Design Meta, governing data security
Modeling the security attributes of data artifacts and objects
Securization Meta.

Metadata, what is in it?
Just having data, there are a lot of questions to answer:
📚 Information data is describing?
⚙ Relationships data elements?
🎭 Who is using data for what proces?
⚖ Inventory information being used ?
🔰 Most logical
back reference.
Contents
| Reference | Topic | Squad |
| Intro | Securization Meta. | 01.01 |
| model flow | Who has access, logical model. | 02.01 |
| model_re1-1n | Who has access, model relationships. | 03.01 |
| 4-artfct | The four basic artifact types. | 04.01 |
| complete-run | Completion to a running operational environment. | 05.01 |
| What next | Step by step, Travelling the unexplored. | 06.00 |
| | Following steps | 06.02 |

Combined pages as single topic.
👓 deep dive
, Data Proces layers
👓 describe data
,Data Administration
👓 Data Modelling
🚧 ALC type3 Security Access
🕶 ALC type3 Low code Analytics, Business (SDLC)
Progress
- 2019 week:18
- Filled in the same steps of layers as in SDLC
- Cross refernces to the SDLC area added.
- Detailed security for tools and business (hosting) to do at the devops meta area.
Who has access, logical model.
A logical model will show all involved parties, that are:
- Human resource support. delegated resposibility by line management. (data controller)
- Business applications and their usage by business departments.
- ICT being the service provider for data processing.
In a picture:
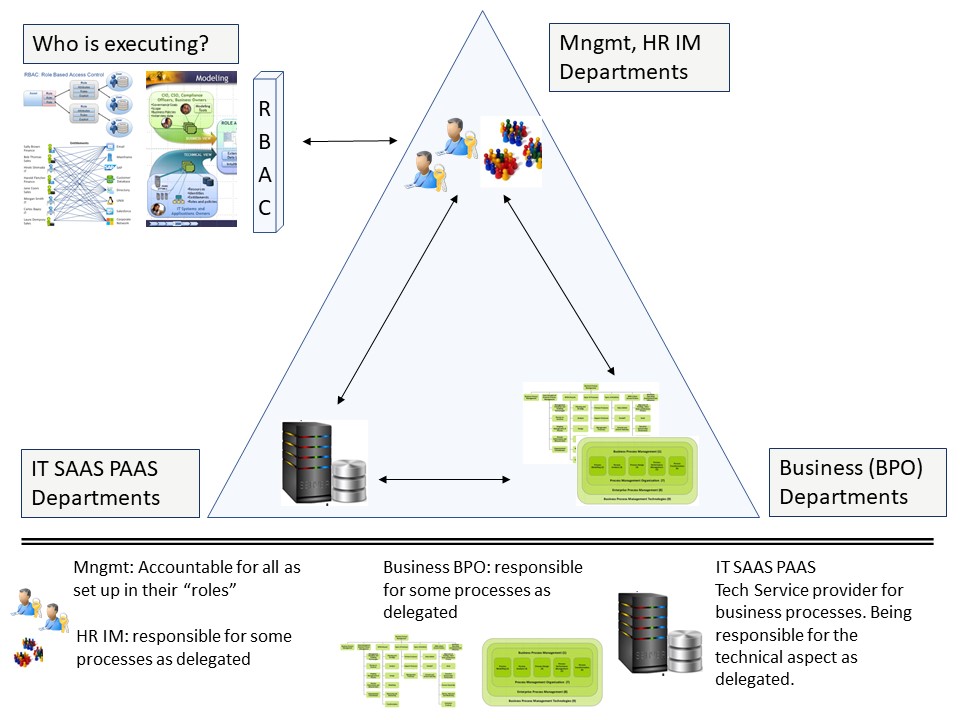
Reference partial:"Role Discovery and RBAC Design A Case study with IBM RaPM."
Replacing the symbols to more technical symbols, There are two important elements: Keys and Groups.
The picture:
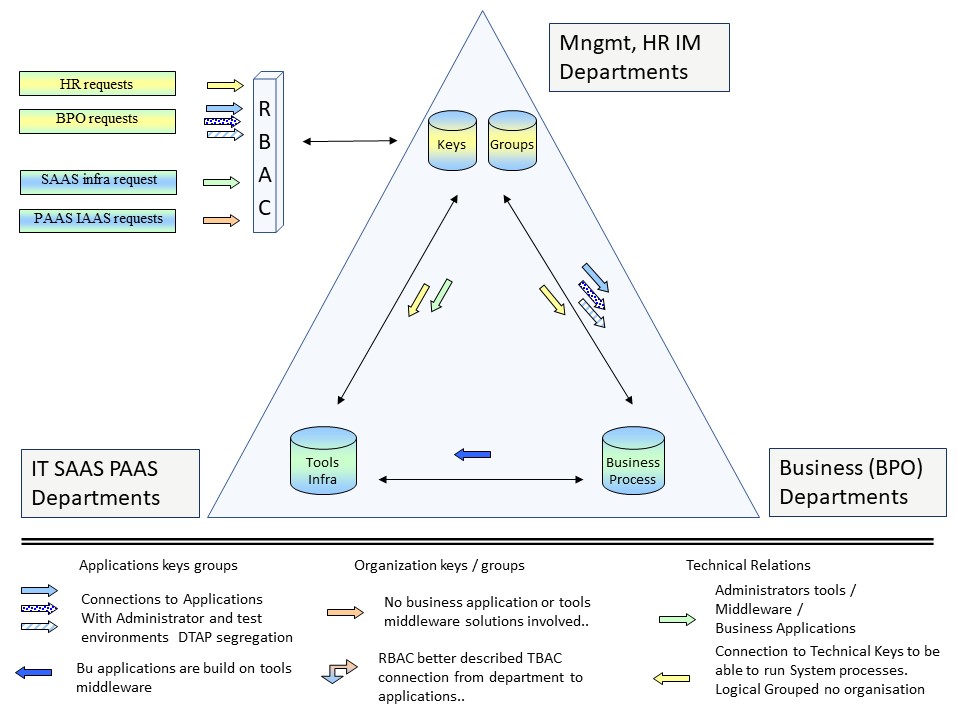
Who has access, model relationships.
Logical Relationships occurences.
Some challenging attention points for an implementation in roles.
💣 Business applications can be used by multiple business departments.
Who is responsible accountable for a business application shoud be made clear.
💣 Tools can be used by multiple business applications a 1-1* relationship.
Who is responsible accountable for a tool shoud be made clear.
💣 The usage of a key /account should be traceble to a person. Shared usage of accounts to be avoided.
A person can have multiple keys / accounts. Using high privileged rights segregations by different accounts is mandatory.
These challenges are caused by assumptions, being more simplistic, not realistic.
Logical Relationships between the four major elements.
The relationships (I Business, see picture):
- Standard: PA, user ➡ group ➡ business application
Most common and understandable
- test-accounts: NPA (non personal account) ➡ group ➡ business application
permanent at test stages (T,A) to simulate - repeatabele, predictable.
- service-accounts business app-s: groups ➡ NPA´s ➡ business application(s)
permanent at stages (DTAP) for administrations and run-time.
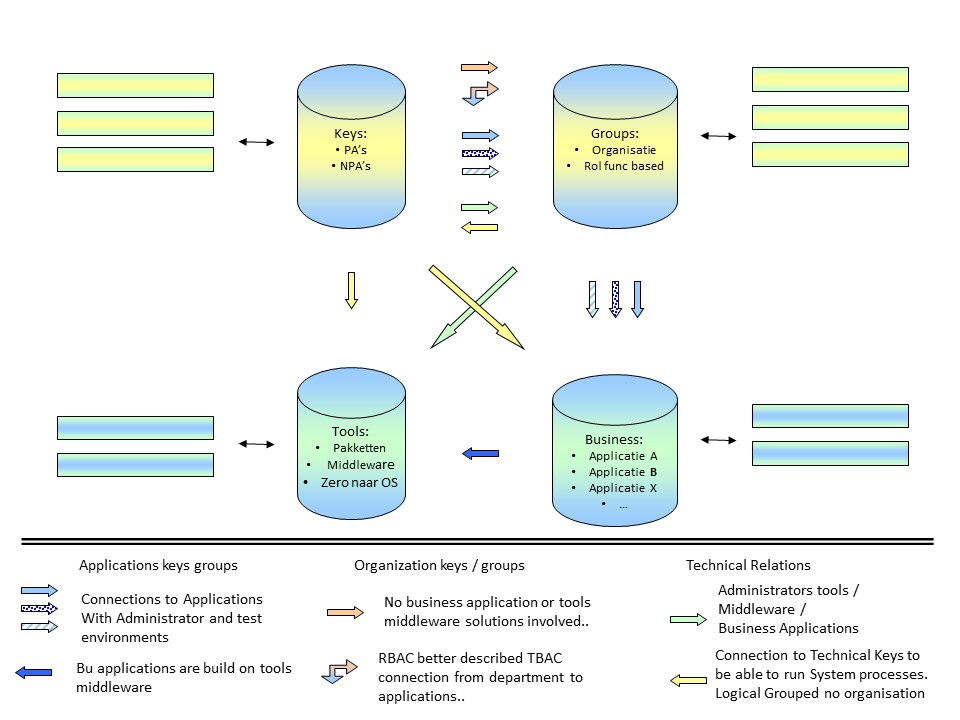
The relationships (II Technical, see picture):
- service-accounts tools: NPA´s ➡ groups ➡ tools(s)
permanent for tool administrations and run-time.
Possible additional business app relations
- Business app-s: ➡ business application(s) ➡ tools(s)
When "group member of group" not possible, repetition detailed relations.
- system-accounts: NPA´s
High privileged accounts, adminstrators and service accounts at the operating system level.
Attribute based rights keys/accounts.
Others aside keys groups could be: date / time, machine hardawre identification, geo location, used network connections, skill level, autorization level.
The four basic artifact types.
The ALC type3 (Application Life Cycle) is having four articaft types, both when developping and running (production). The picture from the design-bpm chapter:
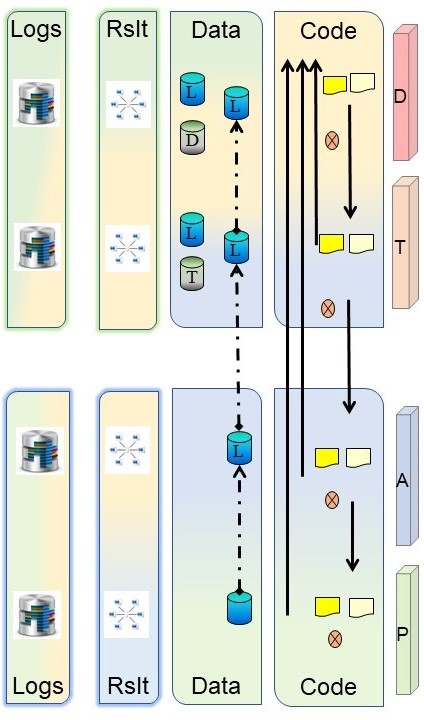
Securing the well known types Data and Code will reuslt in:
- for Npa´ss four for the code and four associated groups
- for Npa´ss four for the data and four associated groups
Having tenfolds of businessapplications, the number of npa´ss and groups increases easily above hundreds.
The results -documents- have their own requirements and implementations.
- Logging to be segregated from administration and segregated from the data and code.
- Results -documents- are possible hardcopy print, filetransfers or api´s. Every technical implementations having his own approach.
The kind of number of security defintions to manage is seen as problematic.
There is no problem in automatization with standardization.
Proposing everybody shoudl have their own infrastrcuture is moving the manageability challenge to managing all those segregated infastructure components.
In the real life logistic world, using containers moving and transporting goes the best using optimized shared cargo carriers.
An understandable structure is required. The logical security being easily understood and higly segregated is mandatory by compliancy.
Completion to a running operational environment.
The business applications ar coming into live by administrators doing the last configurations and manipulations using a schedule planning.
The service portal (desk) for the Business as delivery point.
The picture changes into:
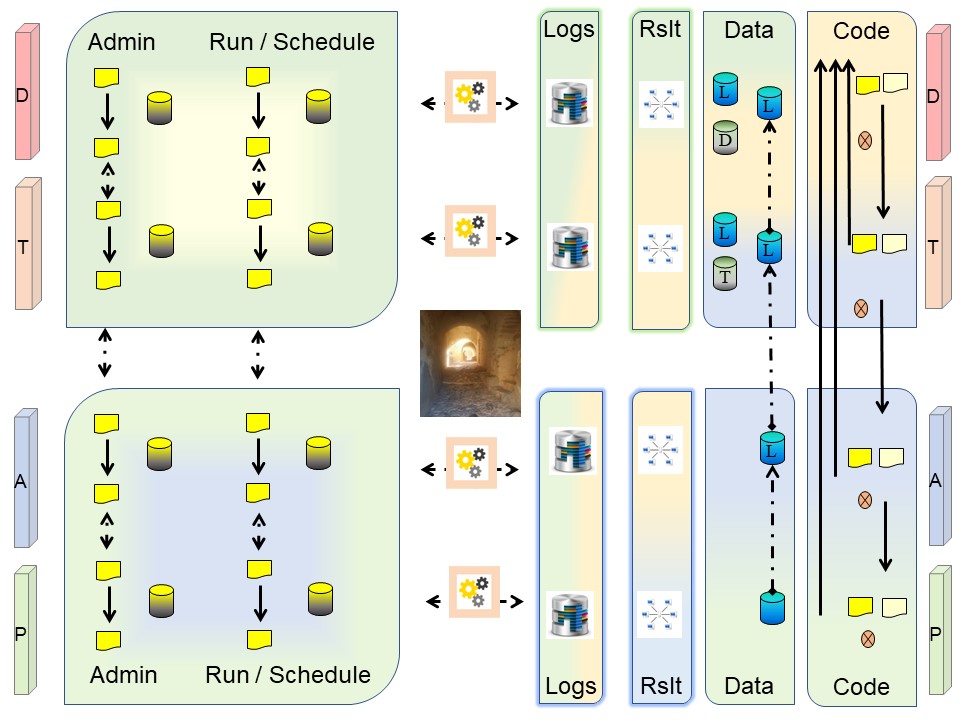
Hidden for the business are the tools and other infrastructural components. They are at the other side of the service portal(desk).
Of course these are necessary. For anay tools only validated tested ones (infrastrcuture) are used, even when only used at test (business logic).
The change in the picture for that is:
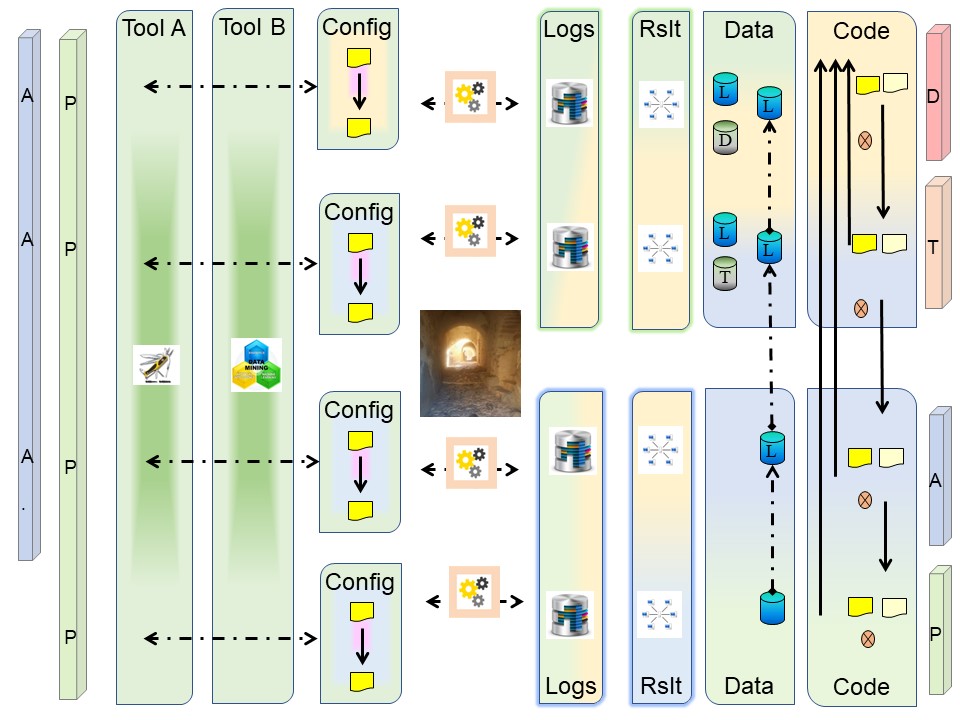

Step by step, Travelling the unexplored.
related topics.
Starting to implement technical solutions for a security goal, doesn´t bring much when the preparation on what to achieve is not done.
Considerations to do first:
- BIA Business Impact analyses.
- PIA Privacy Impact assesment.
- CIA Confidentality Integrity Availability.
Security Development Lifecycle (SDLC), System Software and the prperty Secure are all applicable.
Modeling Tool threats
To better help you formulate these kinds of pointed questions, Microsoft uses the STRIDE model, which categorizes different types of threats and simplifies the overall security conversations.
- Spoofing (Authenticity) Involves illegally accessing and then using another user´s authentication information, such as username and password.
- Tampering (Integrity) Involves the malicious modification of data. Examples include unauthorized changes made to persistent data, such as that held in a database, and the alteration of data as it flows between two computers over an open network, such as the Internet.
- Repudiation Associated (Non repudation) with users who deny performing an action without other parties having any way to prove otherwise for example, a user performs an illegal operation in a system that lacks the ability to trace the prohibited operations.
- Information Disclosure (Confidentiality) Involves the exposure of information to individuals who are not supposed to have access to it for example, the ability of users to read a file that they were not granted access to, or the ability of an intruder to read data in transit between two computers.
- Denial of Service (Availability) Denial of service (DoS) attacks deny service to valid users for example, by making a Web server temporarily unavailable or unusable. You must protect against certain types of DoS threats simply to improve system availability and reliability.
- Elevation of Privilege (Authorization) An unprivileged user gains privileged access and thereby has sufficient access to compromise or destroy the entire system. Elevation of privilege threats include those situations in which an attacker has effectively penetrated all system defenses and become part of the trusted system itself, a dangerous situation indeed.
Considerations with adjustments to as-is situations:
- Retention policies
- red - blue teams as testing approach.
- Versions used software, CMDB
- network segregations
- SOC (Security Operations Center)
- Monitoring technical loggings

Transforming processes.
Change is a the only constant factor of a journey. Never knowing for sure what is next. Changing fast is exploring where no one has gone before.
The people around ICT are a different kind of species than the ones running the business.
Understanding the business during fast transitions is another world.
Combined pages as single topic.

👓 deep dive
, Data Proces layers
👓 describe data
,Data Administration
👓 Data Modelling
✅ ALC type3 Security Access
🕶 ALC type3 Low code Analytics, Business (SDLC)
🔰 Most logical
back reference.
 Metadata, what is in it?
Just having data, there are a lot of questions to answer:
Metadata, what is in it?
Just having data, there are a lot of questions to answer:








