Running portfolio security lean - complicated.
Multi tenancy and Security, Etl perfomance.
The quest work of security with ICT colleagues..
Working experiences by some controls. The SIAR cycle is there using the corners 👓, topic cycle in the center.
SIAR:
S Situation
I Initiatives
A Actions
R Realisations
🔰 lost here, than..
devops sdlc.
Progress
- 2020 week:12
- Started with blank page. (copy jst)
Contents
| Reference | Topic | Squad |
| Intro | Making work of ICT colleagues easier. | 01.01 |
| Tech (I) | Reshufflings tasks by Reorganisations. | 02.01 |
| Tech (II) | New tasks: security, context, ethical usage. | 03.01 |
| Initial tasks | Relationships identities authorisations. | 04.01 |
| Advanced tasks | Processes - Continuity, Availability - DR BCM. | 05.02 |
| Results evaluate | Evaluating results - technical. | 06.01 |
| | Words of thank to my former colleagues | 06.02 |
| Priv Access | Guidelines eg iec/iso 27002, Privileged access. | 51.01 |
| Auth at rest | Securing business applications - at rest. | 52.01 |
| Auth at transit | Securing business operations - at transit. | 53.01 |
| Save Business | Securing business logic - business data. | 54.01 |
| Aggregate PII | Eliminating PII Personal Identifiable Information. | 55.01 |
| Realisations evaluate | Evaluating realistions. | 56.01 |

Notwithstanding all reshufflings cooperation for securing business data, business logic and susbsystem was possible.
Going to the people on the floor finding the ones that set guidelines others are following is the key factor.
ACF2 hierachical, RACF groups, LAN - AD directory
The first change was removing values and hard coded logic from business applications. Defining a centralised in house build call interface (api).
Commercial tools got available.
⚙
ACF2 does an hierachical approach using the uid-string.
A well-designed UID can eliminate the need for secondary authorization IDs when they are used to group IDs for resource access, and can ensure that individual accountability is retained and performance is increased.
A UID takes advantage of masking, which lets you represent multiple characters with a single character. This feature eliminates the need to write multiple rules to cover similar users.
⚠ Quality: dependency on a well designed UID-string naming convention.
⚙
RACF is using groups.
The group concept is very flexible; a RACF group can be equated with almost any logical entity, such as a project, department, application, service bureau customer, operations group, or systems group.
.
As a RACF user, you belong to a default group. You are automatically connected to that group when you log on. However you may be defined to more than one group.
⚠ Quality: dependency on a well designed default group naming convention.
No matter what commercial product is used it will lacking support for complex situations eg in signing sensitive approvals for multiple persons on dedicated conditions.
There was a conversion changing these tools.
⚙
LAN AD is using groups.
Active Directory uses a structured data store as the basis for a logical, hierarchical organization of directory information.
. It is very similar to LDAP. However the technical realisation of authorisation is decoupled.
⚠ Quality: dependency on a well designed directory naming convention.
Securing middelware tools using naming conventions (at rest)
Just define a technical ownership by a dedicated admin account when access rights are controlled by that dedicated admin account.
With this building block all what is needed for installing and running middelware -tools- is complete
⚖ 😉 By restricted admin accounts, security is easy implemented compliant.
😱 I never got understood by the responsible accountable ones why all segregations using dedicated accounts is mandatory by regulations.

Users of any kind including ICT staff once were not allowed to operate machines. Operators did have the exclusive rights to do that.
This all changed when terminals became normal at the office. A new role at ICT.
Ethics conduct code
A new kind of attitude is important for this role. It did not have a place before because the hierachical management were able to fullfill these tasks.
The latest development wiht the GDPR is the obligation to have a DPO (Data Protection Officer) in place, independent advice of management, when personal data is involved.
From
ACFE Association of Certified Fraud examiners. 👓 a code of conduct:
- Thereafter, they must exemplify the highest moral and ethical standards and must agree to abide by the bylaws - and the Code of Professional Ethics.
- - shall, at all times, demonstrate a commitment to professionalism and diligence in the performance of his or her duties.
- - shall not engage in any illegal or unethical conduct, or any activity which would constitute a conflict of interest.
- - shall, at all times, exhibit the highest level of integrity in the performance of all professional assignments and
will accept only assignments for which there is reasonable expectation that the assignment will be completed with professional competence.
- - will comply with lawful orders of the courts and will testify to matters truthfully and without bias or prejudice.
- - , in conducting examinations, will obtain evidence or other documentation to establish a reasonable basis for any opinion rendered.
No opinion shall be expressed regarding the guilt or innocence of any person or party.
- - shall not reveal any confidential information obtained during a professional engagement without proper authorization.
- - will reveal all material matters discovered during the course of an examination which, if omitted, could cause a distortion of the facts.
- - shall continually strive to increase the competence and effectiveness of professional services performed under his or her direction.
Defining roles for activities
When the work, activities, of a business process are clear the needed level in segregation in:
- duties - in what level a person is not allowed to do the combination of tasks
- tasks - in what level a person should use different accounts for a task
- activity attributes - under what kind of conditions a task is done
Knowing and describing the business process is required. There are more reasons like Accounting, the GDPR, it is becoming more and more mandatory for having it well described.
⚖ 😉 By understanding the business process it makes more sense to set up an understandable well secured environment.
Business risks with possible impact are leading for decisions in ICT solutions..
😱 I never will understand why the responsible accountable ones make the technology leading for solutions instead of evaluating he business process.

Building up an automated ICT environment converting from the hollerith methods, analyzing modelling te relationships on what somebody was doing for tasks and how his work annd taks could done in a secure way, was a normal activity.
Role based Access Control, Attributes
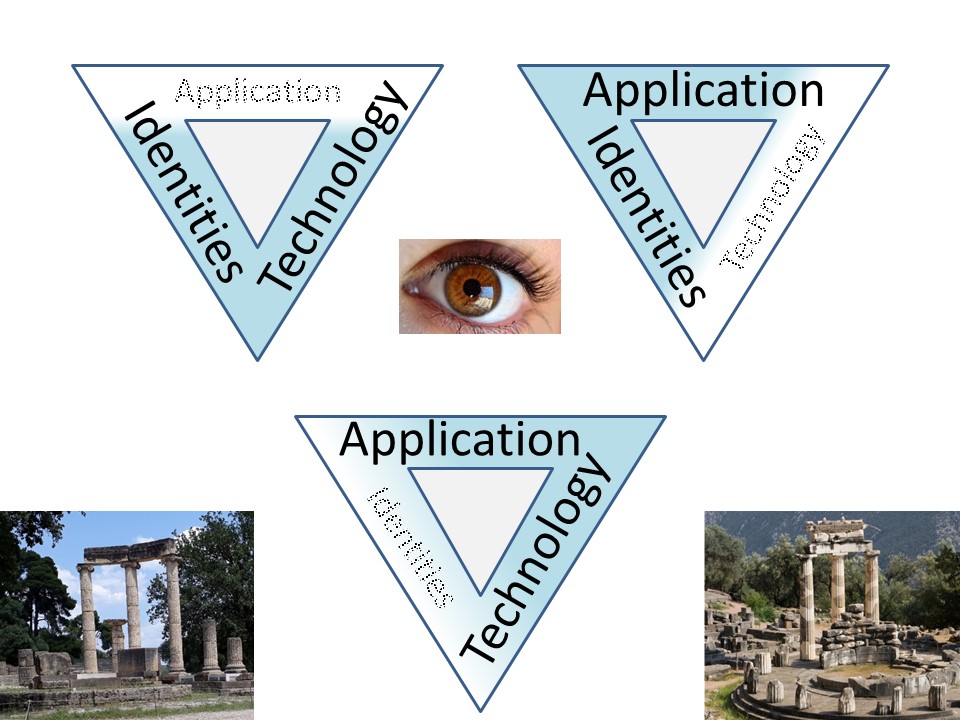
The relationships and model is by a triangle of involved parties.
- Human resources, defining who is working where doing tasks for (bu)
- Business departments doing tasks defined for the organisation
- ICT, Technology supporint the business.
In this triangle confusion misperception and lack in cooperation is easy to rise.
In a figure:
Even more confusing is that in this triangle by responablities there are at least four technical subjects to manage.
- Identities, not only the personal ones but alos non personal technicals.
- Group identities for decoupling the personal dependicies
- Authorisations for business processes.
- Authorisations for technical processes.
Knowing and describing the business process is required. Knowing depencies from business processed to technical realisations and knowing how the technical realisation is functional working also are required.
⚖ 😉 Only by understanding those three involved parties an four technical views an understandable well secured environment can get modeled.
Business risks with possible impact are leading for decisions in ICT solutions..
😱 I never will understand why the responsible accountable ones made the technology leading only managed by HR staff for running all this business and technical challenges.

Business continuity is not only about having a well secured physical an logical environment but also: what to do when some things are going terrible wrong.
Losing the physical access or the logical can stop all processes for an organisation.
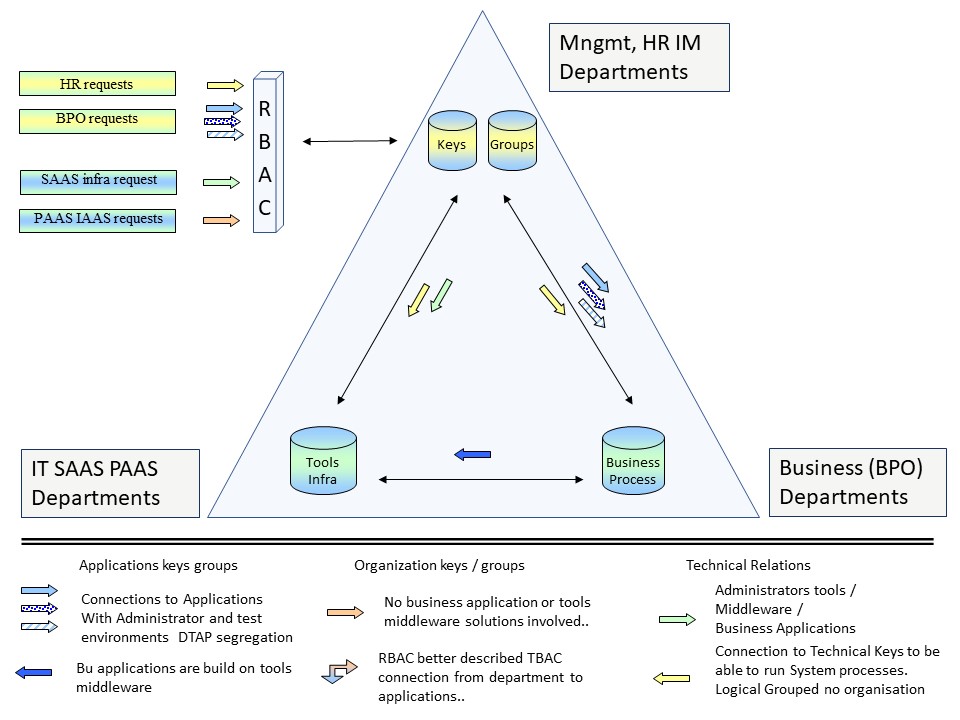
Generic process flow model
Every process has some input and output / results to deliver. For processing
The components at rest and the information in transit going through several steps.
There is a important difference at D Develop being the only line developing new logic. The Test Acceptance Production (operations) very similar.
In a figure:
A shadow Production or Acceptance can act as fall back for the Production line when not sharing critical components.
Hardware as physical component is very often shared by having it in a datacentre.
✅ The classic DR, Disaster Recovery, focus on recovery of losing physicals.
Aside the physical access losing the logical information is a risk. It could happen by accident unintended but also intended by a bad person.
Ransomware is an incarnation of intended logical destruction.
✅ The classic BR, Backup Recovery, focus on recovery restoring logical content.
Availability mitigations
Having those recovery strategies for physical and logical components, they are costly and you never really want to use them.
😱 I never will understand why the responsible accountable ones are doing cost savings by ignoring recovery strategies.
Buying some expensive physical components for physical hot stand by and than doing a claim logical content recovery is not necessary anymore, is not understanding risks.
DR exercises for physical recovery, only successful after several attempts are a fail.
⚖ 😉 By understanding the business impact, acceptable choices are possible. Why would you need development for a limited time when doing a technical migration?

Assuming this subject is the most easy one, easy as not clearly visible what is going on, is terrible misleading.
Putting all topics in a line for shared documentation, this was the last one I did. The cause: hidden complexity an dependicies.
Concepts & practical knowledge
My first mistake 🚧 was wiht JST. It was not technical solutions that were important, but far more important was the impact it had on the work done by my users.
The release management, versioning 🚧 was a follow up associated wiht JST. The same mistake made again. It is not the technology but the impact it has on the work of the ones using it.
For data / information, big data analytics, data modelling 🚧 it is that one getting all the attention. Of cources that topic is interseting an important nor for technology but on the impact when using it well.
💡 What about this subject that is combining it all to get an accptable trustworhty robust environment? It is wat is really driving all those others things.
Words of thank to my former colleagues
There were good persons learning me how to approach some things. The uniquenes and difficulties to port is still something to share for improvements.
A few names:
Not always unhappy by what is going on

this topic ends here. back to devops sdlc
👓 🔰
Implementing processes.
Guidelines eg iec/iso 27002, Privileged access.
PIM Privileged identity management
 😱
😱 Although this guidline is very clear, it is ignored by external suppliers and not verified by internal and external audits.
Unnecessay using shared service accounts introducing lack of auditablity lack of good secured segreagation of duties.
This is what I got into when the merging of companies went into an ever growing bigger organisation. Never again got into an understandable situation.
⚖ 😉 What I learned is that some guys were there to explain the requiements and having an open mindset to do it in a more correct way.
PIM PAM privileged access, easy rebuild a system)
Interesting isolating of high privileged access having the goal of an easy rebuilding the operational machines for normal users.
Privileged Access Management keeps administrative access separate from day-to-day user accounts.
PAM pop, principles of operation (microsoft)
Securing business applications - at rest.
The Technology, Identities triangle for Business applications

Identities defined by technology, ⬅
💣 forgetting the functionality goal in business applications.
Defining identities at applications, ⬅
💣 failing to have generic technology supporting automated definitions.
Getting technology for applications, ⬅
💣 forgetting how identities get their functionality in business applications.
Missing the goal of secure business applications
The usual approach is having identities defined initiated by the human resources department.
Some technical tool in place for granting "roles".
⚖ 🤔 The usual result: a lot of gaps in having well secured business applications.
Defining identities to licenses for tooling
SAM, Software Asset Management, has the goal for knowing what tools by who are used and how much that usage is.
limiting the number of licenses can save a lot of money. Doing effort for SAM will cost money, there is a trade off.
This is in contradictions of everyone on an department giving the same tools in the idea that the department is the business process role of a person.
Defining identities: DBMS - Metadata
Lacking central security management options every system has to solve that in the own technical way.
- The Operating System, OS, should be logical the central security of all.
- A DBMS, a lot similarities with an OS, claims being the central security of all.
- A technical application like SAS positions itself being central security of all.
😱 The result is a chaotic situation having no central security insight no central monitoring at all.
This is what I got into when the merging of companies went into an ever growing bigger organisation. Never again got into an understandable situation.
The claim of a generic technology for a single business application
Words are often not covering the intentions and meaning in the given context.
Having a business using something generic as an office tool, text processing, or terminal emulator, than the department running that business application can act as the solely one of that generic tool.
This misperception is caused by an unclear definition of the word "application".
This misperception escalates when internal cost-accounting is done with no vision of what business logic and what generic tools are.
It doesn´t help either when suppliers are naming their generic tools as "the applications".
🤔 The marvellous quotation of a desktop migration: "We installed the office suite, applications are done." It was done at the moment of outsourcing the desktop.
The real situation: several hundreds of technical applications and business applications to be done for the migration. For each doing a repackaging traject.
Goal: managed desktops.
Securing business operations - at transit.
The triangle Opeations Technology, Business Algorithms
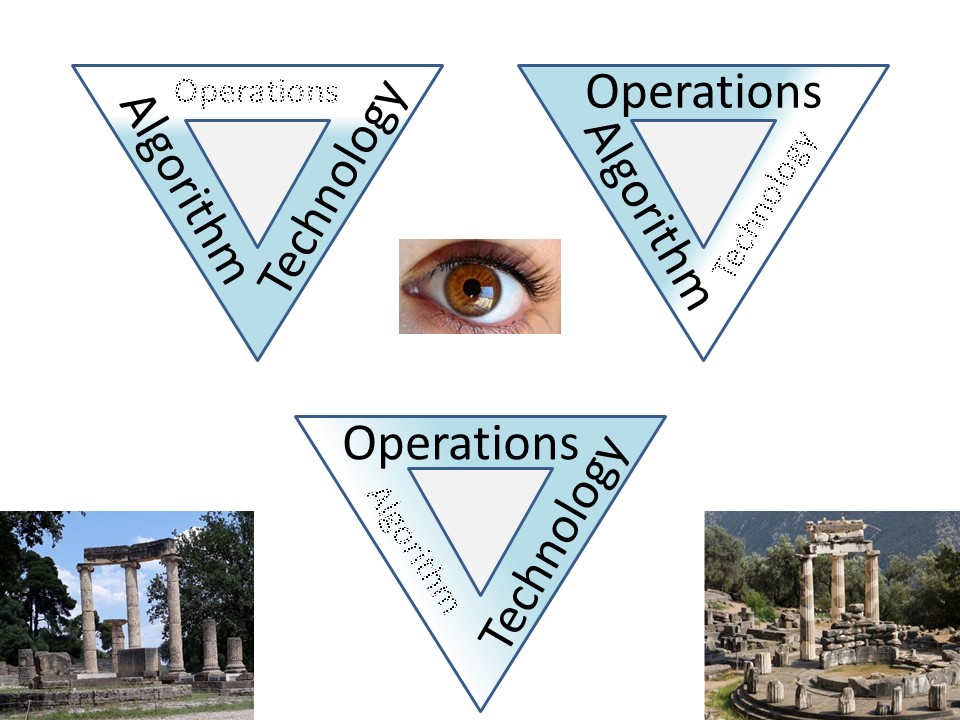
Having technology and algorithms, ⬅
💣 forgetting how to run those operational well secured.
Defining algorithms run operational, ⬅
💣 failing to have well selected appropiated generic technology.
Getting technology for operations, ⬅
💣 forgetting the goal of algorithms in business applications.
Missing the goal of secured operations
The usual approach is having operations done not managed, not controllled, executed by a limited number of operational staff persons.
⚖ 🤔 The usual result is a lot of gaps knowing what is going on at operations. The escalations of obvious wrong situations being the management approach.
Management could feel very happy with this, by seeing indispensable and important with all those escalations. There is a lot of attention going to escalations.
My personal attitude is avoiding escalations as much as possible.
Delivering results, printed output
Printed ouput is a very classic method. Once upon a time it was printed at the local data center.
With cheap printers placed at printer corners the indication of "local" changed from controlled at the datacenter to a remote uncontrolled location.
😱 Outsourcing physical printing and having the safety controls for wrong print instructions not going along with that wnet into wrong prints going out external.
Why those safety controls were missed? They were based on the trust on the local presence of motivated internal persons. Outsourcing wihtout noticing the impact.
The oldest way of the physical distribution where:
- Opening an almost public accesable cabin
- Processed into envelops by the post office & mail delivery department.
🤔 Avoiding multiple adresses printed, using window envelops, avoided any option in sending to wrong persons.
Only when multiple prints went into a single envelop resulted in a problem. Recent cases in sending mail to the wrong person is a signal to have forgotten these save appraoch.
Delivering results, service bus, file transfers
The servicebus file-transfer
- Isolated secured multi tenancy decoupling points are needed for receiving and sending information.
- Multiple tools in technology indicated as middelware are sharing the same machine.
- A technical application like SAS positions itself being central security of all.
⚖ 🤔 The usual result is a lot of gaps knowing what is going on at operations. The escalations of obvious wrong situations being the management approach.
Other procedures, web, api´s - DMZ
Isolating the most sensitive information from generic access is isolation that from the web using nested api´s putting machines in an isoalted area. The isolatedarea indicated as the DMZ.
⚖ 😉 Discussing these kind of requirments and solutions is not usual.
Securing business logic - business data.
Production information of an organisation.
This is the normal approach in operational environment: only connecting information, data, at the same stage in the development test production life cycle.
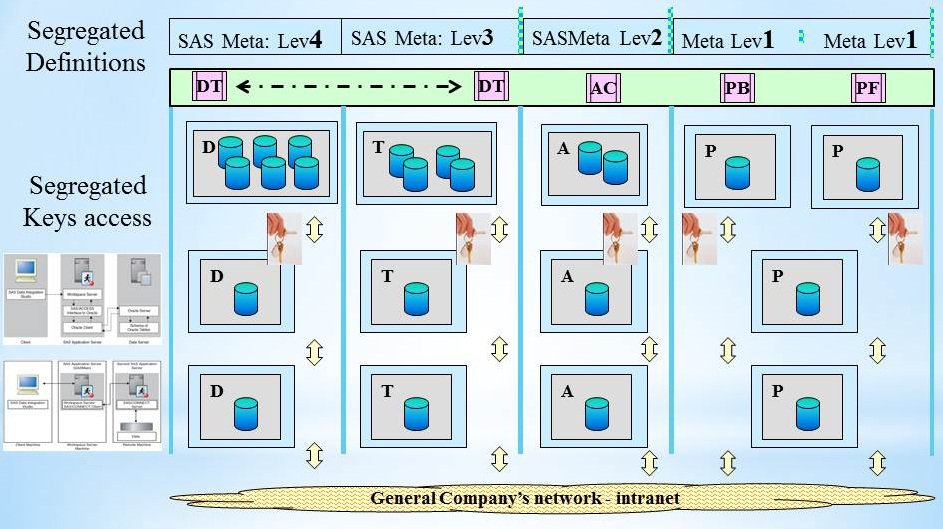
Never crossing the wall of isolation build for data / information.
Doing this by a full network segregation will cause serious trouble.
There are exceptions that will cross those orders meant for data / information.
😱 Stating an administrator of some middleware tool should solve that without any coöperation from the operating system (OS) level, escalated several times.
The result: not good acceptable compliant solutions.
Release Management for business applications classic
This is the normal approach for developping software, business logic: Using operational production versions of that logic to create new better versions.
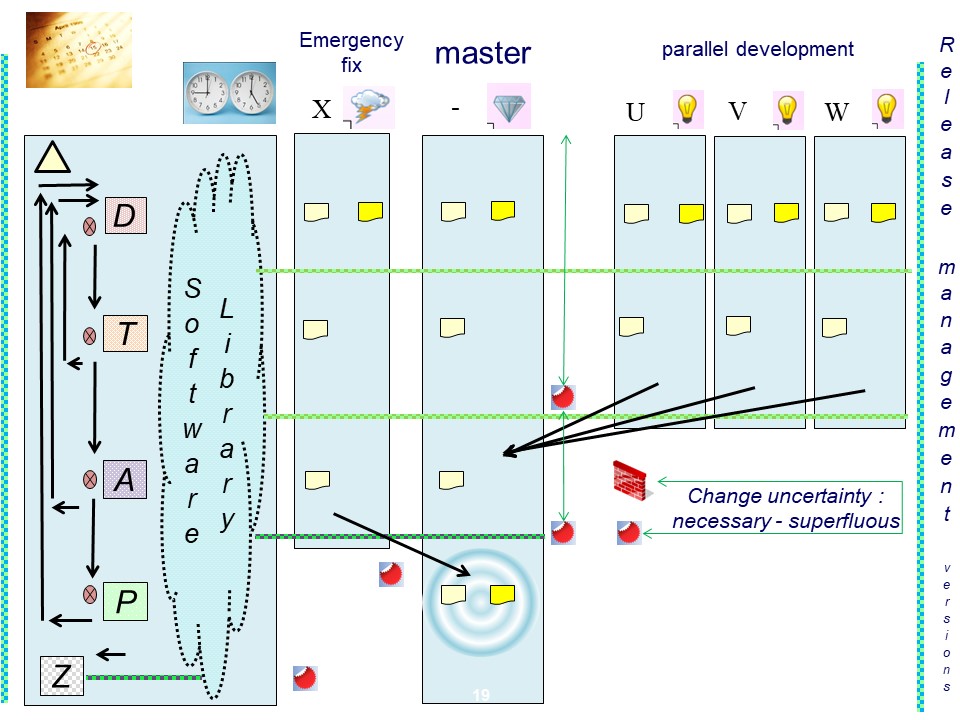
Releasing artefacts needs them passing the wall of isolation build for information / data.
Use of a software library, a copy of the production version is needed, for enabling the developement and test environments.
😱 Stating an administrator of some middleware tool should solve the release train without coöperation from the OS support, escalated several times.
The result: not good acceptable compliant solutions.
Release Management for business applications modern
There are more exceptions that will cross those borders meant for data / information. The alc type 3 model is a result.
🎭 🤔 Going for machine learning opepational data is becoming the source for new business logic. It is allowed to be used at development.
The role of operational information / data is: source code ❗
💣 Never a connection is allowed for transfering results to another different stage. The input, role code, and output information / data lines are different.
✅ Parallel development lines for the data delivery, modelling - scoring and the data output delivery are a logical result using the alc type 3.
⚖ 🤔 The alc type 3 model is not well accepted. The mindset is on:
- classic, legacy, application development
- classic, legacy, bi reporting
- classic, legacy, dwh building
Eliminating PII Personal Identifiable Information.
Anonymization as soon as possible
For the sake of storage size and performance it was necessary to build intermediate synthetic groups for the information.
Outliers wiht all of the dirty details are not interesting when it is too long ago. Having backups to restore for a longer period covers the option for analysing a defined period.
When storage got cheap the argument became that because it was cheap keeping all those detailed information is an advantage. The question: really?
Think again when all requirements for processing PII personal identifiable information are getting more and more important.
Anonymizing using summaries in well defined synthetical groups will avoids a lot of unexplainable spurious correlations.
See figure:
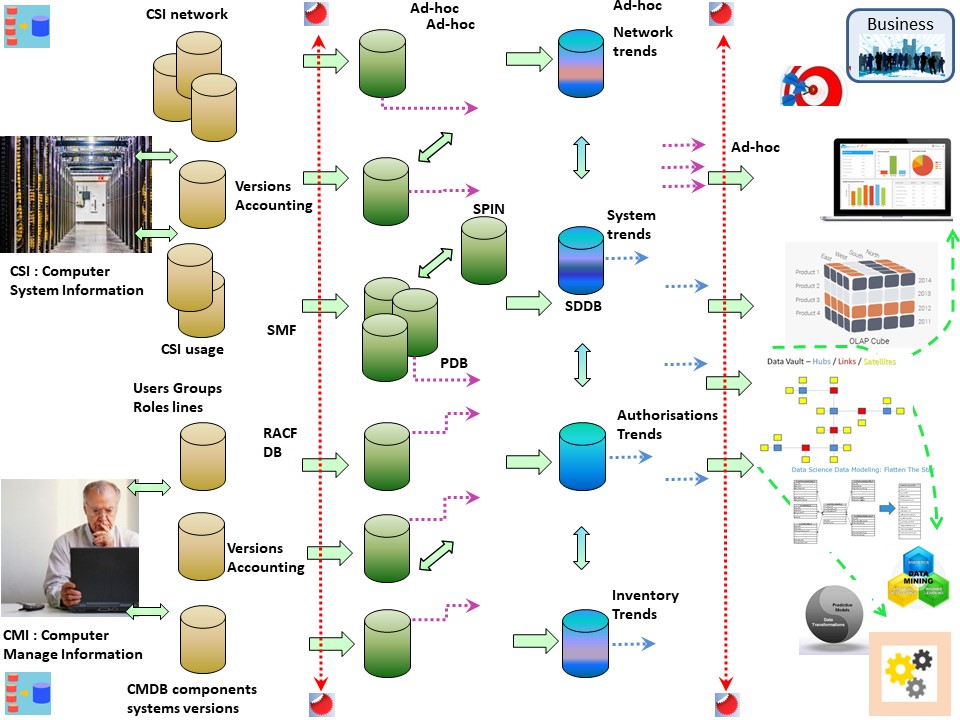
Not all possible questions that someone could imagine are easily answered with this data information summarisation.
Delivering results fast and reliable with good quality is however easier. Basic questions are in the summarisation / anonimisation.
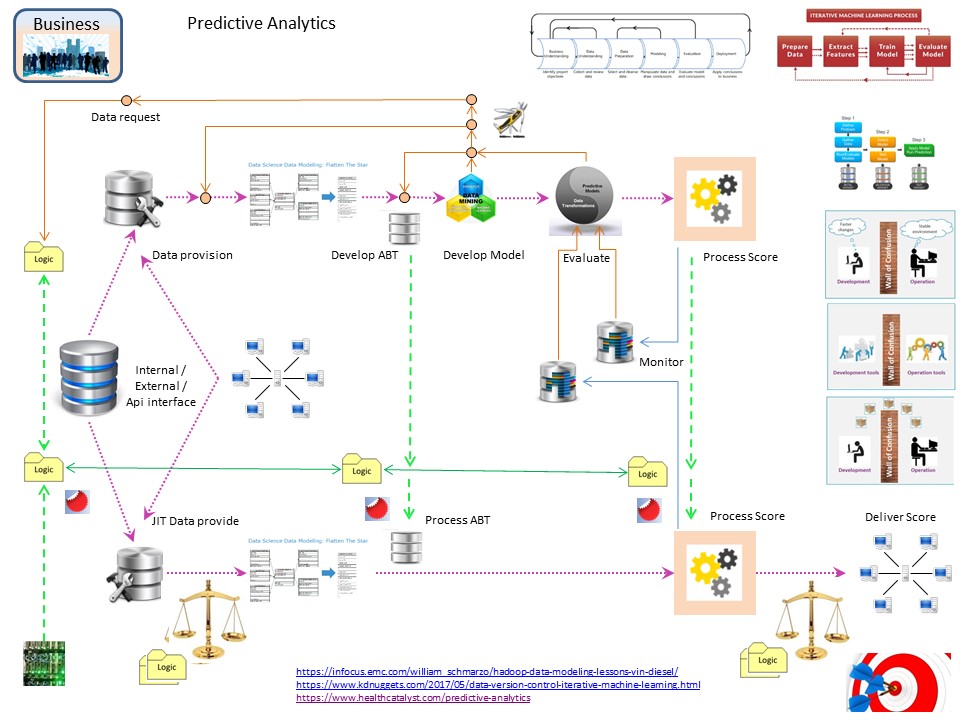
Data preparation ER (entity relation) to ABT (Analytical Base Table).
Classic coding did read the main subject, record of a fact table, joining the associated information (dimension tables, features) for deciding on that subject.
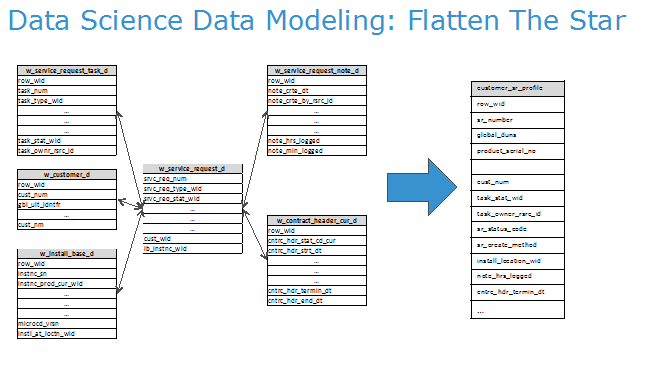
A modern machine learning projects is needing a basic table in the same approach.
See figure.
Going back to the SDLC basics it is all the same despite all new hypes.
⚖ 😉 Using the same basics solved a lot. A little bit painful that many of us don´t see these similarities.

Evaluating realisations.
Information security
The are several topics and all of them must be at sufficiënt level to have an adequate level of information security
- Securing the operational production information of an organisation.
- The Release Management process of business applications for several ALC types.
- Using Personal Identifiable Information only when necessary and preferable anonymised by doing aggregations.
- Having tooling (technical applications) set up in a way not harming in any way the business assets by vulnerabilities in the tooling.
- Having used Operating Systems set up in a way not harming in any way the business assets by vulnerabilities at the OS.
It is a never ending journey exploring what is not surely known. Doing business impact analyses for risk.
Some went went being a succes, others lost accepting change.
Not always unhappy by what is going on

Working experiences by some controls. The SIAR cycle is there using the corners 👓, topic cycle in the center.
SIAR:
S Situation
I Initiatives
A Actions
R Realisations
🔰 lost here, than..
devops sdlc.
 Working experiences by some controls. The SIAR cycle is there using the corners 👓, topic cycle in the center.
Working experiences by some controls. The SIAR cycle is there using the corners 👓, topic cycle in the center. 












