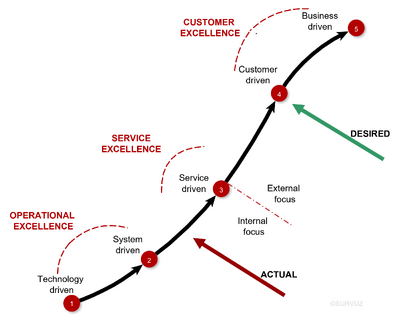
See figure at the right side:
There is an assumption of the actual and desired situation.
- Technology driven. In the service provider's first growth phase, the customer is not leading but following.
- System driven. In the second growth phase, the technology is under control. The service provider is able to make coherent systems available.
- Service driven. In the third growth phase, the service provider's attention is focused on providing services. The service provider also pays special attention to its own position and policies.
- Customer driven. In the fourth growth phase, attention shifts to the customer. The customer and the service provider cooperate in specifying the service and how this creates value for both the customer and the service provider.
- Business driven. In the fifth growth phase, the customer and the service provider deliver added value to the customer's business activities through a partnership. The service provider invests at its own risk in the development of services that create (even) more value for the customer.
The actual assumption could be too optimistic because it states technology is under control and coherent systems are available.
SEI Maturity
Market Guide for Software Engineering Intelligence Platforms (2024 Frank O'Connor, Akis Sklavounakis, Manjunath Bhat, Peter Hyde)
Gartner defines software engineering intelligence (SEI) platforms as solutions that provide software engineering leaders data-driven visibility into the engineering team’s use of time and resources, operational effectiveness, and progress on deliverables. This data-driven visibility enables software engineering leaders and their teams to make smarter business decisions, which leads to the delivery of increased value to customers.
SEI platforms must be able to ingest and analyze the signals created by common engineering tools and systems.
They must provide rich, tailored, role-specific user experiences to enable leaders to more easily query data to identify important trends and gain contextual insights.
- The software engineering intelligence platform market is small but growing.
- Software engineering leaders are under increasing pressure to use data to demonstrate that their teams are delivering value.
This data is often either unavailable or distributed across many different engineering systems making it difficult to collect and analyze.
- Software engineering leaders are wary of adding other engineering systems into an already crowded and fragmented landscape.
They are concerned that such a solution may be perceived by their teams as an effort to micromanage, and about how this might impede or erode trust.
The JABES proposal is overarching SEI, it is a connectiong to business core values.
To be short, a maturity level indication for SEI is: level 0.
This new level build on restructured version of USM principles solving the gap for lean realisations.
💡👁❗Promotion how to see the shop floor in cyber administrative.
💡👁❗Promotion for closed loops, continuous improvements, disruptive changes.
💡👁❗From the shop floor have a clear vision on accountabilities responsibilities for quality and quantity in services.

U-3.6 Maturity 5: Controlled Enterprise Changes
Once Dorothy and her colleagues made the journey to OZ, they quickly found out that there was no there, there.
The Wizard simply told her what she really should have known all along.
Dorothy and her companions just had to figure out how to reframe their own perceived shortcomings and recast them as strengths to achieve real transformation.
⚙ U-3.6.1 Safety: Capabilities for managing uncertainties & risks
Data processing I: Regulations
Purpose: Comply with legal requirements from a minimum level up to beyond the underlying essence of those requirements.
- A lot of information sources from several internal domains have to be combined.
- During the building of a report the content is high confidential.
- When published for the public the report becomes public.
- Financial value is not equal to the real value.
👉🏾 Needed: culture mindset for understanding the regulations en what to do for those.
⚒ U-3.6.2 Interacting communicating becoming an entity
Data processing: support in a shared language
Purpose: Enabling more advanced tasks than a single person or small group is capable to do.
👉🏾 Needed:culture mindset for willing to collaborate, cooperate.

⚖ U-3.6.3 The organisation servicing a product
Voice of the customer, stakeholder
It solves a problem, gives a benefit, satisfies a desire:
- Applicable, Appropiate, Acceptable (quality),
- Available (quantity)
- Affordable
😉 No situation is the same forever although questions could be the same, the logical solutions is kept the same, the technology changing fast.
Data processing II: Product Service
Purpose: Use information, data that describes thea product / service. The closed loops are required to understand and adjust the changes in the market / technology / goal-use.
- Information mainly to be retrieved from Internal sources combining mulitple domains.
External information retreived for insight in performance and the competitors position.
- Information is intended for involved persons for the product / service only (restricted).
- Used for decisions about the product / service by product management. CPO accountability.
- There is a strong financial component, financial value is not equal to the real value.
👉🏾 Needed: culture mindset for understanding what to offer, what options for offerings are.

⚖ U-3.6.4 The goal & maturity of the internal organisation
Data Gathering
Information start with gathering data. Data is:
- configure logs
- Create logs
- Use logs
👉🏾 Needed: culture mindset for simple effective data collectors.
Information Understanding
Information understanding for insight requires an understanding by used words. Information is:
- Using words describing the context of information.
- Using words and values describing the content.
- Using words for relationships between types of information
👉🏾 Needed: culture mindset using a shared master data management vocabulary.
Sei - JABES
Where Jabes is a framework and tool intended to structure software engineering by basic questions the SEI market is trying to connect the disperse complex situation.
The four quadrants are remarkable positioned in a good fit in the Jabes and other philosophy context.
Market Guide for Software Engineering Intelligence Platforms (2024 Frank O'Connor, Akis Sklavounakis, Manjunath Bhat, Peter Hyde)
Gartner SEI figure:
⚙ U-3.6.5 The goal & maturity of the organisation as service provider
Data processing III: Product Lines
Purpose: Use information, data that describes thea product lines. The closed loops are required to understand and adjust the changes in the internal lines.
- Information to be retrieved from Internal sources, simple data collectors.
- Information is intended for involved persons for the product line only (restricted).
- Used for decisions about the product line by product management and plant management. CPO accountability.
- The financial component is ancillary, financial value is not equal to the real value.
The USM maturity is in line for Product Lines and Product Service.
Why: PDCA - DMAIC - SIAR , lean
This is the third image: dynamic, static & stages for flow & control.
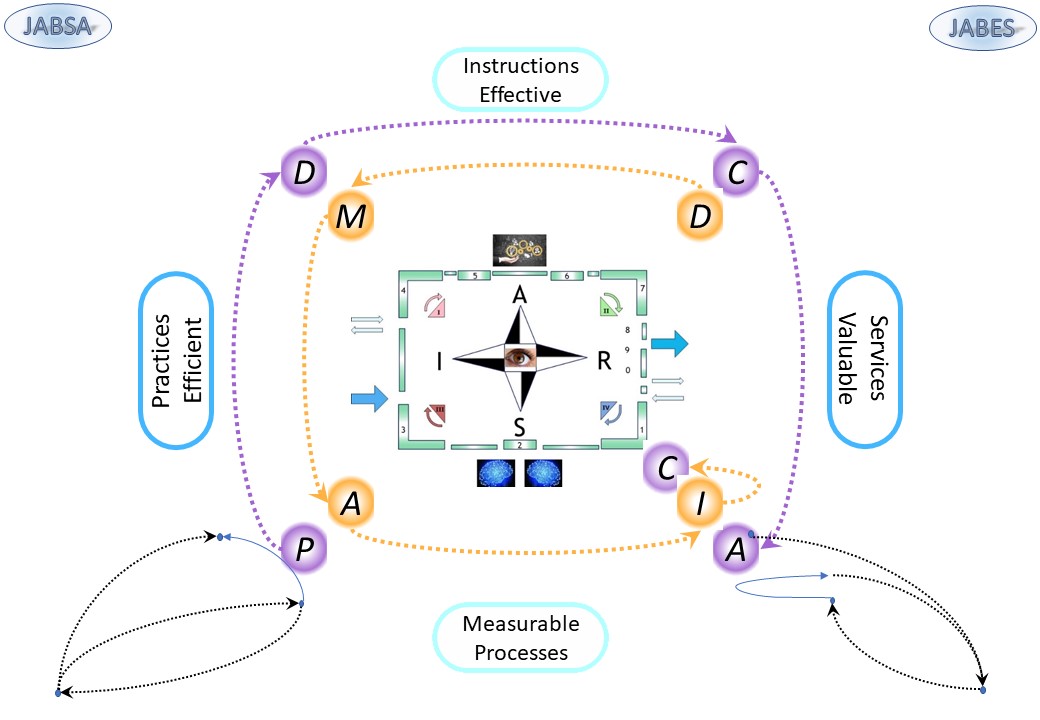
Change:
PDCA
DMAIC
- define, measure,
- analyze, improve
- control
SIAR
- situation,
- input
- activity/analyse
- result/request
Information, data, processing adding measurements for understanding value creation:
- functionality: Processes, Practices, Instructions, Services
- functioning: Measurable, Efficient, Effective, Valuable
- Applied closed loops by: Data, Information, Knowledge, Insight
😉 Improving requires acceptance to unlearn and learn consciously.
Setting values for goals at all levels matching in the way of working.
With understanding what needs to be done for improvements the choices in priority are getting help by better understanding of impact by changes.
👉🏾 Needed: culture mindset understanding what to improve, what options to improve are.
What: Lean Jabes maturity vs service maturity
👉🏾 The Jabes maturity measurment is based on CMMI levels 0,1-5 and lean principles.
Service maturity is based on CMMI levels 1-5.
How: Lean principles
There is no standard definition of what lean is or how to recognize it.
It is a combination of several strong related aspects.
Two important aspects were missing from the listed seven, adding:
- See what is going on on the shop-floor
- Give feed back in closed loops with evaluations to support optimizations
👉🏾 Using these nine aspects in 3*3 planes.
The aspects for lean are well known ones.
There is a difference between theory and realisation, the same aspects have different perceptions from another position, other perspective.
Difficulties in perception using a top down or bottom perspective helps in understanding decreasing those difficulties.
Selecting nine, ordering those in two 3*3 planes, is a new idea.
In the end there will be a multidimensional cubicle model view with three axis.
Top-down theoretical view:
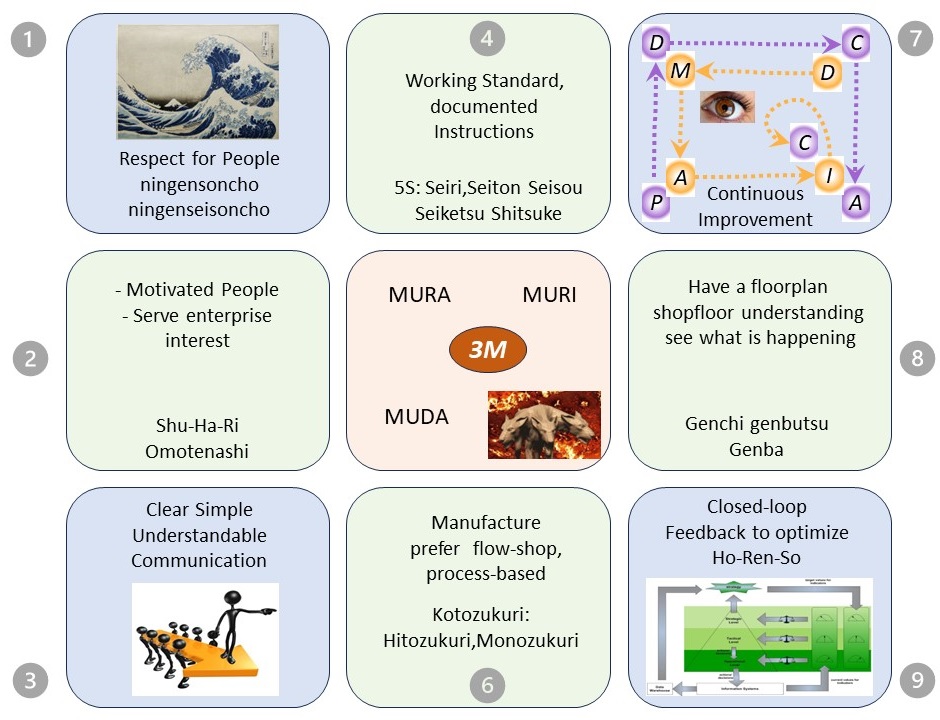
The figure,
see right side
Bottom-up practical view:
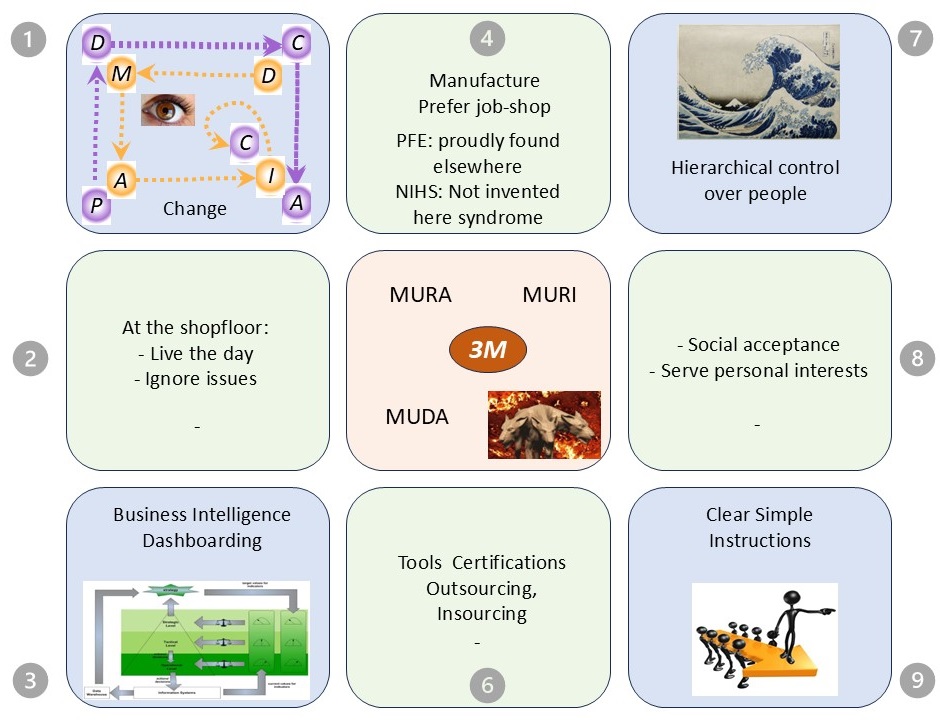
The figure,
see right side
Another one is "data", analytics, business intelligence.
There are 3 closed loops for a service, the processing line for a product:
- functioning of the service (operations)
- functionality of the service (design, technical and functional)
- achieving the purpose of the service, for the good bad and ugly

The model a 3D puzzle build up in pieces
Edge pieces will hold a combination of all of the three axis domains.
Defining all pieces representing dedicated content is the first puzzle.
Every area on the planes is unique only by having a logical position in the correct orientation the result is meaningful.
Three axis:
- How to organize the work to do: Lean
- what to use for doing the work: Tools
- Why the purpose, goal of work, the service implemented: Product
A 3D hs six surfaces, The collections made is by eight surfaces, where four of them not having an interenal PDCA cycle. A 3D view of the 4D object is less clear.
The model: a 3D puzzle changing planes
For Jabes there is a maturity evalution for 36 attention areas instead of 9.
With six floorplans it is a 6*6*6 dimensional world.
What is mentioned for service maturity is covered.
There are pinciples defined in USM that are covered by Jabes.
- The service mindset
- optimize for achieving higher maturity levels
- Evaluating maturity levels for a portfolio is by closed loop in Jabes
This would be easy when there were no correlations between the areas and floorplans.
Any change Will impact and change something at other ones, it is a mulitdimensional approach.
Just the cycles to improve are, is limited to 3*3*3 dimensions.
Possible variations are high in number.
The Rubik's Cube is a 3D combination puzzle.
When the mapping of the change management theory is possible to map to that, there is knowledge how to solve those kind of multi-D puzzles.
⚙ U-3.6.6 Following steps

These are practical sdlc experiences.
Data Information generic - previous
sdlc , development life cycle 👓 next .
Others are: concepts requirements: 👓
BPM SDLC
Bianl
© 2012,2020,2024 J.A.Karman


 The world of BI and Analytics is challenging.
It is not the long-used methodology of producing reports.
The world of BI and Analytics is challenging.
It is not the long-used methodology of producing reports. 












 Notes:
Notes:
 The ICT service, technology, supporting multiple services in shared infrastructural resource usage is multi tenancy.
When there is no shared infrastructe the information safety and processes like access management have no managed entity.
The ICT service, technology, supporting multiple services in shared infrastructural resource usage is multi tenancy.
When there is no shared infrastructe the information safety and processes like access management have no managed entity. 








 🎭 The difference between designing functionality and designing for functioning is hard to underestimate.
Who is communicating with who, interacting for what to service the service is different by goal and initiative.
🎭 The difference between designing functionality and designing for functioning is hard to underestimate.
Who is communicating with who, interacting for what to service the service is different by goal and initiative.  🎭 The difference between managing the internal organisation and one supporting external contacts hard to underestimate.
In the centre of lines for functionality and functioning with activities there are complete different sets to manage.
🎭 The difference between managing the internal organisation and one supporting external contacts hard to underestimate.
In the centre of lines for functionality and functioning with activities there are complete different sets to manage.  An attempt for lean in properties, attributes and purpose:
An attempt for lean in properties, attributes and purpose:


 There are only a few number principles left in each Logical group. In this way they are more easy this way to be translated in visions, missions, goals.
There are only a few number principles left in each Logical group. In this way they are more easy this way to be translated in visions, missions, goals. 
 ... An access token is a protected object that contains information about the identity and user rights that are associated with a user account.
➡ When a user signs in interactively or tries to make a network connection to a computer running Windows, the sign-in process authenticates the user’s credentials.
If authentication is successful, the process returns a SID for the user and a list of SIDs for the user’s security groups.
... An access token is a protected object that contains information about the identity and user rights that are associated with a user account.
➡ When a user signs in interactively or tries to make a network connection to a computer running Windows, the sign-in process authenticates the user’s credentials.
If authentication is successful, the process returns a SID for the user and a list of SIDs for the user’s security groups.  A figure:
A figure: 














 Here, the product manager comes in. They are responsible for planning and maintaining the product, whether physical or virtual, throughout its lifecycle.
Here, the product manager comes in. They are responsible for planning and maintaining the product, whether physical or virtual, throughout its lifecycle. 
 Point-of-Use Provider Routing
Point-of-Use Provider Routing 

 The situation:
The situation:



 The difference between:
The difference between:








 Asking an oracle is a way to convince presumed decisions by assumptions is of all times. Ambiguity is to avoided.
Asking an oracle is a way to convince presumed decisions by assumptions is of all times. Ambiguity is to avoided.



 In engineering, Physics-based modelling often involves deriving equations, from first principles to describe the underlying physical processes.
A wind tunnel is an example of physics based modelling.
In engineering, Physics-based modelling often involves deriving equations, from first principles to describe the underlying physical processes.
A wind tunnel is an example of physics based modelling.  There are some more considerations
There are some more considerations






 🎭 For designing product quality internal two important central activities are about budget and access.
🎭 For designing product quality internal two important central activities are about budget and access.  🎭 For designing product quality internal two important central activities are about budget and access.
🎭 For designing product quality internal two important central activities are about budget and access.  🎭 For designing product delivery external two important central activities are about infrastructure and technical support.
🎭 For designing product delivery external two important central activities are about infrastructure and technical support.  🎭 For designing product quality internal two important central activities are about budget and access.
🎭 For designing product quality internal two important central activities are about budget and access. 





 🤔 In big environments there is a split by:
🤔 In big environments there is a split by:

 😉 This is the natural way of workers accepting others working in that same functional flow line.
Prerequisite culture: working in lines for a shared goal.
😉 This is the natural way of workers accepting others working in that same functional flow line.
Prerequisite culture: working in lines for a shared goal. 







 Accountabilities, roles:
Accountabilities, roles:











 In a figure, see right side.
In a figure, see right side.


 See the figure right side:
See the figure right side:








